Founded in 2018, @Dusk $DUSK began with a simple but ambitious brief: build a Layer 1 blockchain that speaks the language of regulated finance while keeping confidentiality and auditability side-by-side. From its start the project has pitched itself not as a general-purpose anonymity network but as a pragmatic infrastructure layer for institutions banks, custodians, token issuers and regulated markets that need to move securities, tokenized real-world assets and financial contracts on-chain without exposing sensitive business details. That institutional focus is reflected throughout the documents and messaging the team publishes: privacy is baked into the protocol as a feature for compliance, not merely a tool for hiding; at the same time the stack aims to give auditors and regulators the deterministic traces they need when appropriate.
Dusk Network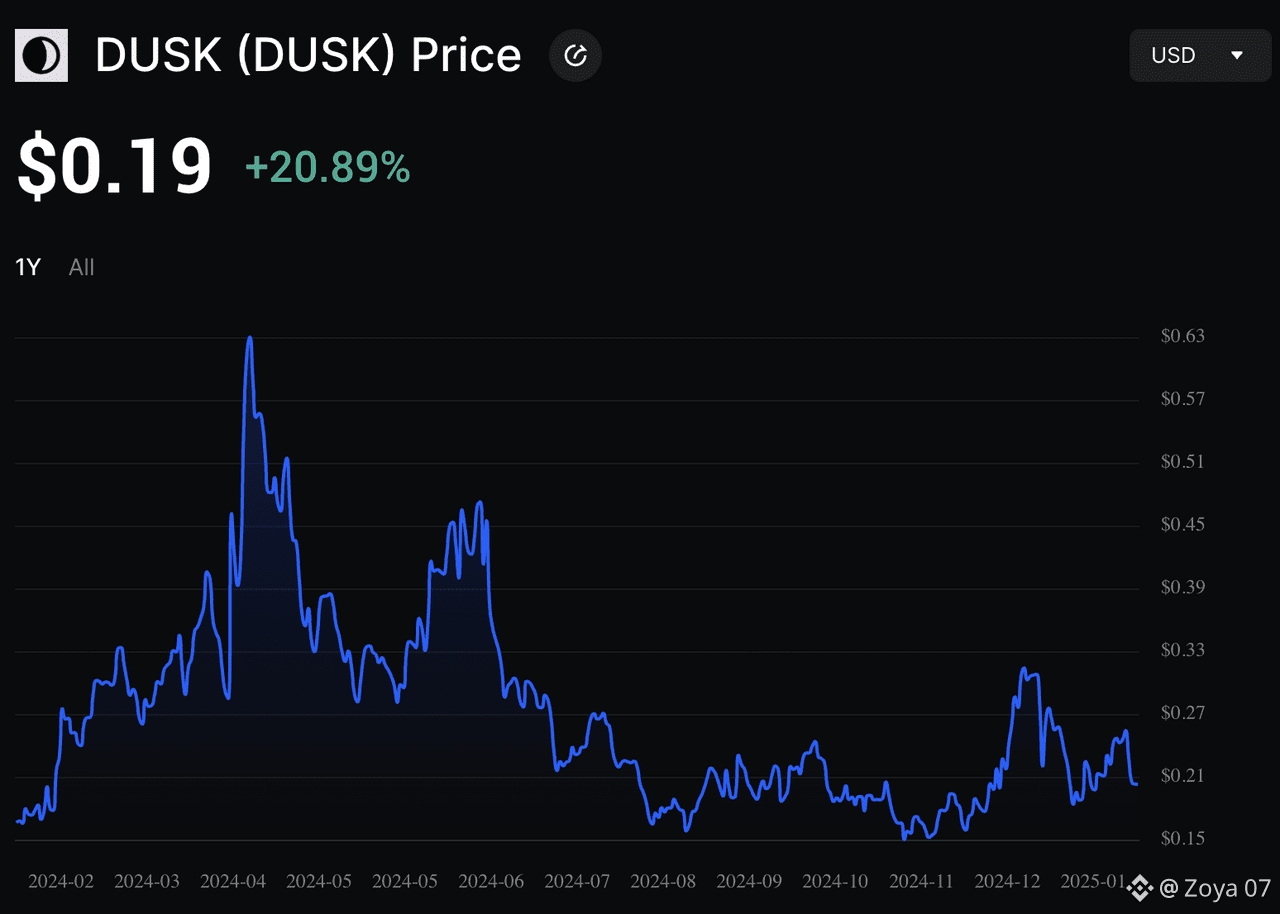
Technically, Dusk blends several complementary elements. It adopts a UTXO style transaction model and a transaction abstraction called Phoenix that supports obfuscated transfers and confidential smart contracts, allowing the network to hide amounts and inputs while still providing cryptographic proofs that let the network validate state transitions. The chain’s core components emphasize modularity: a privacy-aware transaction layer, a virtual machine and contract model designed for confidentiality, and a compact consensus layer that produces fast, deterministic finality suited to financial flows. Those design choices steer Dusk away from the general public-broadcast model used by many public chains and toward an architecture optimized for private, auditable business logic executed on a shared base layer.
Privacy in Dusk is not an afterthought implemented only at the application level; it sits at the protocol level and is repeatedly highlighted in the project’s technical materials. The whitepaper and subsequent updates describe zero-knowledge constructions, shielded contract primitives, and validator anonymity techniques that reduce attack surfaces and censorship risk for participants. Rather than exposing validator identities during block production, the protocol uses cryptographic selection and succinct attestation mechanisms so that committees can propose and ratify blocks without revealing long-term operator identities a property that helps institutions feel safer using a public infrastructure where targeted pressure on known validators would otherwise be a concern. These mechanisms are paired with tooling that enables selective transparency: a counterparty, an auditor or a regulator can be granted verifiable access to the evidence they need without the ledger becoming public knowledge. 
From the standpoint of real-world deployments, Dusk’s primary sales pitch is its suitability for compliant DeFi and the tokenization of assets that must carry off-chain legal constraints, privacy covenants, or KYC/AML requirements. Use cases the team highlights include security token issuance, private lending and settlement rails for fiat-backed instruments, confidential auctions and marketplaces for sensitive datasets, and back-office reconciliation systems where confidentiality and an auditable trail are both essential. Because confidential smart contracts can be composed and settled on a deterministic L1, Dusk positions itself as a foundation where institutional workflows can be expressed on chain while preserving operational confidentiality for example, by exposing only cryptographic commitments and proofs on the public ledger while the sensitive inputs remain shielde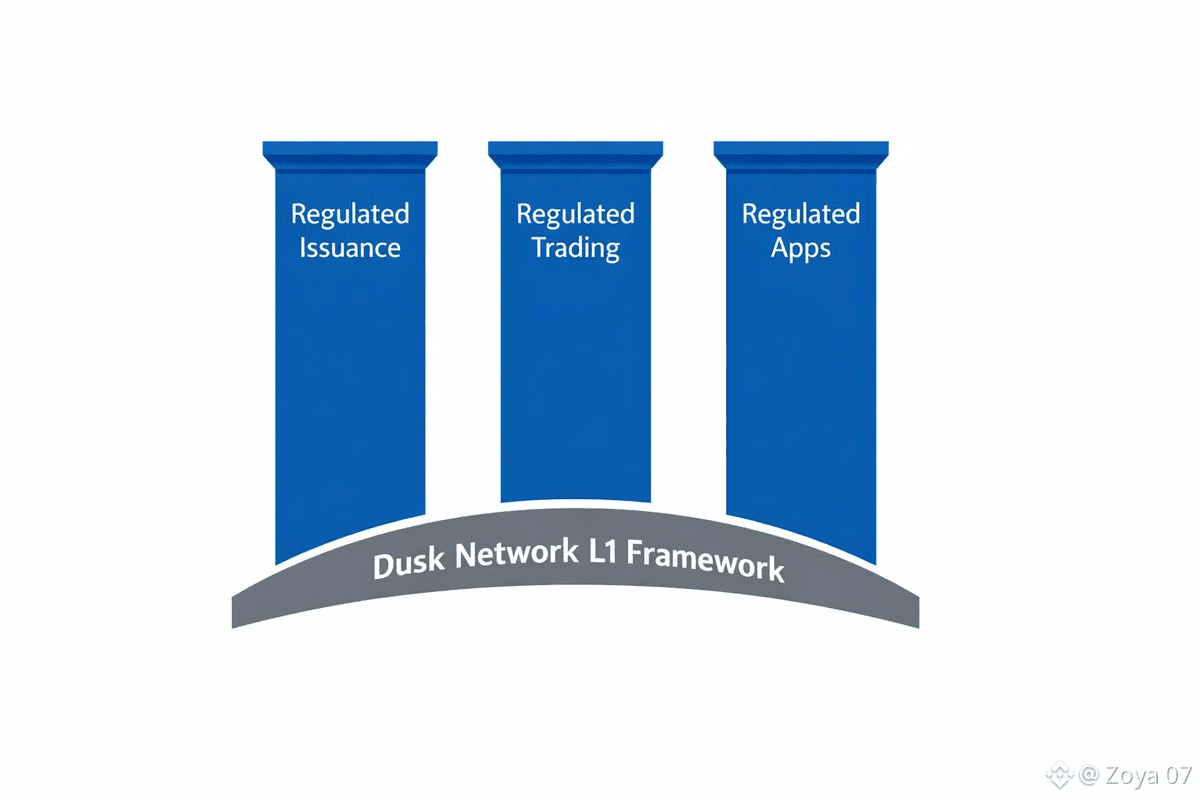
The project has evolved: the original whitepaper (and its technical primitives) formed a base that the team has iterated on, releasing updated technical documentation and a refreshed whitepaper that reflects changes to the stack and product roadmap. That continued work shows up in public documentation describing consensus refinements and implementation details for succinct attestation and provisioner/validator roles. Practically this means Dusk has moved beyond theoretical designs toward concrete engineering milestones improved VM semantics for confidential contracts, refined committee selection, and clearer operator role definitions all intended to make the network operable by service providers and financial institutions. Those updates also underscore that, while the protocol provides powerful privacy guarantees, integrating it into regulated workflows requires careful policy and tooling decisions around who gets selective disclosure and how on-chain proofs map to off-chain legal processes.
No infrastructure platform is risk-free, and Dusk is no exception. The cryptography that enables confidentiality is complex and must be audited and implemented precisely; selective disclosure and compliance tooling add operational surface area; and adoption depends on a healthy ecosystem of custodians, market makers and legal frameworks that trust the proofs Dusk provides. Moreover, token economics, validator decentralization and exchange liquidity affect how attractive the network will look to institutions evaluating production readiness. That said, Dusk’s combination of protocol-level privacy, a transaction model built for obfuscation, and a clear focus on regulated finance gives it a distinct place in the market: it is neither a fully permissioned private ledger nor a general anonymity coin, but a middle path aimed at bringing conventional financial arrangements on-chain while preserving the confidentiality those arrangements often require.
If you’d like, I can turn this into a shorter explainer thread for social media, extract a one-page technical cheat sheet that highlights Phoenix, succinct attestation and selective disclosure workflows, or draft a sample compliant-by-design smart contract flow showing how an issuer, custodian and regulator would interact on Dusk. Tell me which format you want and I’ll produce it directly.@Dusk #Dusk $DUSK #dusk
