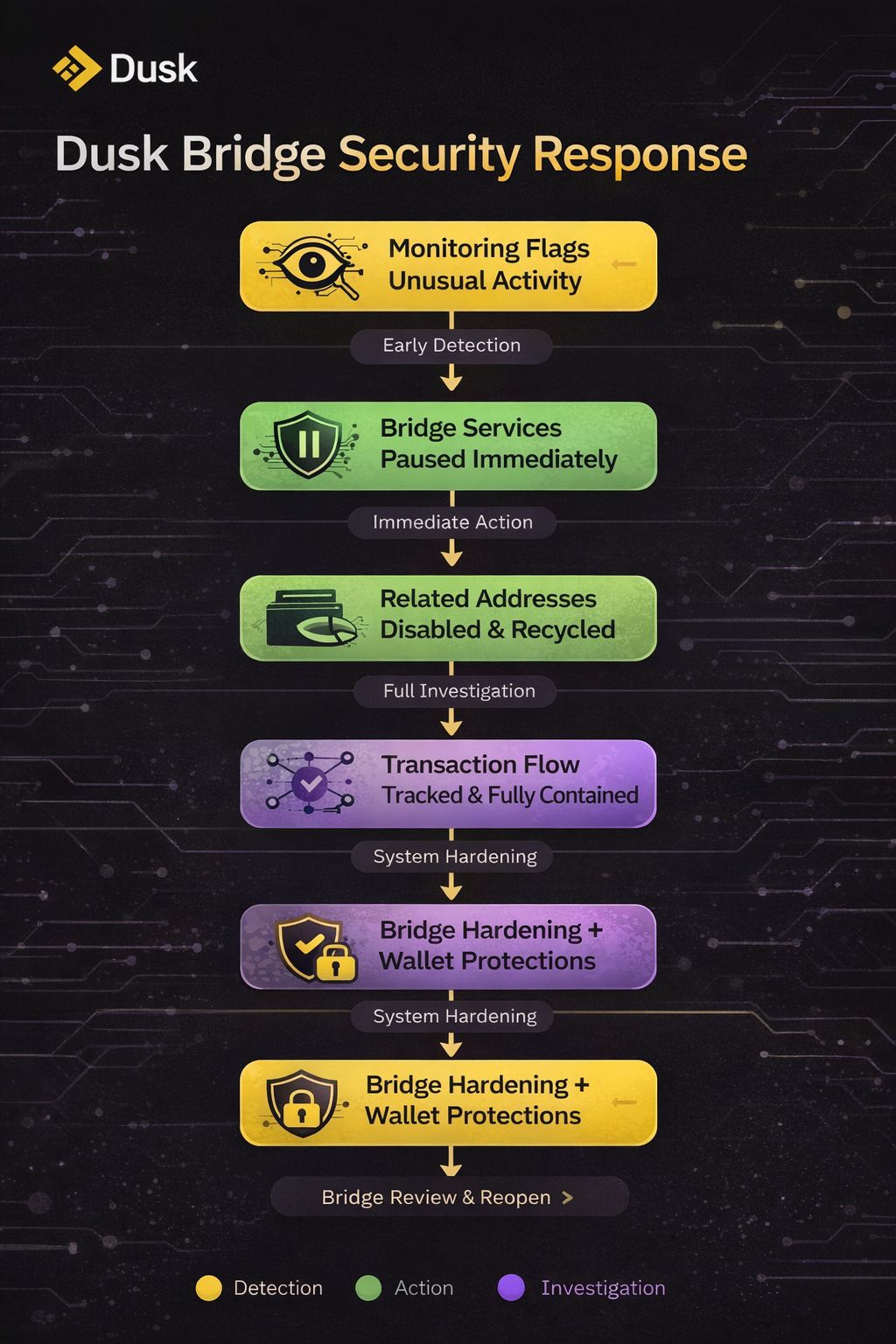
In decentralized systems, security is not about claiming perfection — it’s about how fast and responsibly a network reacts when something looks off. Over the past few days, Dusk Network demonstrated exactly that approach during a precautionary bridge security response.
Dusk’s internal monitoring systems detected unusual behavior connected to an operational wallet used for bridge-related activity. Importantly, this was not a protocol-level issue, and it did not affect the Dusk mainnet or the long-term architecture of the network. Still, the team treated the signal as security-critical and acted immediately.
As a precaution, bridge services were temporarily paused to prevent any further activity while the situation was assessed. A limited number of related addresses were disabled and recycled, ensuring that potential risk could not spread. During the investigation window, only a small number of transactions were identified, and based on all available data and confirmations, no user funds were impacted.
When part of the transaction flow touched centralized infrastructure, the Dusk team coordinated directly with external partners to keep the situation fully contained. This cross-platform cooperation highlights a mature understanding of how real-world blockchain systems operate — security does not exist in isolation, and responsible teams act across boundaries when needed.
Beyond containment, Dusk introduced additional user-side protections. Wallet-level mitigations were implemented to prevent transfers to known risky addresses, surface clear warnings before transactions are submitted, and reduce exposure to compromised or scam-related endpoints. These measures are designed to protect users proactively, not retroactively.
Equally important is what remained unaffected. The Dusk mainnet continued operating normally. There was no disruption to consensus, privacy features, or core network functionality. This confirms a strong separation between auxiliary infrastructure and the protocol itself — a key indicator of sound system design.
At present, bridge services remain temporarily paused while Dusk completes a broader hardening process. This includes tightening access controls, strengthening monitoring and alerting, and reinforcing bridge-related infrastructure. The bridge will only reopen once the review is complete and the team is confident it can resume safely.
Dusk has committed to sharing a follow-up update once the review concludes, including a clear plan and timeline for reopening bridge services and resuming the next phase of ecosystem expansion.
In a space where silence often follows incidents, Dusk chose transparency, speed, and prevention. This update isn’t just about an isolated event — it’s a reminder that real security is measured by preparation, response, and accountability.
That’s how long-term networks earn trust.

