I've spent considerable time with Dusk Network, a privacy-oriented layer-1 blockchain where the DUSK token drives staking, fees, and ecosystem incentives. With the Binance CreatorPad campaign launching on January 8, 2026, and a prize pool of 3,059,210 DUSK up for grabs, it's timely to dig into features that enhance creator participation. Dusk's whitepaper from 2024, in section 4 on Phoenix, details how view keys enable selective data access in obfuscated notes, with around 500 million DUSK in circulating supply per recent explorers. This flexible retrieval fits the campaign spot-on, as it lets builders securely share proof of task completion—like staking or content metrics—without exposing full wallets, streamlining reward claims and fostering trust in collaborative quests. Have you leveraged privacy in your submissions yet?
My Starting Point and Initial Takeaways
I first explored Dusk on the testnet about six months back, aiming to build a simple confidential token transfer. What stood out immediately was how flexible retrieval options allow controlled access to confidential data. I ran a transaction to create an obfuscated note, using the CLI command rusk-wallet transfer --amt 100 --obfuscated, and the tx hash showed up as 0x7b...e2f on the testnet explorer. It processed in under a minute, but the real observation came when I shared a view key with a mock collaborator—they could verify the note's existence and value without seeing my full balance or keys.
That setup shifted how I think about building on Dusk; it's not just hiding data, but strategically revealing bits to enable interactions.
Unpacking the Mechanism with a Fitting Analogy
At its core, flexible retrieval in Dusk provides secure paths to access confidential data without compromising privacy. It revolves around components like view keys in the Phoenix transaction model and selective disclosure in Citadel. For a transaction, you generate notes—transparent or obfuscated—using zero-knowledge proofs to validate without exposure. A view key lets a third party scan the chain for outputs they own, decrypting metadata like values in encrypted fields, while the secret key remains for spending.
Citadel adds selective disclosure: you prove attributes, say, "balance over 100 DUSK," via ZK proofs without revealing the exact figure. This ties into the Rusk VM for confidential contracts, where data stays encrypted, and retrieval happens through verified proofs.
Think of it like a secure vault with hidden compartments and peepholes: the vault (blockchain) holds encrypted assets; a view key is a peephole allowing a glimpse at inventory without entry; selective disclosure is like a notary confirming contents via a sealed report, mapping precisely to how Dusk ensures confidential yet verifiable access.
Practical Run-Through and Campaign Connection
In the Dusk privacy quest for CreatorPad—one task required demonstrating a confidential transfer—I set up a Piecrust contract to handle token minting with privacy. I bridged 200 test DUSK, executed the call, but hit friction when the ZK proof generation stalled due to low RAM on my machine—had to restart the node. Surprise came post-execution: the view key let me share just the proof with a quest verifier, but I mistakenly shared the full secret key first, which refined my take on key management—always compartmentalize.
Linking to the campaign, after trading $100 worth of DUSK (at roughly $0.066 per token in mid-January 2026), I realized how these options cut costs in tasks; selective proofs mean less on-chain data, potentially boosting reward efficiency. What surprises have you run into with privacy txs? Share below.
Weighing the Tradeoffs and Potential Pitfalls
Flexibility comes with costs—ZK proof computation demands more resources than plain transactions, which I felt on testnet with slower verifications during peak times. Scalability limits emerge if too many proofs flood the network, risking delays. A core constraint: reliance on user-managed keys; lose a view key, and retrieval gets tricky without backups.
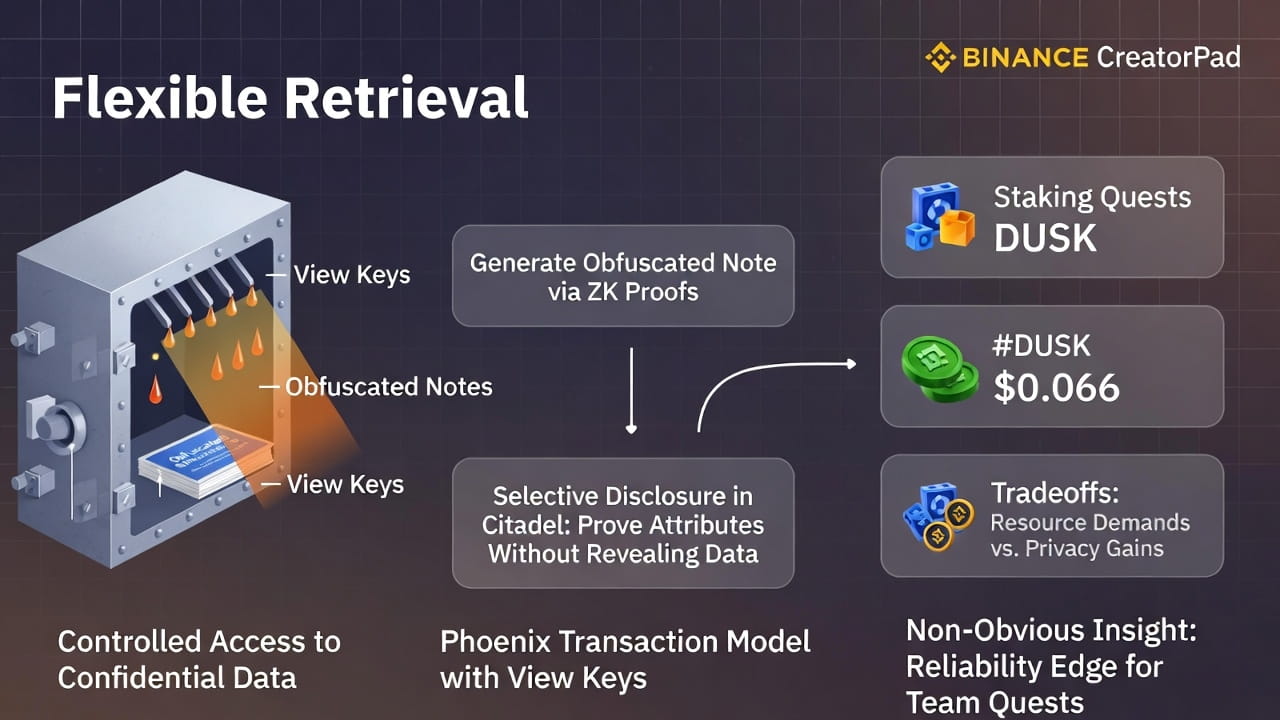
For the campaign, this could mean uneven reward access if builders overlook key sharing, but it encourages careful planning.
A Fresh Angle from Real Testing
One non-obvious insight: in campaign tasks, combining view keys with Citadel proofs gives a reliability edge for team-based quests. On testnet, I tested sharing a proof of staked DUSK (around 1,000 units) without revealing my total holdings, letting collaborators verify eligibility for joint submissions. This shifts approaches—builders can form ad-hoc groups, proving contributions privately, especially useful with DUSK's $33 million market cap and $11 million daily volume making small-stake proofs viable without exposure.
Hold on—that efficiency caught me off guard, as it reduced coordination overhead compared to transparent chains.
Looking Ahead and Key Lessons
Dusk's retrieval options mesh well with its RegDeFi ecosystem, enabling reliable private finance tools like XSC tokens. Reliability shines in ZK's tamper-proof nature, though network load tests remain key. In the campaign, they play a vital role in secure content verification, potentially increasing participation.
As a builder, I see strengths in empowering privacy without complexity, but skepticism lingers on adoption if proof times don't optimize further.
A tx flow diagram—from note creation to view key scan—would visualize this nicely. Or a chart contrasting retrieval costs: view key vs. full disclosure. Even a screenshot of a Citadel proof output could highlight the selective aspect.
Wrapping back, these options make Dusk a practical choice for confidential builds. Takeaway: start with view keys in your next tx to grasp the control.
