Last night I caught myself doing that familiar loop—checking the official pages again, half-expecting a neat new post to appear and explain the “latest” in one clean quote, even though the market almost never gives you clarity on schedule. In the last 24 hours, there still wasn’t a fresh Dusk site news update that replaces the most recent official reference point, which remains the Bridge Services Incident Notice dated January 17, 2026, and that silence is actually useful because it forces you to separate narration from evidence. When you stop waiting for a headline and look for something verifiable that doesn’t depend on anyone writing an update, the clearest short-window signal becomes contract-level movement: Etherscan surfaces the DUSK ERC-20 contract’s 24-hour transfer count, and that single number gives you a measurable view into movement and usage at the contract layer even when the official feed stays quiet.
That’s why your framing—privacy-preserving markets without sacrificing transparency on demand—hits differently when you treat it as a design constraint instead of a slogan. People argue privacy like it’s a switch, either everything public or everything hidden, but regulated markets don’t live at either extreme because confidentiality is normal while accountability is non-negotiable. The real challenge is selective disclosure: you keep sensitive details private by default, but you can still prove validity, compliance properties, or eligibility when oversight requires it, without dumping every transaction and relationship into permanent public view. “Transparency on demand” should mean structured pathways for proof, audit, and dispute resolution, not radical exposure as the default cost of participation.
This is where zero-knowledge methods stop feeling like mystique and start feeling like infrastructure logic, because they let a system answer the only question that truly matters in serious finance—can you prove you followed the rules—without forcing you to reveal everything about the underlying transaction or identity. Privacy that cannot be verified becomes a black box, and black boxes don’t scale in regulated environments, but transparency that equals permanent exposure creates its own failure mode: surveillance, competitive leakage, and the slow erosion of any realistic institutional participation. The Dusk thesis is essentially an attempt to keep the ledger verifiable while letting the market remain confidential where it should be, and only revealing what is necessary, to the right party, at the right time.
If you want to judge whether a project understands that balance, you don’t only read the vision; you watch how it behaves when the operational edges get messy. The January 17, 2026 incident notice matters precisely because it isn’t glamorous, and because it forces the team to communicate in the language of containment rather than in the language of features. The notice describes unusual activity tied to a team-managed wallet used in bridge operations, followed by practical responses like pausing bridge services, disabling and recycling related addresses, and adding a Web Wallet mitigation through a recipient blocklist that aims to prevent transfers to known dangerous addresses and warn users before submission, while also drawing a clear boundary around the core protocol by stating it was not a protocol-level issue on DuskDS and that the main network continued operating. Even the sequencing tells you something: the bridge remains closed pending review, with reopening tied to resuming the DuskEVM launch path, which reads less like “PR” and more like infrastructure discipline.
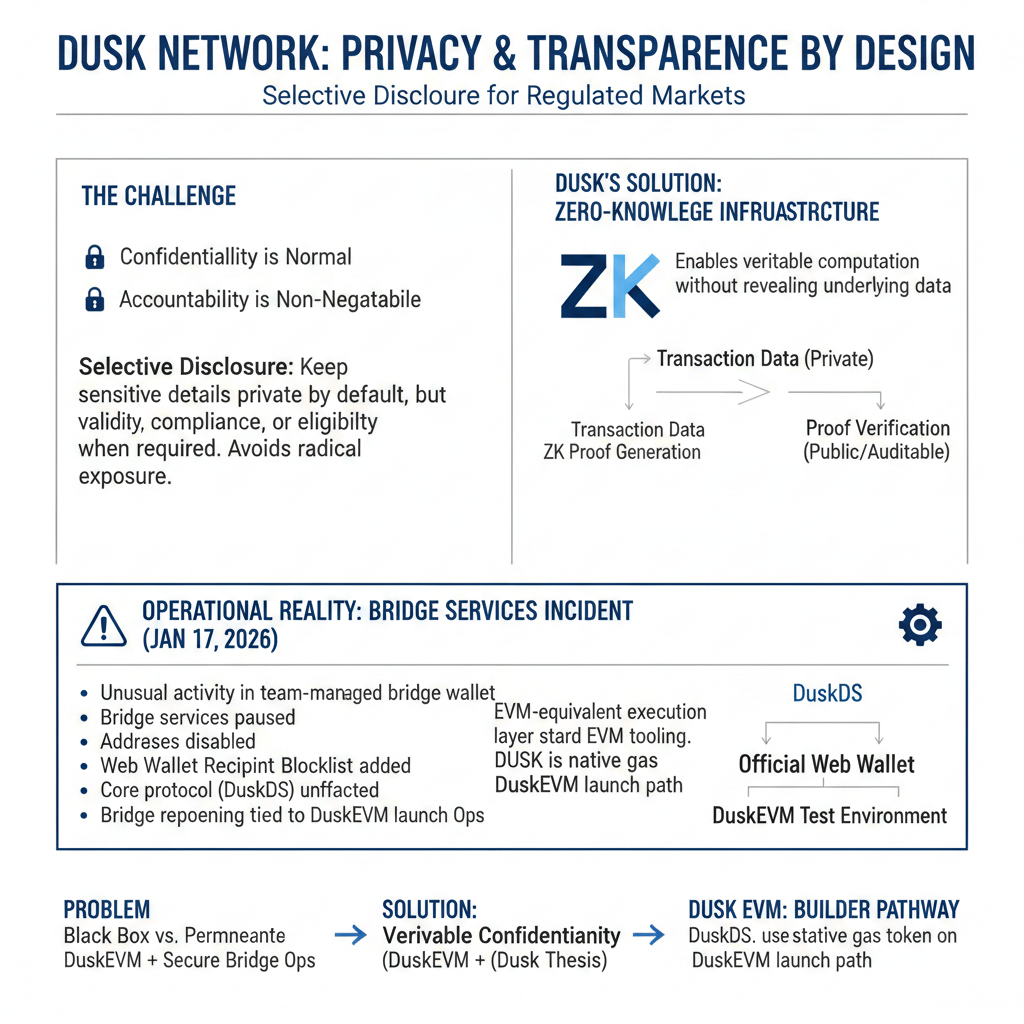
That builder pathway is important because privacy-first networks often fail not due to lack of ambition, but due to developer reality, where teams need familiar tools and clear execution environments to ship. Dusk’s documentation positions DuskEVM as an EVM-equivalent execution layer that inherits security, consensus, and settlement guarantees from DuskDS, which is a practical way to let developers build using standard EVM tooling while the broader architecture still aims at compliance-oriented market design. The bridge guide makes this tangible by describing a flow from DuskDS into a DuskEVM test environment via the official Web Wallet, and once bridged, DUSK becomes the native gas token on DuskEVM, which turns the idea from theory into something operational. When you add the wider bridging and migration context—how token representations like ERC-20 or BEP-20 relate to native DUSK—you also understand why bridge operations become a sensitive corridor that needs strict process and security posture.
So the “updated” story doesn’t need to be loud to be real: the most recent official site anchor remains the January 17, 2026 bridge incident notice, while the most verifiable last-24-hours signal is the contract-level movement that Etherscan surfaces through 24-hour transfer activity. And the more I read Dusk through that lens, the more it feels like the project isn’t trying to make everything invisible, and it isn’t pretending that full public exposure equals trust; it’s trying to build markets that can be private without becoming unverifiable, and transparent when needed without turning every participant into public metadata. That’s a harder path than slogans, but it’s also the only one that looks like it could survive contact with real finance.
