Traditionally in the crypto or blockchain space, holding a "private key" grants unrestricted access—allowing the holder to transfer funds, alter data, and more. This poses a significant risk if a key holder acts maliciously or goes "rogue".
@Quack AI Official redefines this concept. x402 is not merely a signing tool, it is an intelligent security system directly integrated with governance protocols.
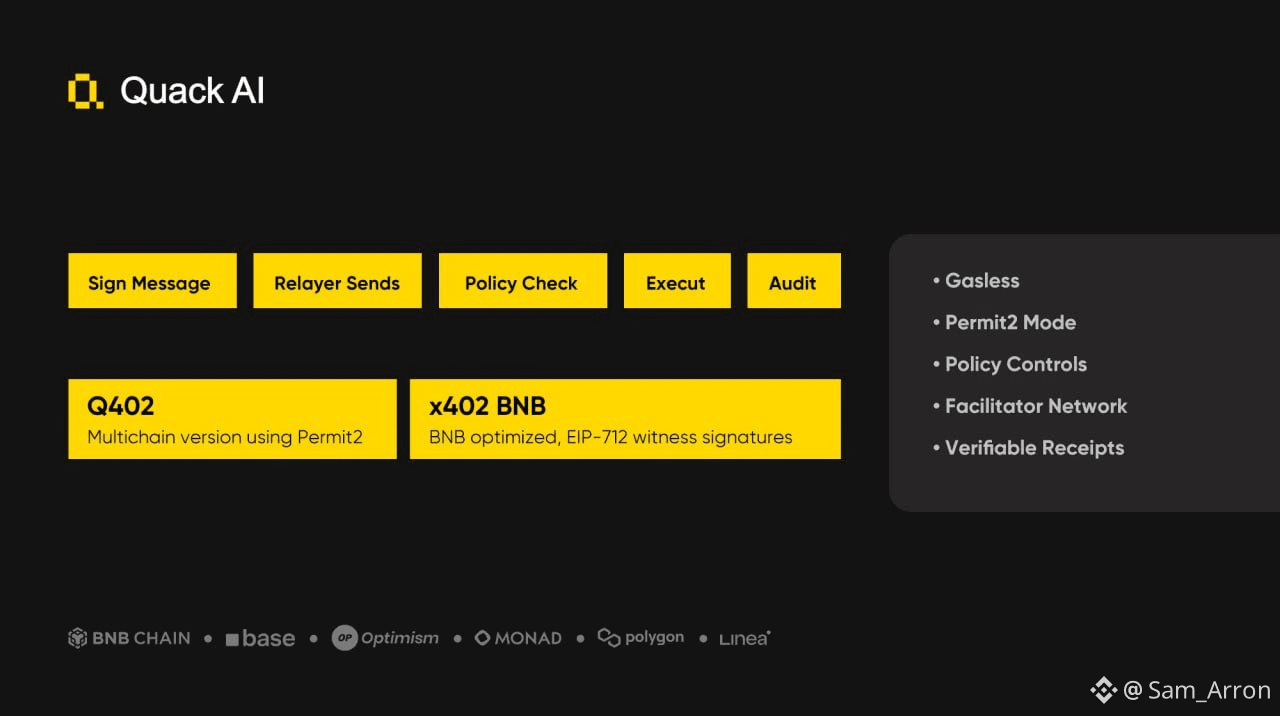
Detailed Workflow Explanation (Based on Image & Text)
Below is a simplified technical breakdown based on the diagram and text you provided:
1. Governance & Policy (Intent and Rules)
• Governance Decides "What": The power holders (DAO or project management) determine what actions are permissible.
• Policy Check: The concept of "trusting the admin" no longer exists. The system itself enforces the policies. If the rule says "A," the admin simply cannot do "B."
2. The Role of x402 (The Gatekeeper)
• x402 Decides "When": x402 functions as a logic gate. It ensures that the timing and execution conditions align strictly with the granted permissions.
• Q402 & x402 BNB Versions: These are technical variants (multichain or BNB-specific), but the core essence is the same: they utilize advanced technology (Permit2 / EIP-712) to securely validate permissions.
3. Execution by Facilitators
• Facilitators Execute: There are parties tasked with processing the transactions (facilitators/relayers).
• Can't Override Rules: This is the key point. Even though facilitators process the transactions, they do not have the power to alter rules or conduct secret transactions. They are merely "couriers" working within a locked perimeter.
4. Audit & Transparency
• Verifiable Receipts: Every step is recorded. There are no "phantom" or hidden transactions.
• No Rogue Execution: Because the system blocks actions outside the rules from the very beginning, rogue execution (misuse of funds or power) is impossible.
