In what has become a alarming trend for the cryptocurrency sector, hackers affiliated with North Korea have stolen a staggering $2.02 billion in digital assets throughout 2025, setting a new annual record for the reclusive nation. This amount reflects a more than 50% increase compared to the previous year and elevates the total estimated thefts attributed to these actors since 2016 to approximately $6.75 billion, based on comprehensive data from blockchain analytics firm Chainalysis.
The broader cryptocurrency ecosystem experienced significant losses in 2025, with total thefts surpassing $3.4 billion from January through early December. North Korean-linked operations were responsible for a dominant share of these incidents, particularly those targeting centralized platforms.
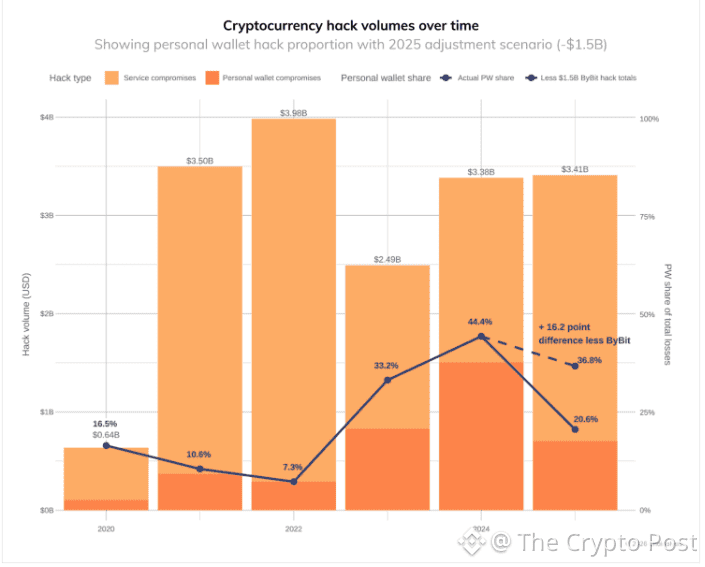
The most notable breach occurred in February when Dubai-based cryptocurrency exchange Bybit fell victim to a massive attack, resulting in the loss of around $1.5 billion—predominantly in Ethereum. This single event stands as the largest cryptocurrency heist ever recorded and significantly contributed to North Korea’s record haul.
Analysts and security experts emphasize that these illicit funds play a critical role in supporting North Korea’s nuclear weapons and ballistic missile programs, allowing the heavily sanctioned regime to circumvent international restrictions. “The reality is that cryptocurrency, because of its global 24/7 access, creates a unique value proposition for the regime to target,” Chainalysis head of national security intelligence Andrew Fierman said.
North Korean cyber operatives have demonstrated increasing sophistication, shifting toward fewer but higher-impact attacks. Tactics now frequently involve infiltrating cryptocurrency firms through fraudulent IT worker schemes—where operatives pose as remote employees—or more advanced social engineering, such as impersonating recruiters from prominent web3 and AI companies to extract credentials and access.
Laundering of stolen funds has also grown more complex. Hackers typically break proceeds into smaller transfers (often under $500,000), utilize cross-chain bridges, mixing services, and rely heavily on Chinese-language over-the-counter (OTC) networks and guarantee services to obscure traces and convert assets.
“Crypto heists have become ‘the easiest way for DPRK cyber actors to fund their regime,'” said Eun Young Choi, an attorney at Arnold & Porter and a former federal prosecutor with expertise in probing such cyberattacks. Choi highlighted how the growth in crypto adoption and market value has provided more lucrative targets for these state-backed groups.
Despite a reported decline in the number of confirmed incidents, North Korea was linked to a record 76% of compromises on centralized services in 2025. This efficiency underscores the regime’s patience and strategic focus on high-value opportunities.
Beyond centralized exchanges, the year saw a continued rise in personal wallet compromises, affecting an estimated 80,000 unique victims—nearly double the figure from a few years prior. While the total value stolen from individuals decreased slightly to around $713 million, the sheer volume of incidents reflects expanding risks as more people enter the crypto space.
In contrast, decentralized finance (DeFi) protocols experienced relatively suppressed hack losses despite recovering total value locked (TVL), suggesting improvements in security measures, rapid response capabilities, and governance tools that can mitigate or even reverse attacks.
As the cryptocurrency industry navigates policy advancements and market fluctuations, the persistent threat from nation-state actors like North Korea remains a top concern. With few effective deterrents due to existing sanctions, experts anticipate continued aggressive operations in the coming years.
This unprecedented year of crypto theft serves as a stark reminder of the vulnerabilities in digital assets and the need for enhanced security protocols, international cooperation, and vigilant monitoring to protect the evolving ecosystem.
