Today let's discuss about security system of Dusk Protocol. So let's gets started.
Imagine you're running a small shop where customers pay with digital tokens. Now, what if someone could create fake identities to manipulate your system or spend the same token twice? This is exactly what blockchain networks face every day, and it's a serious problem that can destroy trust and value.
Dusk Network, a privacy-focused blockchain, has built special defenses against these economic attacks. Let's break down why these attacks are dangerous and how Dusk keeps your transactions safe.
What Are Sybil Attacks and Why Should You Care?
Think of a Sybil attack like someone creating hundreds of fake social media accounts to manipulate a poll. In blockchain terms, a bad actor creates multiple fake identities (nodes) to gain unfair influence over the network.
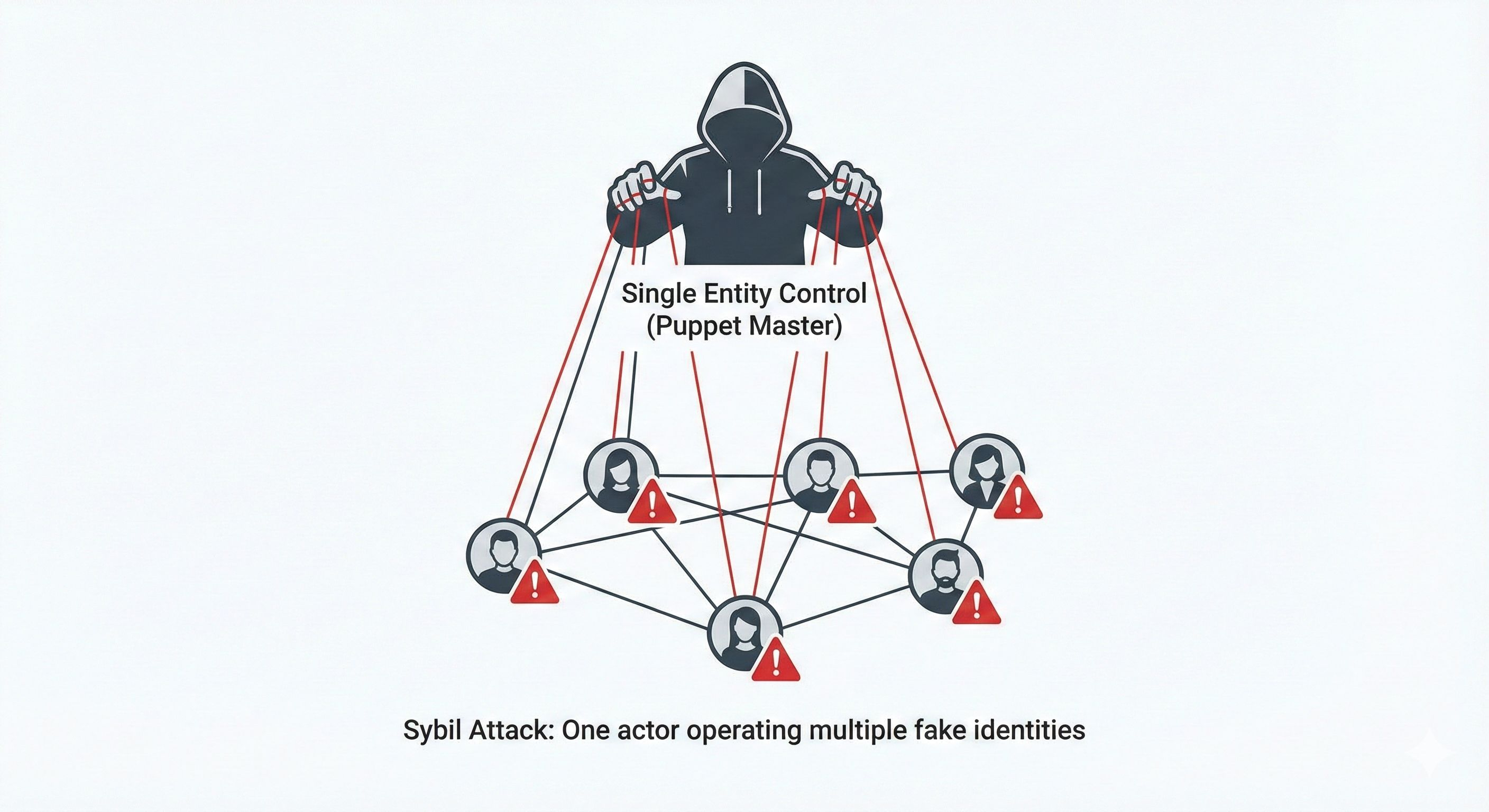
On a private network, this becomes even trickier. Unlike public blockchains where anyone can see everything, private networks have limited visibility. This makes it harder to spot when someone is pretending to be many different people.
The danger is real. If someone controls enough fake nodes, they could:
Block legitimate transactions
Approve fraudulent activities
Manipulate voting or consensus decisions
Steal funds or sensitive data
The Double Spending Problem Explained Simply
Double spending is like using a photocopier on a dollar bill and trying to spend both copies. In digital currency, it means spending the same coin in two different places before anyone notices.
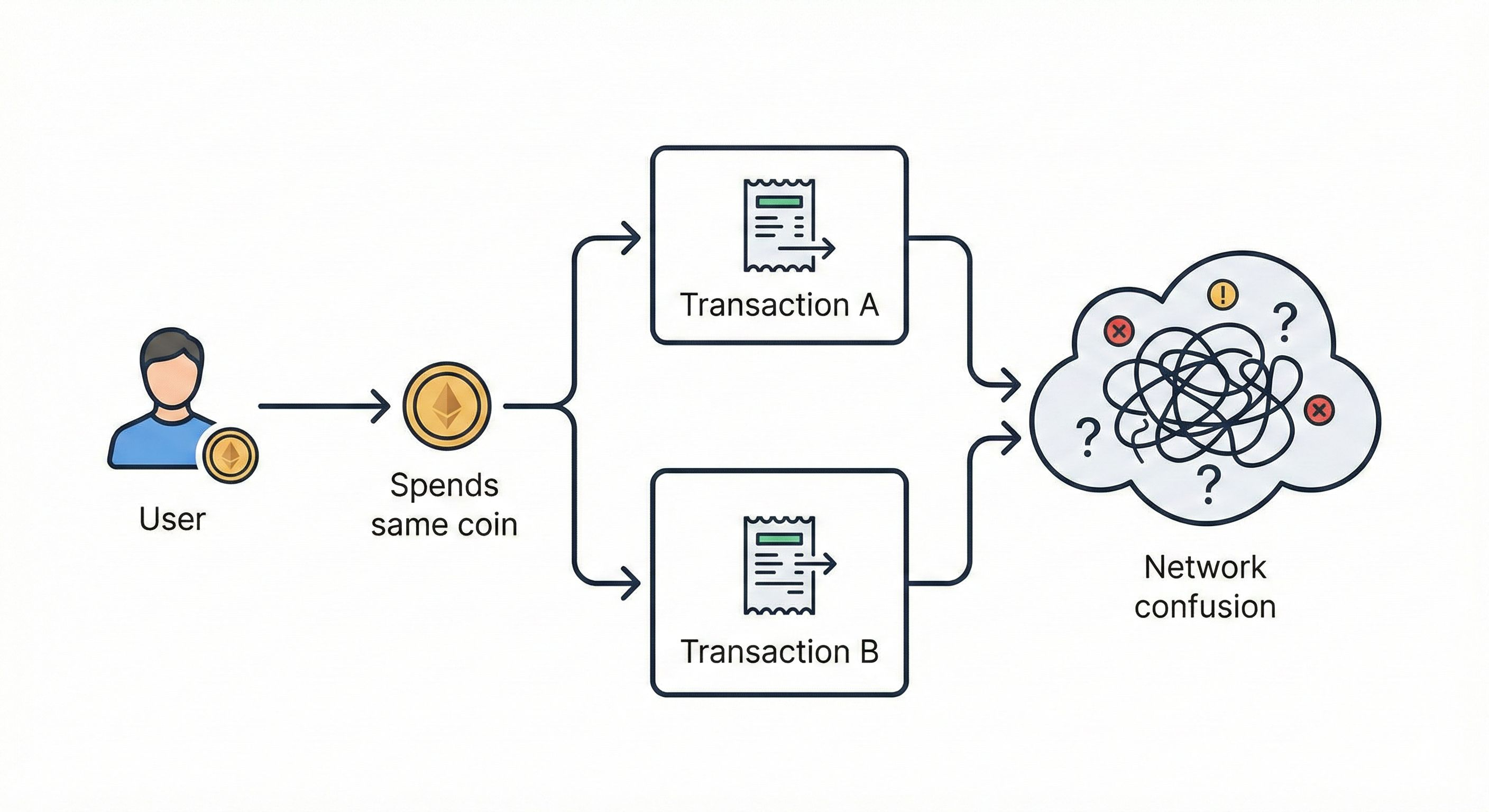
Here's why it's particularly challenging on private networks:
1. Limited validators: Fewer people are checking transactions
2. Privacy features: Harder to track transaction history
3. Speed requirements: Fast transactions can create gaps for exploitation
If successful, double spending breaks the entire trust system. People lose money, and the network loses credibility.
Why Traditional Solutions Fall Short
Most blockchains use one of two approaches:
Proof of Work: Requires expensive computer power to validate transactions. While secure, it's slow and energy-hungry.
Proof of Stake: Validators lock up coins as collateral. Better, but wealthy actors can still gain too much control.
Neither approach fully solves the problem for private, enterprise-grade networks that need both speed and security.
How Dusk Network Stands Guard
Dusk has built a multi-layered defense system that works like a high-tech security building with multiple checkpoints.
1. Segregated Byzantine Agreement (SBA)
This fancy term means Dusk uses a smart voting system where validators must prove they're legitimate before participating. It's like requiring fingerprint verification plus a security badge plus a PIN code not just one form of ID.
2. Stake-Based Participation
To become a validator on Dusk, you must lock up DUSK tokens. This creates a financial stake in the network's honesty. If you try to attack the system, you lose your locked tokens.
Creating multiple Sybil identities becomes expensive because each fake identity needs real tokens locked up. It's like requiring a large cash deposit for each fake account—quickly becoming too costly for attackers.
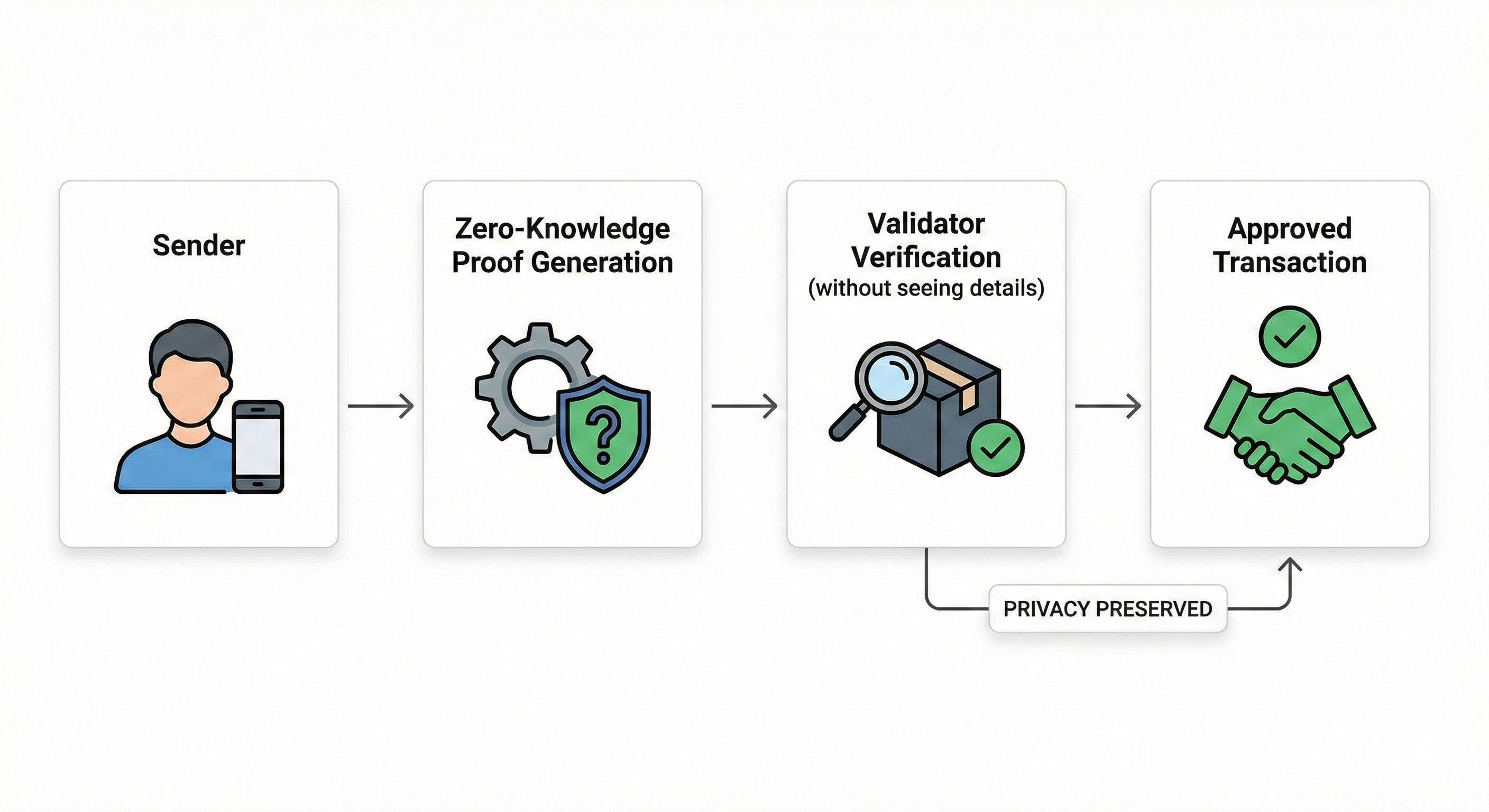
3. Zero-Knowledge Proofs
Dusk uses advanced cryptography that lets validators verify transactions without seeing private details. This means:
Double spending attempts are caught immediately
Privacy remains intact
No single point of failure exists
 4. Randomized Block Generation
4. Randomized Block Generation
Dusk randomly selects block generators from the validator pool. Attackers can't predict who will create the next block, making it nearly impossible to coordinate an attack.
Think of it as a lottery where the winner changes every round you can't bribe or control someone when you don't know who they'll be.
Real-World Protection in Action
Let's say someone tries to double-spend 1000 DUSK tokens:
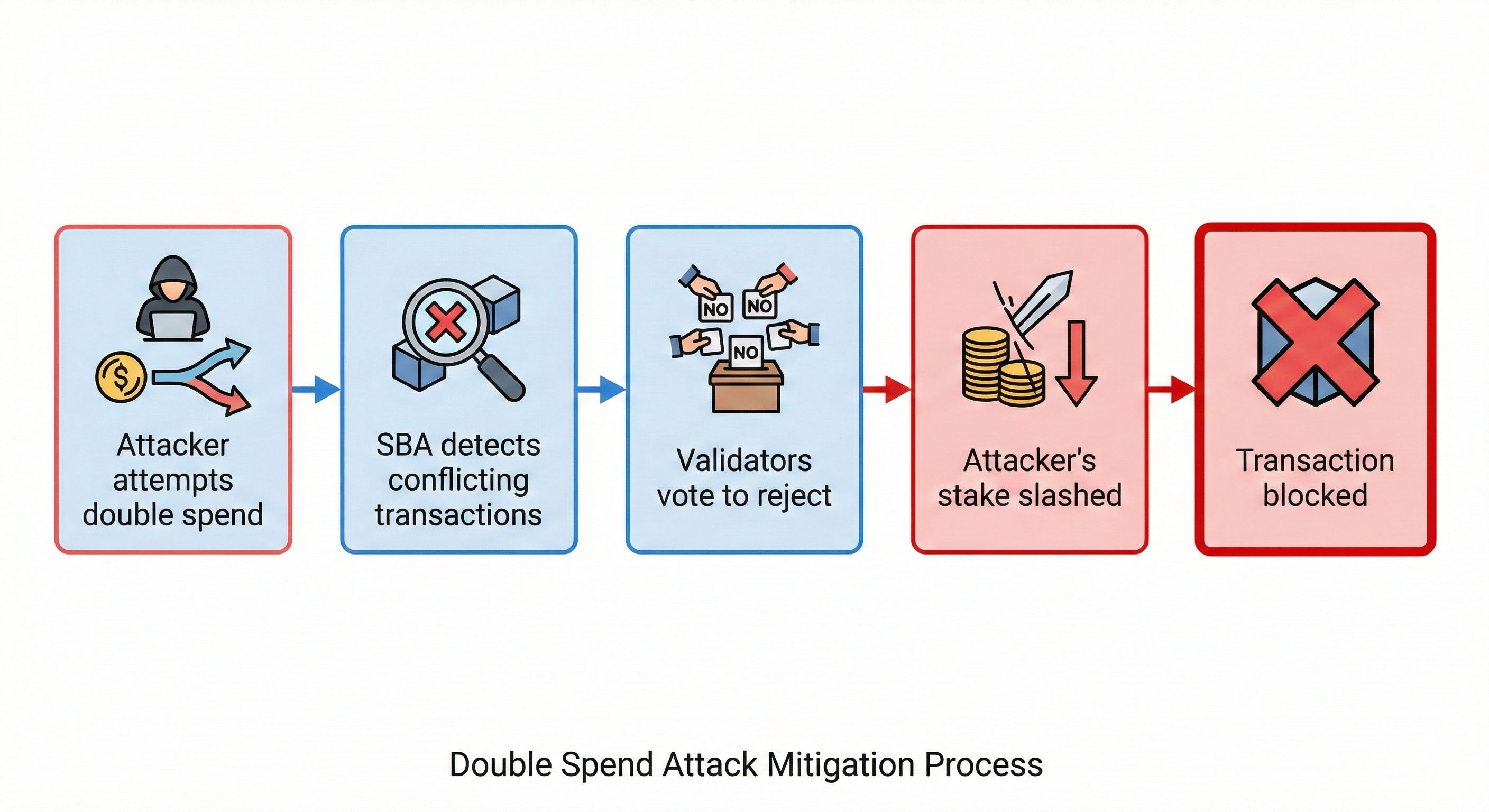
1. They broadcast two conflicting transactions
2. Multiple validators receive both transactions
3. Zero-knowledge proofs reveal the conflict without exposing details
4. The consensus mechanism rejects both transactions
5. The attacker's staked tokens are penalized
The system works because attacking costs more than any potential gain.
Why This Matters for Regular Users
You don't need to understand all the technical details. What matters is:
Your money stays safe: Double spending attempts fail automatically
Network stays honest: Sybil attacks become economically impossible
Privacy protected: Security doesn't compromise confidentiality
Fast transactions: Protection doesn't slow down the network
Dusk has essentially built a fortress where the walls get stronger the more someone tries to attack them.
The Bottom Line
Sybil attacks and double spending are serious threats that have destroyed other blockchain projects. Private networks face extra challenges because they can't rely on full transparency to catch bad actors.
Dusk Network's approach combines financial incentives, advanced cryptography, and clever consensus mechanisms to make attacks both technically difficult and financially stupid. It's like having a security system where breaking in costs more than everything inside is worth.
For businesses and users, this means confidence that their transactions and assets are protected by one of the most robust security architectures in the blockchain space.
Disclaimer: This post is for informational purposes only. It is not financial or investment advice. Cryptocurrencies are volatile and risky. Always do your own research (DYOR) before making any decisions.
