Dusk Network feels like it was built by people who actually understand why traditional finance still hesitates to move on-chain, because the biggest blocker is not speed or composability, it is exposure. In most public blockchains, every meaningful detail is broadcast by default, and in real markets that is simply not acceptable: positions, counterparties, trade sizes, treasury movements, issuance rules, investor eligibility, even the timing of transactions can become weaponized information. Dusk is trying to solve that exact contradiction by designing a Layer-1 where privacy is not a bolt-on feature you enable later, but a structural part of how value moves and how applications behave, while still keeping the system compatible with the realities of regulation, audits, and institutional workflows.
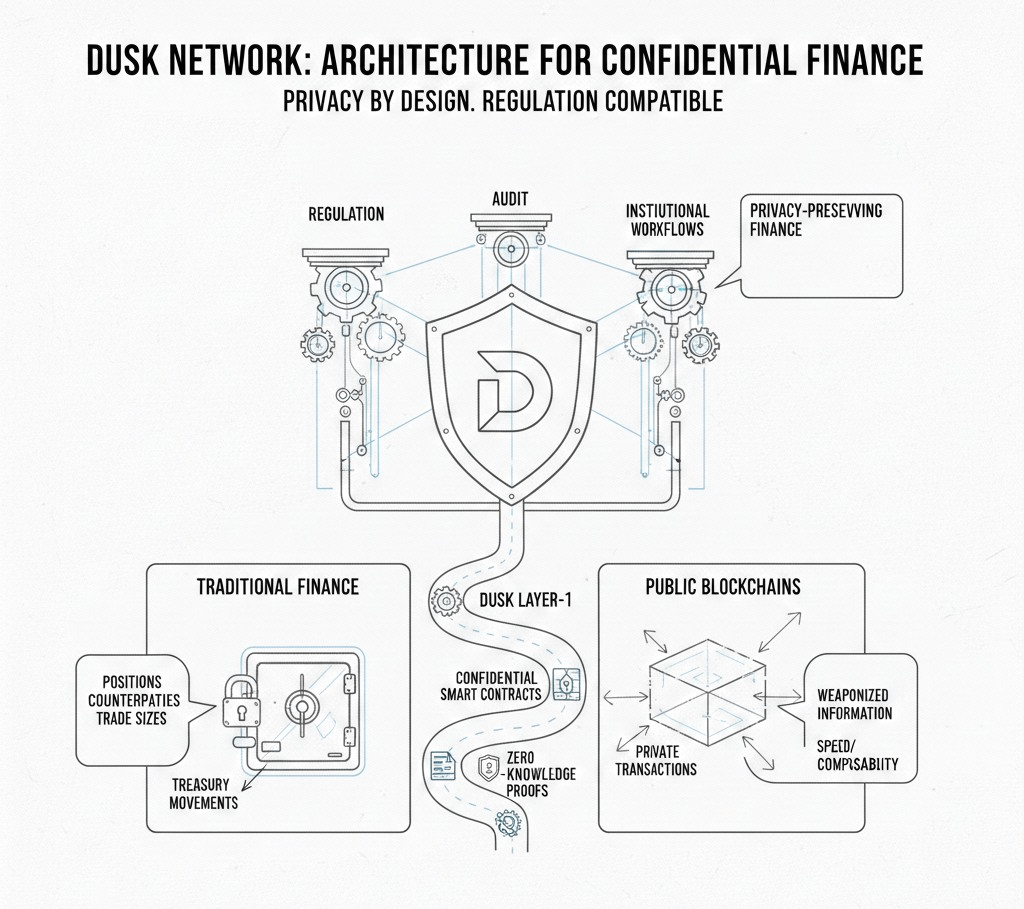
At the center of the project is the idea that “privacy” cannot mean “nothing can be checked,” because financial systems require verification, accountability, and rules, yet those rules do not require the public disclosure of every sensitive detail. Dusk’s direction is best described as confidentiality with verifiability, where the chain can validate correctness and enforce constraints without forcing users and institutions to reveal everything in plain sight. That philosophy shows up in the way the network models transactions, the way it approaches smart contracts, and the way it frames tokenized securities and identity as first-class concerns rather than side quests.
One of the most important parts of Dusk is that it does not force a single privacy mode onto every use case, because finance is messy and not every workflow wants the same level of disclosure. Dusk’s settlement layer supports a public-style model for transparent activity and a shielded model for confidential activity, which allows applications and participants to choose the right tradeoff for the situation. The public-style path is useful when transparency is expected or required, while the shielded path is meant for the parts of finance that cannot operate if everything is exposed. This dual capability matters because it makes Dusk more adaptable to real institutional requirements, where some data must remain private while some reporting must remain provable, consistent, and sometimes selectively revealable under proper permissions.
The project’s privacy approach is not limited to “private transfers,” because in financial systems the real value is often in private execution and private state, not just hidden balances. That is why Dusk’s roadmap and architecture increasingly emphasize confidential computation and compliance-friendly privacy within smart contracts. The project also leans into an EVM execution strategy so developers can build using familiar tools and patterns, while privacy and compliance primitives sit underneath as infrastructure. The practical meaning of this is that Dusk is trying to reduce the friction that usually kills privacy chains, where the technology might be impressive but the developer experience is too foreign, too expensive to learn, or too hard to integrate with the rest of the ecosystem.
Dusk’s strongest identity comes from its obsession with regulated assets and security-token style lifecycles, because tokenizing a regulated instrument is not the same as minting a fungible token and calling it an RWA. Real securities come with rules that must be enforced at the asset level, such as who can hold them, how transfers are restricted across jurisdictions, how corporate actions are processed, how voting works, how redemptions occur, and how compliance requirements are met throughout the lifecycle. Dusk talks in this language consistently, and its standards and components are aimed at making those workflows possible without exposing sensitive investor and market data to the entire internet. This is the kind of niche where a purpose-built chain can matter, because general-purpose chains often require complicated off-chain scaffolding to approximate these requirements, and that scaffolding is where complexity and risk accumulate.
Identity is another piece that Dusk treats as infrastructure rather than an afterthought, because regulated finance cannot avoid eligibility checks, but eligibility checks do not have to mean full doxxing or permanent on-chain identity leakage. The project has positioned privacy-preserving identity mechanisms as a way to prove attributes without revealing everything about the person, which aligns with the broader theme of selective disclosure and compliance-compatible privacy. The goal is not to erase regulation, it is to make regulated workflows possible while protecting users and institutions from unnecessary exposure.
Operationally, Dusk has recently shown the kind of reality that comes with building market infrastructure, which is that the “boring” parts such as bridges, service availability, incident handling, and safeguards can matter as much as consensus design and cryptography. They published a bridge incident notice in mid-January 2026, communicated that the core network was not impacted, and described mitigations and a cautious approach to resuming services. Whether someone reads that as a temporary setback or a sign of maturity depends on their bias, but in an institutional context, transparent communication and safety-first response are not optional behaviors, they are table stakes for credibility. At the same time, bridge disruption is never free, because liquidity routes and user flows depend on reliability, so the speed and clarity of follow-through becomes a practical measure of execution quality.
On the adoption and ecosystem side, Dusk has been tying its story to regulated market pathways and interoperability standards rather than purely retail hype, including an announcement linking Chainlink standards with a regulated exchange context through NPEX. The significance of that kind of move is not in the headline itself, but in what it implies: if regulated assets are issued and managed in a way that institutions can accept, then interoperability and standardized data become necessary, because institutions will not want to live inside one isolated chain forever, and compliant market data feeds and cross-chain settlement possibilities become part of the infrastructure conversation. In other words, these are the types of building blocks that point toward real financial usage patterns rather than short-lived narrative cycles.
When people talk about the token, it is easy to get lost in market chatter, so it helps to keep it grounded in what the system actually requires. The DUSK token, including the ERC-20 representation visible on Ethereum, is presented as the unit that powers network economics through fees and staking-style security participation, and its Etherscan page shows a maximum supply value of 500,000,000 and a holder count in the tens of thousands, which provides a basic snapshot of distribution surface rather than a full tokenomics story. The meaningful part of the token narrative is not the number itself, but the idea that if Dusk becomes a real settlement venue for confidential, regulated finance, then the token is not merely a speculative ticker, it becomes the fuel for execution and the economic glue for validators and participants. The market can ignore that for long periods, but infrastructure usage, if it arrives, tends to reshape the conversation from “price talk” to “utility pressure.”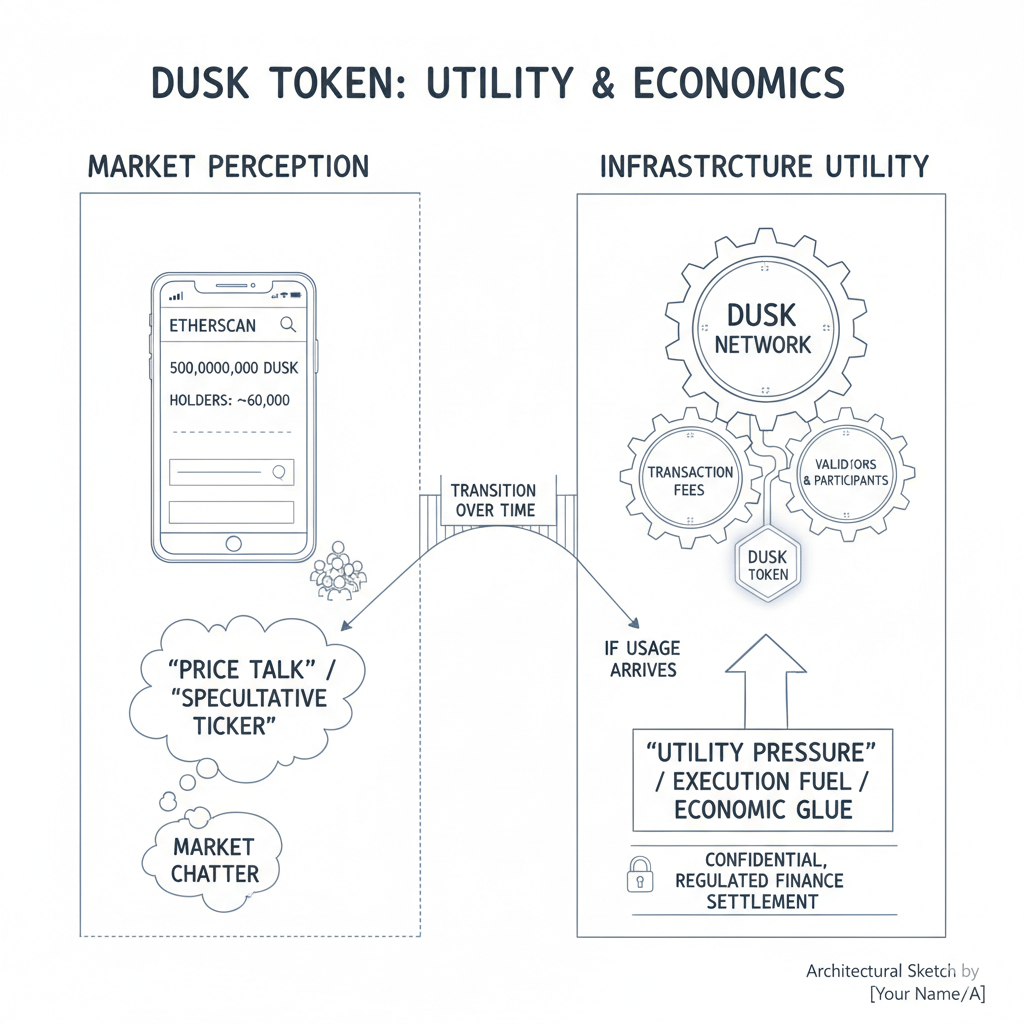
The way I would describe Dusk’s overall bet is that it is aiming for the slice of crypto where the winners will not be determined by the loudest memes or the fastest copy-paste apps, but by the chains that can satisfy institutional constraints without killing the benefits of programmability and composability. The project’s cohesion is its strength, because the same themes repeat at every level: confidential settlement, privacy-aware execution, identity and eligibility without overexposure, and standards for regulated assets that behave like the real instruments they represent. If Dusk executes, it will likely look “quiet” compared to retail-driven narratives, because regulated adoption arrives through pilots, compliance validation, integrations, and incremental scaling rather than sudden viral moments.