When I first started looking at Dusk, I approached it like any other “privacy chain for regulated finance”: check the consensus, skim the token, glance at the buzzwords, move on. But the more time I spent inside their docs and blog, the more something very specific grabbed my attention—not just the idea of confidential smart contracts, but the identity system wrapped around them. Citadel, their zero-knowledge KYC and licensing framework, felt less like an add-on and more like the missing backbone of compliant access control on-chain. It was the first time I saw a chain treat identity and permissions as cryptographic assets that live natively inside the protocol, instead of external paperwork that platforms bolt on in a panic later.
What really shifted my thinking was understanding Dusk’s starting position: this is a privacy blockchain for regulated finance, built so institutions can actually meet real regulatory requirements on-chain while users still get confidential balances, private transfers, and shielded interactions. That sounds impossible if your mental model of KYC is “upload your passport to a centralized database and hope for the best.” Dusk’s answer is the opposite: prove what you need to prove, reveal nothing you don’t, and let the chain enforce compliance via zero-knowledge proofs and confidential smart contracts instead of raw data dumps. The Foundation explicitly frames this as programmable compliance, not performative box-ticking, and that distinction mattered a lot to me.
Citadel is where that philosophy becomes concrete. On paper, it’s a zero-knowledge KYC framework that issues claim-based credentials—rights, permissions, regulatory statuses—as cryptographic attestations users can carry into any Dusk-based application. In practice, it’s a self-sovereign identity layer: users hold credentials that sit on Dusk as private NFTs, and they can prove those credentials to services without exposing the underlying personal data. The framework is designed so that a bank, an exchange, or a regulated dApp can verify “this wallet is allowed to access this product under this regulation” without seeing the passport scan, address, or salary that originally backed that statement. 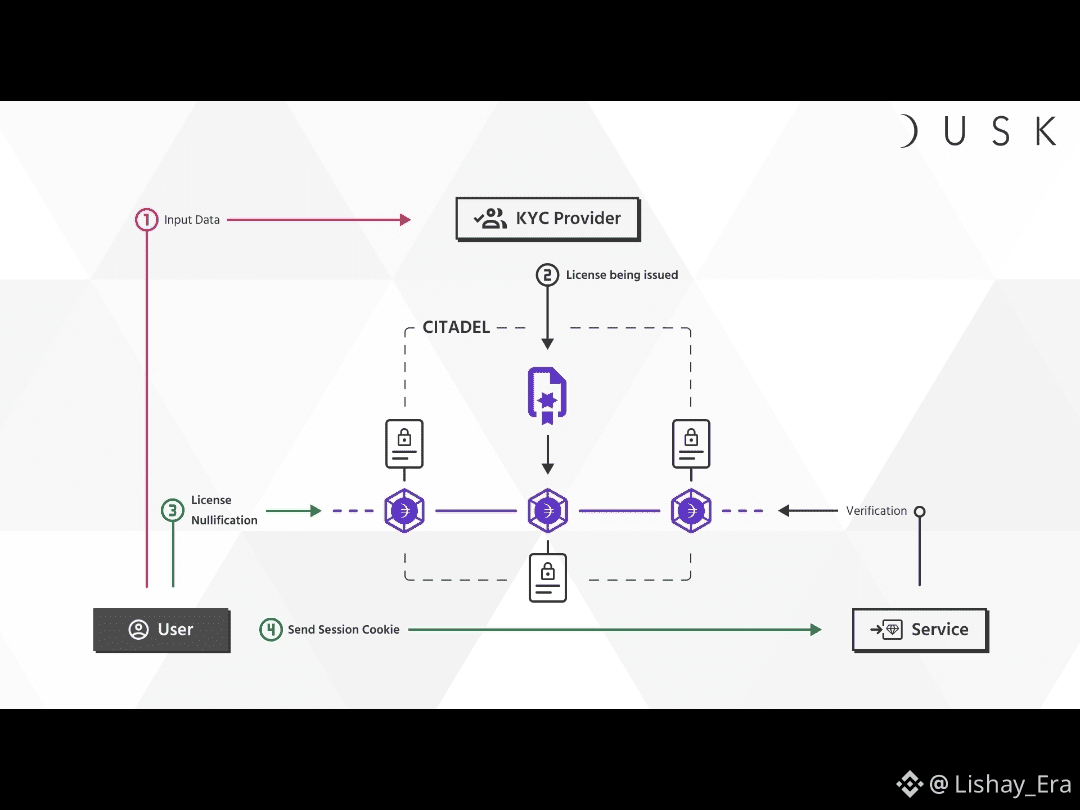
The moment it clicked for me was when I read their “KYC x Privacy” piece and realized Dusk is explicitly rejecting the false choice between total anonymity and full exposure. They argue that privacy and KYC not only can go together, they should—and they already do on Dusk. Instead of making every transaction public forever or handing all your raw identity data to every venue you touch, Citadel lets you present the minimum proof a counterparty or regulator needs, and nothing more. It’s a very different mental model from the “KYC once per platform, leak everywhere” paradigm we’ve normalized across crypto and TradFi.
As I dug into the technical side, I started to appreciate how deep this goes. Citadel is built on top of Dusk’s private-by-default blockchain, where transactions and smart contracts are already shielded using zero-knowledge proofs. That means the identity layer isn’t fighting the base protocol; it’s aligned with it. Rights and licenses are encoded as privacy-preserving NFTs, and users prove possession through ZK proofs rather than public ownership records. In other words, access rights themselves become confidential on-chain objects: verifiable to whoever needs assurance, invisible to everyone else. For someone obsessed with composable infrastructure, that’s huge.
What really impressed me is how the Dusk Foundation thinks about Citadel beyond pure KYC. They explicitly position it as a general licensing and entitlement layer: the same framework that proves your compliance status can prove that you have a right to use a service, consume a dataset, access a product tier, or enter a specific regulated market segment. You can see this in how they describe Citadel as a privacy-preserving licensing tool, not just an identity badge. That framing moved me from thinking about “passing KYC” to thinking about programmable access: who can do what, under which rules, proven privately and enforced on-chain.
From there, my mind went straight to the user experience we’re all used to. Right now, every exchange, broker, and DeFi front-end treats KYC as a siloed onboarding marathon. You repeat the same process over and over, spraying copies of your documents everywhere, and then those platforms try to retrofit compliance into smart contracts that were never designed to care about jurisdiction, product limits, or investor categories. On Dusk, the sequence flips: identity and regulatory status are first-class objects that live at the protocol level, and dApps simply ask for the proofs they need. You go from “upload documents into a black box” to “present a cryptographic credential that your wallet controls,” and that is a completely different UX story.
What I also like is how well this identity layer fits the European regulatory context Dusk is embedded in. The project is based in the Netherlands, launched back in 2018, and is very explicit about aligning with frameworks like MiFID II and MiCA rather than pretending regulation will magically disappear. When I read their materials and external research, I don’t see “we’ll fight the regulators”; I see “we’ll give you cryptographic tools that let you satisfy them without sacrificing user privacy.” Citadel becomes the bridge: institutions get comfort that rules are enforced; users get the comfort that their personal information isn’t scattered across thousands of databases.
The most personal shift for me was in how I think about data minimization. I used to view it as an abstract GDPR principle everyone quotes and few actually implement. Dusk, through Citadel and its zero-knowledge architecture, forces you to encode minimization at the primitive level. A lending dApp doesn’t need your full profile; it needs proof that you meet a risk or regulatory threshold. A security token platform doesn’t need your full history; it needs proof that you’re allowed to hold that instrument in your jurisdiction. The idea that these proofs live as reusable credentials in your wallet—and not as raw fields in someone else’s database—is what made me feel like “self-sovereign identity” is finally being treated as an engineering problem, not a conference slogan.
Of course, none of this works if the underlying chain can’t enforce confidential logic at scale, and that’s where Dusk’s confidential smart contracts and Phoenix transaction model circle back into the story. Phoenix allows obfuscated transactions and private contract execution, while the EVM-compatible layer gives builders familiar tools to plug Citadel checks directly into business logic. So when I imagine a security token dApp on Dusk, I don’t imagine an off-chain “KYC checkbox”; I imagine a smart contract that simply refuses to execute unless a valid Citadel credential is presented, all without doxing the user on a public ledger.
What really stays with me is how this architecture changes KYC from a one-time gate to an ongoing, programmable relationship. A credential can expire, be revoked, be upgraded, or be scoped to specific products—all enforced cryptographically on-chain. The Dusk Foundation’s research around self-sovereign identities explicitly talks about rights as NFTs and proofs as ZK statements, which means the whole lifecycle of “who is allowed to do what” can be automated and audited without ever dumping raw identity data into the open. That is the kind of discipline I want to see if we’re serious about real institutional adoption.
From a markets perspective, this also unlocks a very different kind of composability. Imagine multiple venues on Dusk—trading platforms, lending desks, issuance portals—all trusting the same Citadel credential types. A user doesn’t start from zero each time; they carry a portfolio of proofs with them, and each venue simply verifies what it needs. Institutions can define their own rules on top, regulators can still audit flows when necessary, but the base identity and permissioning layer is shared. It’s like having a common language for compliance that every protocol on Dusk can speak.
Personally, the more I sit with Dusk and Citadel, the more I feel my old view of KYC as a necessary evil dissolving. Instead of thinking “this is the tax I pay to access real markets,” I start thinking “this is the cryptographic rail that lets me access serious instruments without handing over my life every time.” The Foundation’s insistence on privacy as a right and compliance as a requirement comes through strongly in their writing, and for someone like me—who cares both about user dignity and institutional constraints—that combination is exactly what I want to see at the base layer, not patched on at the application edge.
So when I say Dusk changed how I think about on-chain identity, I’m not just praising another ZK buzzword. I’m talking about a specific design: a privacy-first L1 with native confidential smart contracts, wrapped in a self-sovereign identity and licensing system that treats credentials as programmable rights, not static PDFs. Citadel, as the identity backbone of that stack, let me imagine a future where “KYC’d” doesn’t mean “leaked forever”—it means holding a portfolio of cryptographic proofs under my own control, and using them to step into regulated markets on my terms. And for me, that’s exactly the kind of infrastructure that deserves to sit underneath the next decade of serious on-chain finance.
