Dusk has been unusually consistent since 2018 about what it is actually trying to solve. It is not chasing a generic narrative about decentralization. It is building a layer 1 specifically engineered for regulated finance where privacy is mandatory, auditability is non negotiable, and application design has to reflect how institutions really operate. That starting point matters because regulated markets do not fail on technology alone. They fail when the infrastructure forces institutions into impossible tradeoffs. Either everything is transparent and you leak strategy, counterparties, and sensitive positions. Or everything is hidden and you cannot prove compliance when it counts. Dusk is built around the idea that privacy and oversight can coexist if the chain treats selective disclosure as a native capability instead of an afterthought.
A useful way to think about Dusk is that it is not trying to make every transaction private. It is trying to make privacy configurable without breaking settlement integrity or compliance controls. In institutional settings, the requirement is rarely absolute secrecy. The requirement is controlled visibility. A bank, a broker, or an issuer needs to keep sensitive information confidential to protect clients, manage market impact, and meet data protection rules. At the same time, they need the ability to prove that transfers followed restrictions, that participants were eligible, and that reporting obligations can be satisfied. Dusk frames this as privacy by design with auditability by design, meaning the chain is engineered so that confidentiality and verifiability are both part of normal operation rather than a bolt on process.
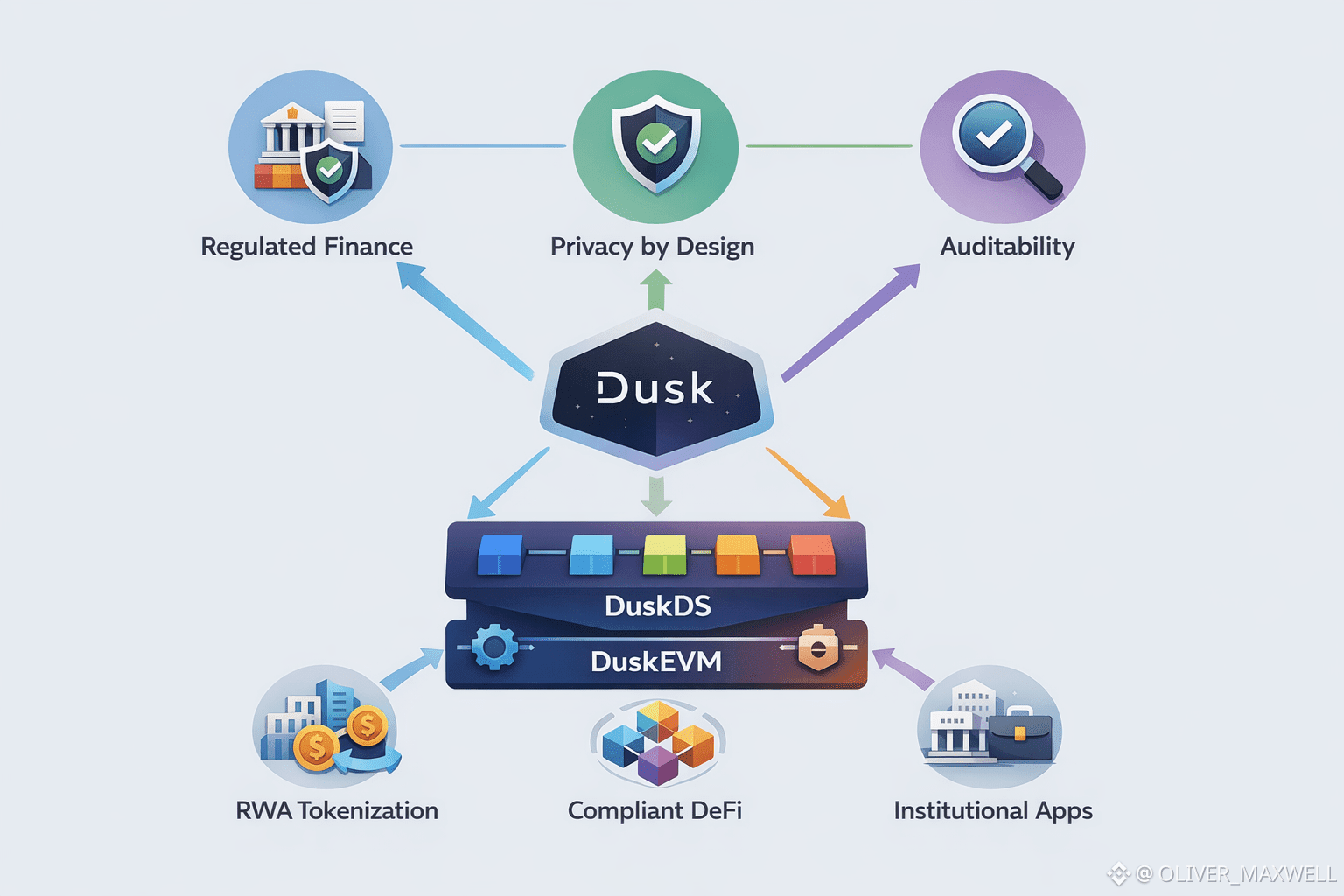
This is where Dusk’s modular architecture becomes more than a technical preference. Modularity is what lets Dusk separate settlement concerns from execution concerns, and it is what lets institutions build regulated applications without turning the base layer into a rigid one size fits all system. DuskDS functions as the settlement and data layer where consensus, finality, and native transaction models live. DuskEVM functions as an execution environment that supports familiar smart contract development while still being anchored to Dusk’s privacy and compliance oriented foundation. The practical implication is that institutions can design products with the execution surface they want while still inheriting the chain’s settlement guarantees and its privacy and auditability primitives.
Inside that architecture, Dusk’s most important design decision is that it supports distinct transaction models that map to real compliance needs. One model is public and account based, which is useful when transparency is acceptable or even desirable for operational simplicity and reporting. The other model is shielded and note based, which is critical when confidentiality is required to protect counterparties, positions, or sensitive corporate information. The reason this matters for regulated finance is that compliance obligations vary by workflow. An institution might want transparent movement for operational treasury between internal accounts but require confidentiality for client settlements or for regulated instruments where the holder registry and transfer timing are sensitive. Dusk’s approach lets applications choose the disclosure posture per flow without forcing the entire system into full transparency or full opacity.
The privacy mechanism is only half the story. The other half is how Dusk keeps auditability intact without turning privacy into a loophole. Dusk is structured around the idea of selective disclosure, where authorized parties can verify facts when necessary without forcing all information into the public domain. That is the compliance sweet spot. A regulator or auditor does not need the world to see every detail. They need the ability to verify that rules were followed. In a proof based compliance model, the participant can prove eligibility, jurisdictional constraints, transfer limits, and other policy requirements without publishing the underlying private data. This reduces the amount of personal and transactional data that gets exposed, which is increasingly important as data protection standards tighten and institutions become more risk averse about leakage.
This is also why Dusk’s focus on regulated and privacy focused financial infrastructure is not simply a positioning line. It is a product thesis about market structure. Public transparency is often presented as a virtue in crypto, but in regulated markets it can be a defect. If every balance and transfer is observable, then basic financial behavior becomes intelligence for competitors. Inventory moves become signals. Large allocations become attack surfaces. Client activity becomes a dataset. Even when no law is broken, the institution fails its duty to protect confidential client information and proprietary strategy. Dusk treats that problem as structural. It is building rails where confidentiality is expected, but where compliance and accountability can still be proven in a controlled manner.
Dusk’s consensus and networking choices reinforce this institutional intent. Regulated finance cares about finality because finality determines operational and legal certainty. When finality is weak, institutions cannot safely release collateral, reconcile obligations, or complete corporate actions without costly buffers and manual oversight. Dusk is designed around fast finality and a low probability of forks, with a proof of stake foundation and a structure that separates proposing and finalizing responsibilities. On top of that, Dusk incorporates privacy preserving elements into validator selection logic, which matters because consensus dynamics can leak strategic information and create coercion risks if leadership patterns are too observable. The networking layer also aims for predictable performance rather than only average throughput, which is aligned with institutional requirements where predictability is often more valuable than occasional peak speed.
The place where Dusk becomes most directly relevant to real world finance is tokenized assets. Tokenization is not simply minting a representation of an asset. In regulated settings, the asset carries rules. Who can hold it. Under what conditions it can be transferred. How dividends or distributions are handled. How voting occurs. How redemptions work. How caps, lockups, and jurisdiction constraints are enforced. Dusk’s asset protocol work is built around supporting these lifecycle realities, including restrictions and corporate action logic, while maintaining confidentiality where necessary. This is a major difference between a chain that supports tokens and a chain that supports regulated instruments. Regulated instruments are defined by their constraints, not by their existence.
Confidentiality is especially important in asset lifecycle events. Corporate actions can reveal sensitive information about issuer decisions, shareholder structure, and timing. A public holder registry can create competitive risk and privacy violations. Distribution mechanics can leak positions. Voting can expose investor behavior. Dusk’s privacy and auditability posture is designed to prevent these processes from becoming public intelligence feeds while still letting issuers, auditors, and regulators validate outcomes. This is where Dusk’s design feels less like a generic blockchain feature set and more like financial infrastructure engineering.
Dusk’s approach to compliant DeFi follows the same logic. The question is not whether an application can offer lending, trading, or yield strategies. The question is whether it can do so while enforcing eligibility, disclosure rules, and risk controls that institutions require. In practice, compliant DeFi needs privacy for counterparties and positions, plus policy enforcement that can be audited. Dusk’s combination of private transaction capability and proof based compliance frameworks is aimed at allowing financial applications to enforce rules without turning the chain into a surveillance layer. That is the core innovation. It shifts compliance from document exchange and database leakage to cryptographic proof of constraints.
Identity is the unavoidable layer beneath compliance, and it is where many systems either become leaky or become brittle. Dusk’s identity direction is oriented toward privacy preserving proofs of rights, meaning a participant can prove they have the right to participate without publicly exposing their identity or permanently linking activity to a visible profile. In regulated finance this matters because institutions are required to know their customers and enforce AML standards, but they are also required to protect customer data and minimize exposure. A system that supports proof of eligibility without broad disclosure aligns with both obligations. It also reduces operational risk, because the less sensitive data is spread across systems, the less there is to breach.
Tokenomics and governance also matter for institutional credibility because they determine whether the network can be modeled and trusted over long horizons. Dusk’s staking design includes clear participation requirements and an emission schedule designed to decay over time, which functions as a long run security budget plan rather than a short term incentive gimmick. Institutions evaluating infrastructure want predictable parameters, not surprise mechanics. Governance also needs to be legible, because regulated participants will ask who can influence protocol evolution and whether governance processes can support stability. A chain built for regulated finance cannot behave like a culture war arena. It has to behave like infrastructure, with change that is deliberate, auditable, and operationally manageable.
What makes Dusk’s positioning most compelling is that it does not ask regulated finance to abandon its core operating principles. It tries to encode them. Confidentiality is preserved through private transaction models and selective disclosure. Accountability is preserved through auditability and proof based compliance. Lifecycle constraints for regulated instruments are treated as core requirements, not edge cases. Modularity provides a practical path for institutions to build bespoke applications without compromising the settlement layer. When you connect these pieces, Dusk reads less like a chain looking for a narrative and more like a project executing a specific infrastructure thesis that began in 2018 and has stayed consistent.
The forward looking opportunity for Dusk is not to compete on generic metrics. It is to become the default settlement and compliance substrate for financial applications that cannot exist on fully transparent rails. That includes regulated tokenized assets where privacy and transfer rules are mandatory, institutional grade venues that need predictable finality, and compliant financial applications where policy enforcement must be provable without exposing sensitive information to the public. The adoption path will depend on whether Dusk can keep its selective disclosure promise in production workflows, whether its privacy mechanisms remain usable rather than purely theoretical, and whether its modular execution surfaces can attract builders who care about regulated outcomes, not only experimentation.
If Dusk succeeds, it will not be because it marketed privacy. It will be because it treated privacy and auditability as the missing primitives for regulated on chain finance, and then built a layer 1 that institutions can actually use without violating their own obligations. That is the real significance of Dusk’s design. It is not trying to make finance transparent. It is trying to make finance on chain function like finance is required to function, private where it must be, auditable where it has to be, and flexible enough to support real instruments with real rules.
