I researched Fogo’s design notes and one detail stood out: rather than minting a new token standard, they modified SPL Token and layered session-based authorization on top of the SVM delegation model. That choice reads less like deference to Solana’s ecosystem and more like an operator’s preference for predictable surfaces.”
I’ve watched this debate play out enough times that it feels predictable. A team says, “Let’s own the standard,” and for a moment it sounds clean: fewer legacy constraints, better primitives, tighter fit with the new feature they want to ship. Then reality shows up. The first wallet integration takes longer than expected. Indexers don’t know what to track. Auditors start listing edge cases you didn’t even model. Someone on the ops side asks a simple question like, “What happens if a user revokes approval halfway through?” That’s when the excitement turns into a quiet bill. A new standard isn’t just code. In the context of #Fogo , it’s a compatibility tax across the entire stack, and most teams only internalize that cost after something snaps in production.
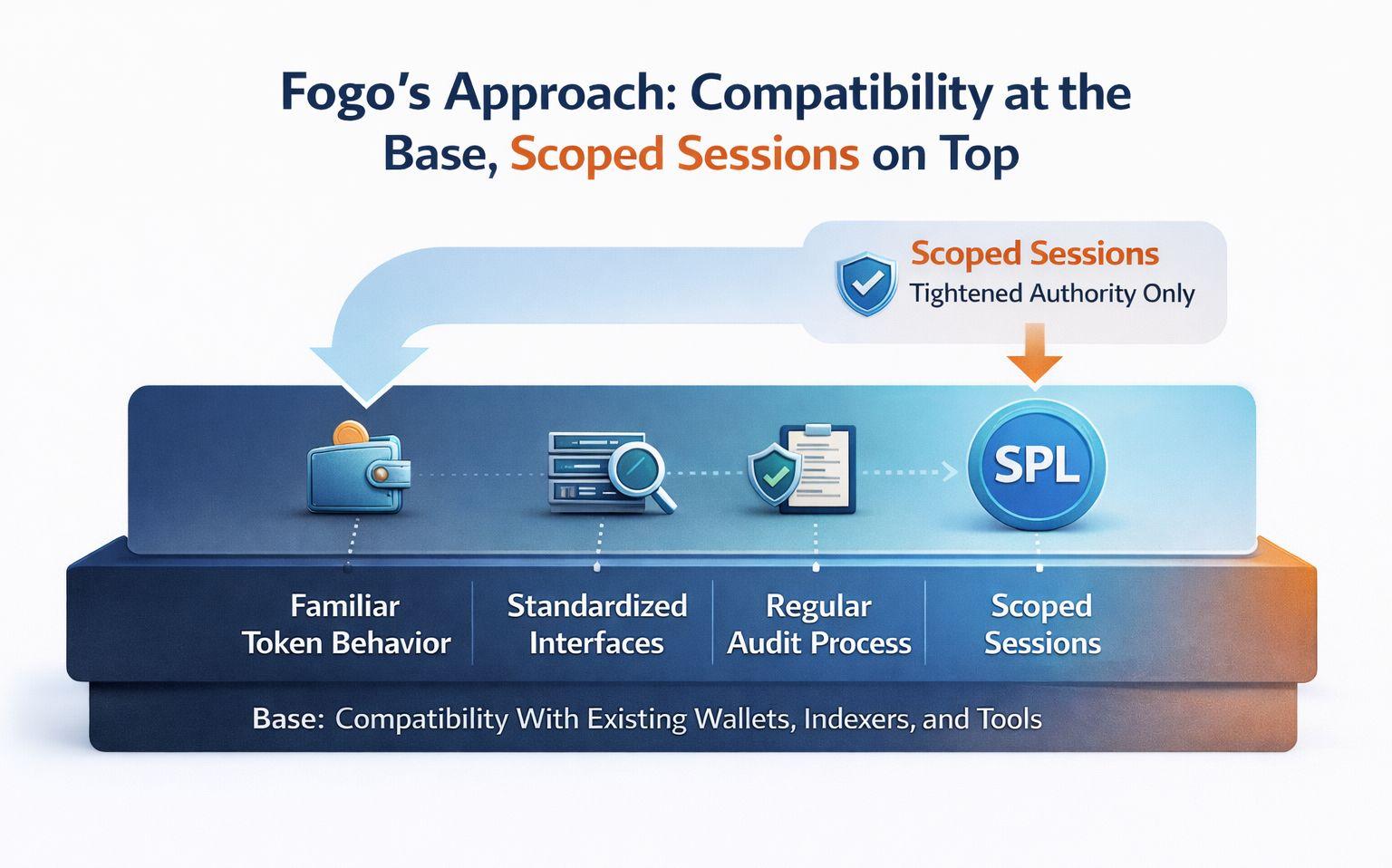
What I took away from @Fogo Official approach is that they’re thinking like people who’ve had to live with the consequences. When your token behavior looks familiar to the existing tooling stack, you can feel the integration surface shrink. Wallets don’t need special handling. Indexers don’t need custom logic. Audits don’t balloon just because the standard is new. Then, instead of rewriting the whole substrate to get new capabilities, they add scoped sessions on top, tightening authority without changing what everyone already understands. To me, that reads like maturity. It’s choosing controllability over novelty at the exact layer where mistakes are most expensive: user funds and app reliability.
Lately it’s felt like watching the same sprint on repeat. A team rushes out a new token program, adds a bespoke permission system, bolts on a custom signing flow, and calls it momentum. Then the second phase begins. Wallet support is behind because nobody wants to carry special cases. The audit scope quietly expands because every custom path creates new edge conditions. App teams end up burning weeks on glue code just to make basic workflows behave. I’ve seen people mistake that pace for progress, but it’s usually just relocating the risk. The real failures don’t show up in the launch thread. They show up later in the integration layer, where the problems are less visible and the fixes are more expensive.
The Discipline Behind Scoped Permissions.
Fogo is effectively warning against reinventing the most widely touched surface area in the stack. The discipline they are building is: keep token semantics familiar, then enforce authority through explicit guardrails. Sessions can be scoped by time, program allow lists, and spending limits, with a clear audit trail of what was permitted and when. That gives apps “delegation with controls” instead of blanket approvals that live forever.
How Competing L1s Increase Integration Load.
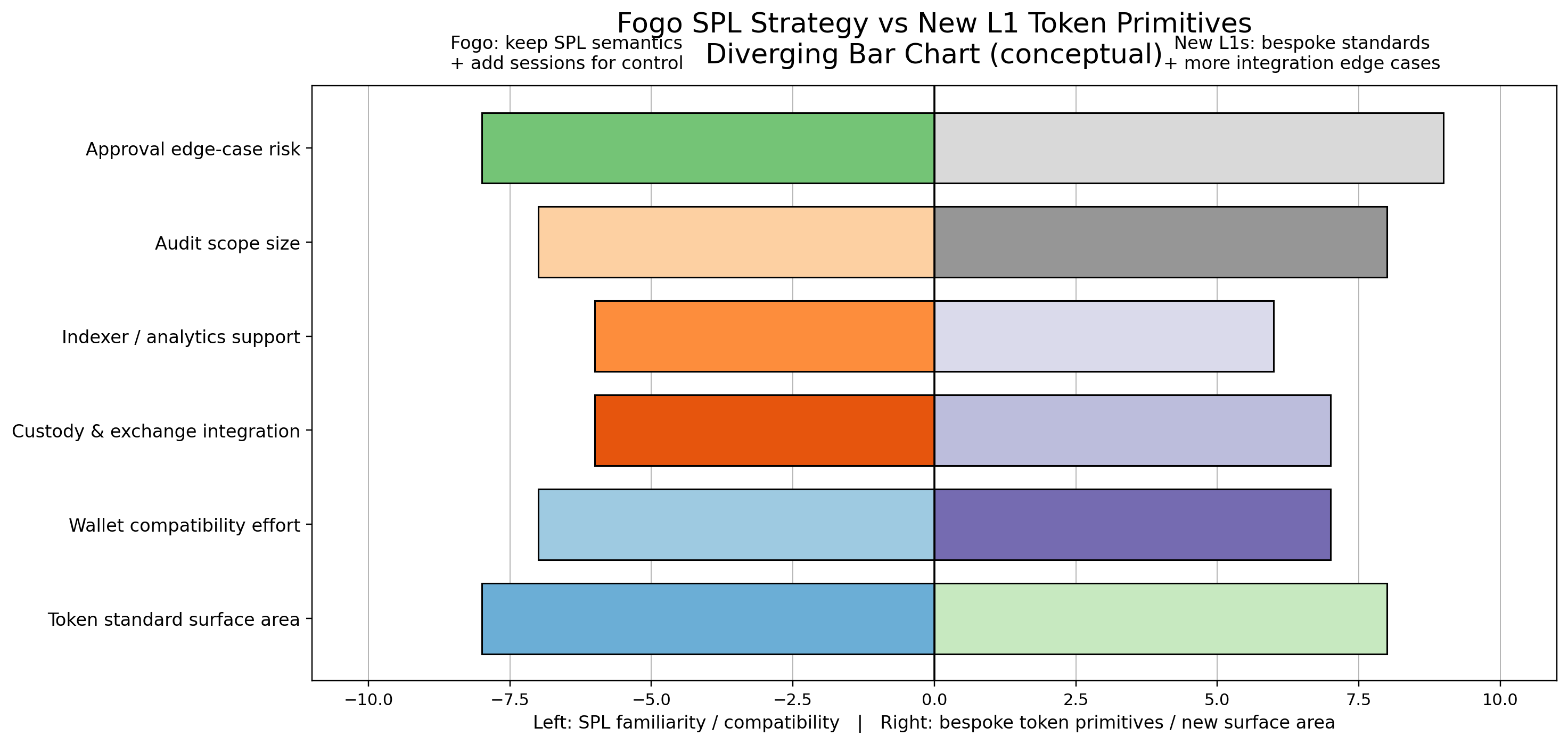
A useful contrast is the path taken by newer L1s that shipped with their own native asset frameworks and token primitives, like Aptos ($APT ) or $SUI in the Move ecosystem. They get cleaner control over the standard, but they also force every wallet, custody provider, indexer, and exchange integration to treat the token layer as a new surface area, with new edge cases around approvals, transfers, metadata, and recovery flows. Even in the EVM world, you see a similar pattern when teams push custom token mechanics or bespoke authorization layers that diverge from what wallets and infra assume by default. Fogo’s SPL strategy is the opposite risk trade. Keep the most widely integrated token semantics familiar, then add capability through sessions and scoped delegation so the “newness” lives in permission boundaries rather than in the token itself. That tends to lower integration drag, shorten audit scope, and reduce the number of places where a small mismatch turns into a funds-at-risk incident.
A Real Wallet Flow Under Stress.
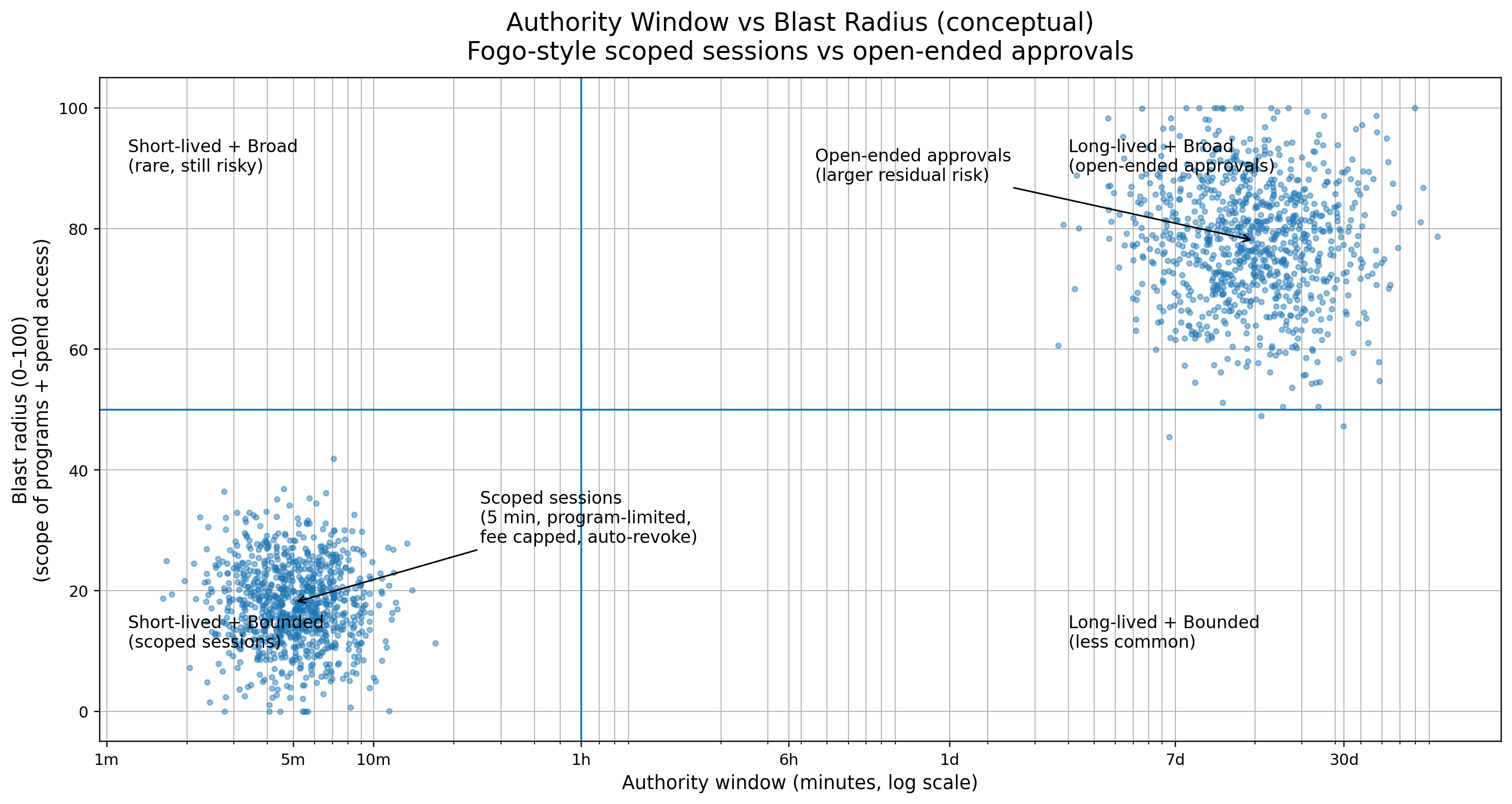
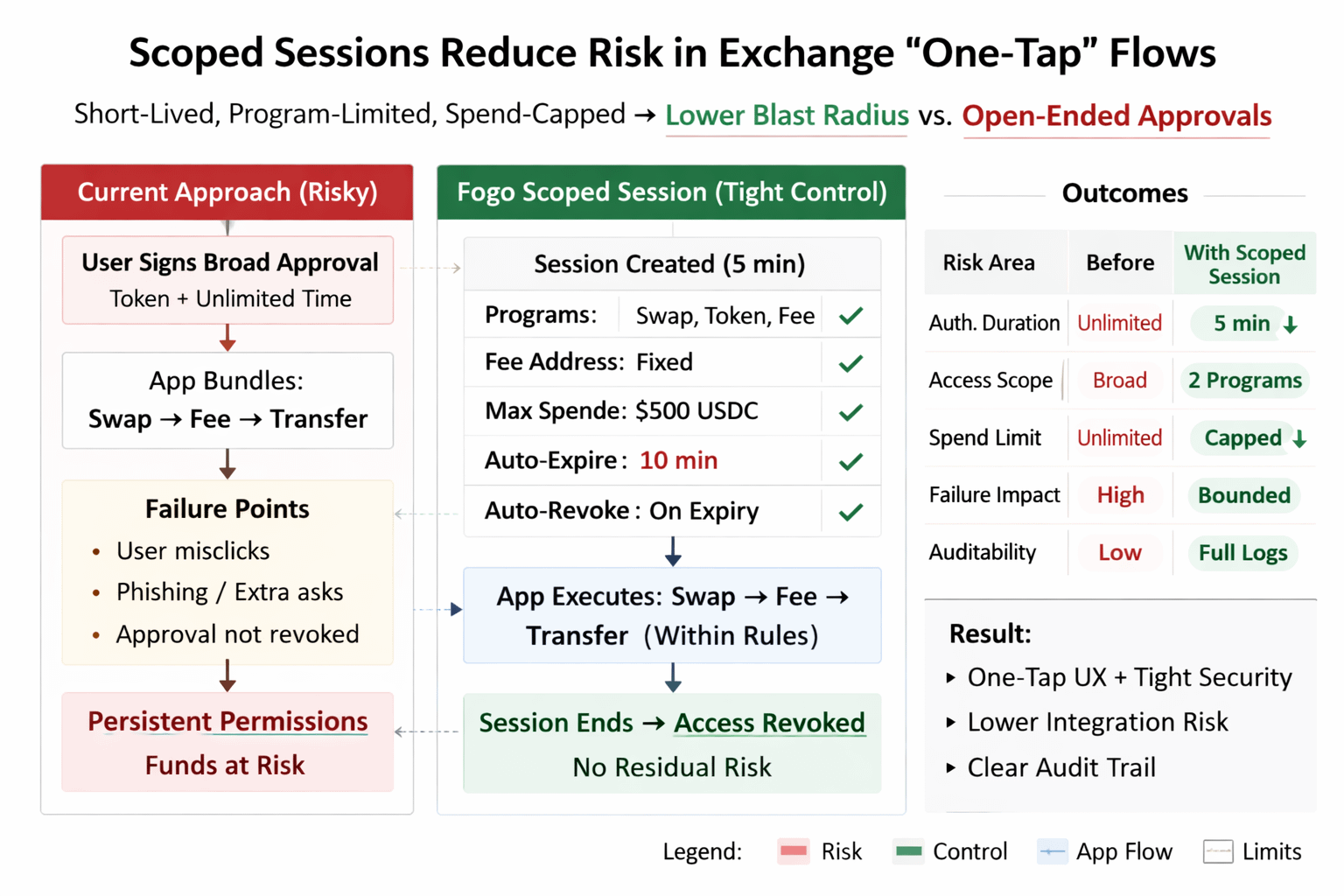
A concrete use case is a Fogo consumer wallet running a “one tap” flow for an exchange account: swap USDC to SOL, pay a service fee, then send the remainder to a new address. Without sessions, many apps rely on broad approvals that sit open ended, or they ask users to sign multiple transactions in a row. In practice, users misclick, abandon the flow mid way, or get phished into signing an extra approval that persists. With SPL compatibility plus session based authorization, the wallet can issue a session that is valid for 5 minutes, limited to a specific swap program and a specific fee address, capped to a maximum spend, and automatically revoked at expiry. The user gets the convenience of a bundled experience, while the permission surface stays tight enough that ops teams can defend it and auditors can trace it.
Why Wallet-Ready Standards Lose The Hype Cycle
I’ve watched the market get oddly dismissive when a team like Fogo chooses the boring path. There’s no shiny token narrative to point at, no new acronym to chant, nothing that looks like a fresh category. Backward compatibility can feel like settling, and sessions sound like wallet plumbing. But that reaction is normal. Traders price what they can see first. The cost of operational debt usually shows up later, when the hype has moved on and Fogo-style decisions start looking sensible.
What makes the logic stick, at least for me, is who cares first, and Fogo is clearly building for that audience. It’s not speculators. It’s the people who get the late-night messages when approvals go wrong: wallet teams, auditors, exchange integrators, ops leads. I’ve seen the same failure pattern repeatedly. An app sponsors fees and tries to bundle a trade plus a transfer. With a custom token standard, a wallet mis-handles an edge case during allowance revocation and a user is left with permissions that quietly persist. On Fogo, scoped sessions give you a cleaner boundary: the authorization can expire in 10 minutes, be restricted to two programs, capped to a fixed amount, and the blast radius stays bounded even if the user abandons the flow.
Where Permissioning Becomes Internal Controls.
And this is where the market eventually catches up, including for networks like Fogo that prioritize controls over novelty. As more workflows go on-chain, permissioning gets evaluated like internal controls by default. Least privilege stops being a slogan and becomes a requirement. Expiring authority becomes expected. Logs that auditors can follow become part of “done.” The standards that fit existing wallet behavior tend to earn distribution not because they are exciting, but because they reduce integration drag while still supporting modern authorization patterns, which is exactly the lane $FOGO is leaning into.
Institutional trust is not won by clever primitives. It is won by systems that behave predictably under stress, integrate cleanly, and fail with contained consequences. Fogo is aiming for that prize, and it shows in the choices that are easy to overlook.
