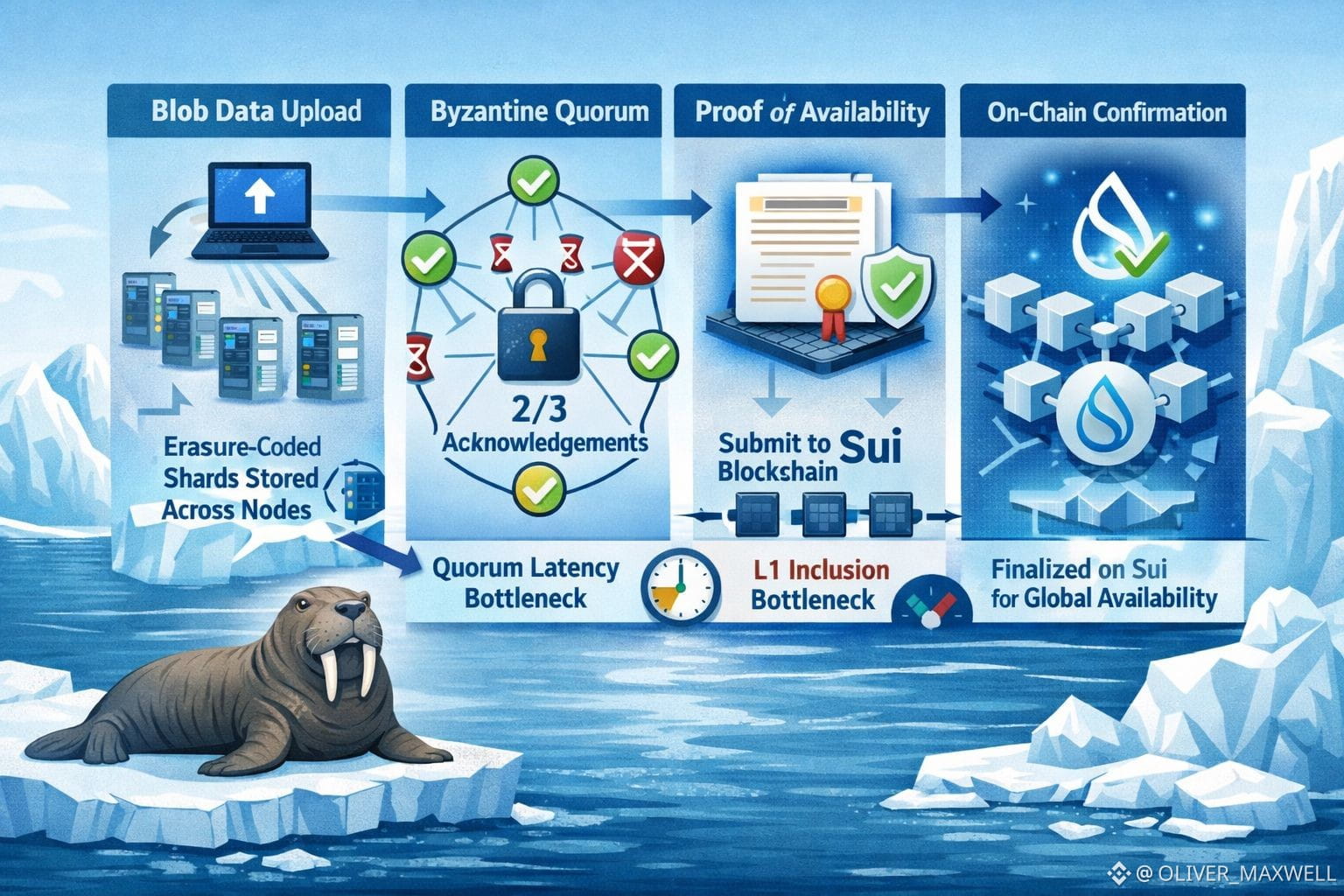
Walrus is often priced like storage is a pricing game: erasure coding lowers replication cost, blob storage makes big files practical, so the winner is whoever can push the cheapest dollars per gigabyte. I don’t buy that as the decisive constraint. The mispricing, in my view, is that Walrus is being valued like a data plane, while its scaling limit is a control-plane problem: every blob write is effectively a Byzantine quorum protocol that only becomes real once a Proof-of-Availability certificate lands on Sui.
The part that matters is not that Walrus slices a blob into shards and spreads them around. The part that matters is that the system needs to convince itself, and everyone else, that the blob is actually available. In practice that means the client is not “uploading a file,” it is coordinating an availability vote. Storage nodes acknowledge receipt and retention of their assigned sliver, you need a 2/3 threshold of those signed acknowledgements, and then you package that threshold into a Proof-of-Availability certificate whose on-chain inclusion on Sui confirms the blob is globally committed as available.
Once you look at it that way, the bottleneck stops being disk and bandwidth and starts being the coordination drag of quorum collection plus L1 inclusion. Quorum latency shows up where you are waiting to reach 2/3 acknowledgements, and the tail dominates the user experience because the slowest responses you still need determine when the certificate can be formed. In a Byzantine setting you don’t get to hand-wave stragglers away, because distinguishing “slow” from “faulty” is exactly the ambiguity adversaries exploit. So you tune timeouts, retries, and committee composition to preserve safety, and those choices show up as write confirmation time. You can make the system faster by loosening timeouts or retry discipline around quorum collection, but you pay by weakening the guarantees the certificate is meant to represent.
Then you stack L1 inclusion on top of that. Even if you collect 2/3 acknowledgements quickly, the write is not final until the certificate is published and confirmed on Sui, meaning the system cannot treat the blob as globally committed and safely referenceable under the same availability guarantee before that point. That means Walrus inherits a throughput ceiling that matters under sustained writes when certificate inclusion is the gating step, and that ceiling is driven by how many certificates Sui can absorb and finalize under real load, not how much aggregate storage bandwidth Walrus has. If your mental model is “Walrus scales when we add more storage nodes,” you miss the hard dependency: adding storage capacity does not automatically add certificate finality capacity.
This is why the “cheap erasure-coded storage” narrative can be true and still not determine adoption. Erasure coding is a cost lever on the data plane. The certificate path is a coordination lever on the control plane. In systems like this, the control plane usually wins the argument because it pins the user-visible latency and the global notion of what exists. A network can have abundant storage and still feel slow and capacity-constrained if each write is gated by quorum collection and L1 confirmation.
The trade-off becomes sharp when you think about committee size. Bigger committees improve fault tolerance and, depending on design, can improve decentralization. But bigger committees also make quorum collection more expensive. You increase the number of parties who can be slow, you increase the surface area for transient failures, and you increase message overhead. The design choice is not “decentralization versus cost,” it’s “fault tolerance versus write latency.” If Walrus optimizes for faster writes by shrinking the effective committee, it can look great in a demo and then disappoint under adversarial conditions. If it optimizes for robust quorums, it can preserve its guarantees but feel slower and less elastic than people expect from a “storage network.”
The on-chain certificate step also creates a subtle product tension. Applications want to behave like storage is immediate, but Walrus introduces a probationary state where an upload can exist as data movement while still lacking the on-chain certificate that makes it globally safe to reference under the protocol’s availability guarantee. That forces an uncomfortable question: when is a write safe to treat as real? If you require the certificate to be confirmed, you’ve introduced an L1 confirmation dependency into every user write path. If you let applications treat an upload as “done” before certificate finality, you are asking developers to build around a probationary state where data might exist on some nodes but not be globally recognized as available. That might be acceptable for some workflows, but it is not the simple cloud-replacement story people tell themselves.
Under sustained load, the certificate pipeline can dominate even if the storage nodes are idle. Imagine a world where Walrus can physically ingest far more blob bandwidth than it can certify on-chain. In that world, the network is not limited by storage at all. It is limited by how quickly it can turn “I stored it” into “everyone agrees it’s stored.” That mismatch creates pressure for batching and aggregation. Batching multiple blob commitments into fewer on-chain publications can relieve L1 inclusion pressure, but it also changes the failure model: larger batches mean larger blast radius when something goes wrong, and more complicated retry logic when a subset of writes fail to reach quorum.
This is also where incentive design becomes less obvious than it looks. If the system is constrained by quorum and inclusion rather than raw storage, then the scarce resource is not disk, it’s timely participation in acknowledgements plus reliable certificate publication. That tends to reward low-latency operators with stable networking and predictable uptime. Over time, that can create an economic filter that favors data center-grade participants. People can still run nodes, but the economic weight shifts to those who can consistently be inside the fast 2/3. If you care about decentralization as more than a slogan, you should treat this as a real gravitational pull, not a hypothetical.
The dependence on Sui also has a censorship-resistance shape that is different from “data is spread across many nodes.” If certificate publication is the gate to finality, then any sustained friction at the L1 level, congestion, fee volatility, or transaction scheduling dynamics becomes a governance issue for Walrus writes. You can build around it, you can buffer, you can prioritize, but you cannot pretend it’s not there. The system is choosing to anchor availability claims to Sui’s finality. That’s a sensible trade if you want a strong global ordering and shared truth, but it is also a constraint you pay for every time you write.
If you want the most honest way to evaluate whether this is actually the bottleneck, you don’t need intuition, you need one specific falsifier. My thesis fails if public testnet benchmarks show end-to-end write confirmation latency from client submission through Sui-confirmed certificate inclusion staying effectively stable as committee size and write rate increase. Not “sometimes flat,” not “median stays okay,” but the shape that matters: the tail latency and the end-to-end time from upload start to certificate finality should not blow out as you scale load. If Walrus can keep that curve controlled, then the system has solved the core coordination problem, and the “writes are consensus” framing becomes less central.
Until that falsifier is clearly met, I think the right way to think about Walrus is that it’s selling a particular bargain: you get cheap erasure-coded storage, but you pay with a control plane that functions like availability-focused consensus. That bargain can be worth it, especially if you want strong, verifiable guarantees of availability. But it is not free, and it is not the kind of scaling story you get by simply adding more disks to the network. If you’re trying to price WAL or model adoption, the question I keep coming back to is boring but decisive: can Walrus certify blobs on-chain, at scale, without quorum collection and certificate inclusion becoming the system’s real throttle?

