In most discussions around blockchain adoption, the focus drifts toward surface metrics: transactions per second, block times, raw throughput. For institutions, those figures are secondary. The real constraint has always been transparency itself. A public ledger that exposes trading behavior, liquidity positioning, or counterparty relationships is not merely inconvenient it is unusable.
Dusk Network begins from that assumption. Rather than attempting to retrofit privacy onto an open system, it builds confidentiality into the foundation. Zero-Knowledge Proofs are not an accessory or an optional mode; they are part of the protocol’s native grammar. The result is a Layer-1 designed for environments where discretion is not a preference, but a requirement.

SBA Consensus: Finality Without Ambiguity
Settlement is only meaningful when it is final. Many blockchain systems rely on probabilistic assurances, where certainty increases over time but never fully arrives. In financial markets, that ambiguity is unacceptable. Ownership must be determinable, enforceable, and immediate.
Dusk’s Segregated Byzantine Agreement (SBA) consensus addresses this directly. The mechanism separates block creation from validation, distributing responsibility in a way that reduces attack surfaces while maintaining speed. Block Generators participate through a blind bidding process powered by Verifiable Random Functions. Until a block is revealed, the proposer remains unknown, limiting the feasibility of targeted interference.
Validation is handled by a rotating committee of Provisioners executing a multi-step Byzantine agreement. Once consensus is reached, the block is final irreversible without qualification. There is no waiting period, no probabilistic comfort. The chain moves forward with the assumption that each block must stand as legally and economically complete.
Piecrust VM: Designed for the Weight of Zero Knowledge
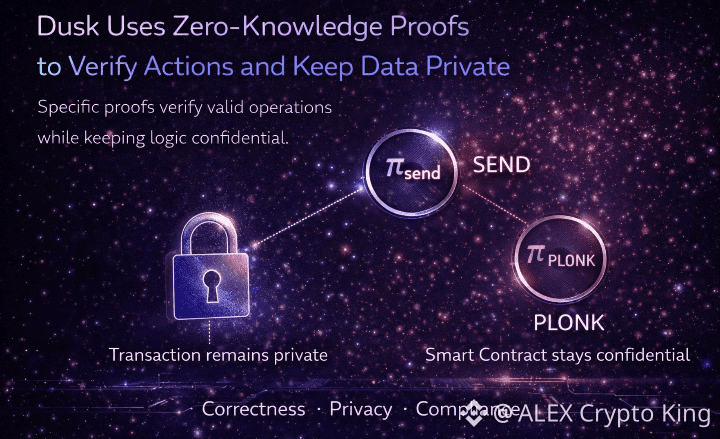
Zero-Knowledge systems are computationally demanding. Many virtual machines tolerate this cost rather than addressing it directly. Piecrust does not.
Written in Rust and executed through WebAssembly, Piecrust is structured around the realities of ZK computation. Arithmetic-heavy operations, proof generation, and verification are treated as first-order concerns. Memory safety and execution efficiency are not optimizations; they are prerequisites.
This allows confidential smart contracts to behave less like experiments and more like infrastructure. Compliance logic, asset lifecycle management, and distribution mechanisms can execute privately without forcing the network to absorb excessive latency. The system remains responsive because it was never designed to be casual.
Citadel and XSC: Compliance as a Property of the System
Regulatory compliance is often handled at the edges off-chain checks, manual processes, institutional trust. Dusk integrates it into the protocol itself.
Citadel provides a self-sovereign identity framework where credentials are proven, not disclosed. Users can demonstrate eligibility jurisdiction, accreditation status, regulatory clearance without exposing the documents behind those claims. Zero-Knowledge Proofs preserve privacy while maintaining verifiability.
The Confidential Security Contract (XSC) standard extends this logic to assets. Compliance rules are embedded directly into the contract’s behavior. Transfers are evaluated against Citadel proofs at execution time. If conditions are not met, the transaction does not occur. There is no exception handling, no retroactive correction. The asset enforces its own constraints quietly and consistently.
Cryptographic Foundations: PLONK as Infrastructure, Not Ceremony
Dusk’s privacy model is underpinned by PLONK, a ZK-SNARK system built around a universal trusted setup. This choice avoids the fragility of per-contract ceremonies and reduces operational overhead for developers.
A single setup applies across the network, allowing confidential applications to be deployed without introducing new trust assumptions each time. It is an approach that favors continuity over novelty less spectacle, fewer moving parts, and a lower tolerance for unnecessary risk.
Closing Thoughts
Dusk Network does not present itself as a disruption in search of attention. Its design suggests something else entirely: a system built with the expectation of scrutiny, load, and consequence. Instant finality, private computation, and programmable compliance are not framed as features, but as conditions for use.
This is not a blockchain designed to perform in ideal conditions. It is designed to hold up when the environment is adversarial, regulated, and unforgiving. Privacy here is not a shield it is a structural requirement for participation at scale.
