

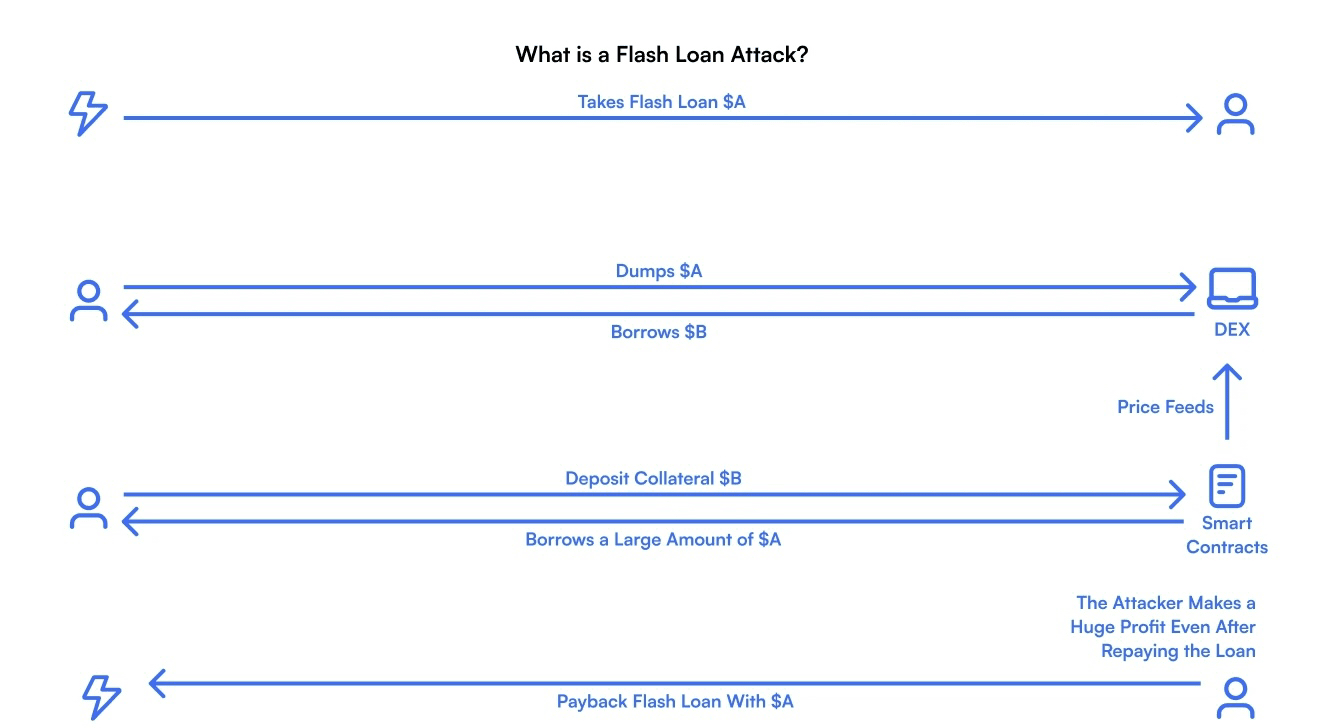
Flash loan attacks are often described as a problem of clever contracts and aggressive leverage. The narrative usually focuses on how attackers borrow large sums, manipulate a market briefly, extract value, and repay everything in a single transaction. This framing makes the attack look like a magic trick, something almost unfairly powerful. What it hides is the deeper truth. Flash loan attacks almost never succeed because smart contracts are weak. They succeed because data assumptions are weak.
Code does exactly what it is told to do. If a contract liquidates positions, rebalances pools, or settles trades, it does so because an input told it to act. That input is almost always oracle data. When attackers use flash loans, they are not really attacking contracts. They are attacking the system’s belief about reality.
APRO Oracle’s relevance becomes very clear when you shift your attention from execution to belief.
Flash loans amplify existing fragility. They do not create it. If a protocol’s oracle design assumes that short-lived price movements are meaningful, flash loans simply exploit that assumption at scale. If an oracle treats every observable price as equally trustworthy, attackers can manufacture observables cheaply.
This is why flash loan attacks feel sudden but are actually predictable. They target systems where data is treated as fact without context.
The typical flash loan oracle attack follows a pattern. Liquidity is thin on one or more venues feeding the oracle. The oracle updates frequently and mechanically. The protocol consumes updates immediately and irreversibly. None of these properties are bugs on their own. Together, they create a surface attackers can use.
Attackers do not need to sustain manipulation. They only need to cross thresholds briefly. Liquidation prices, collateral ratios, and invariant checks are binary. Once crossed, execution follows. The flash loan simply provides the temporary force needed to push prices across those boundaries.
APRO’s design philosophy addresses this pattern directly by challenging the assumption that all price movements deserve immediate belief. A price formed under stress, low liquidity, or abnormal conditions is not the same as a price formed in a stable market. Treating them as equal is what makes flash loan attacks possible.
Weak data design turns short-lived distortions into irreversible actions.
One of the reasons flash loan attacks remain so effective is that many oracle systems optimize for freshness above all else. The faster the update, the better it looks on paper. Freshness feels like accuracy. In reality, freshness without validation is noise.
APRO treats freshness as one signal among many, not the final authority. This reduces the effectiveness of flash loan manipulation because attackers rely on speed. They need the system to believe the manipulated price before markets normalize.
By requiring stronger confirmation before data becomes actionable, APRO raises the cost of attack. Attackers must sustain manipulation longer, across more venues, and under closer scrutiny. This changes the economics dramatically.
Another overlooked aspect of flash loan attacks is how they exploit human expectations. Users assume that if something happens onchain, it reflects a broader market reality. When positions are liquidated during flash loan events, users feel blindsided because they never observed the underlying conditions.
This is not just a financial issue. It is a trust issue.
APRO’s approach aims to align oracle behavior more closely with what users intuitively recognize as real market movement. When outcomes feel consistent with observable reality, trust survives even during losses.
Flash loan attacks also reveal how brittle reactive security models are. After each incident, protocols add patches. They add time delays. They add circuit breakers. These measures help, but they treat symptoms rather than causes.
The root cause is almost always the same. The system trusted data it should have questioned.
APRO’s preventive design reduces reliance on after-the-fact defenses by addressing trust at the data layer. Instead of trying to catch manipulation mid-execution, it reduces the chance that manipulated data becomes authoritative in the first place.
This distinction matters because automation is unforgiving. Once a flash loan transaction begins, everything happens atomically. There is no opportunity for human judgment. The only protection is prior design discipline.
From a quantitative perspective, flash loan attacks often involve surprisingly small net capital at the manipulation stage. The losses they cause are amplified by leverage and automation downstream. Reducing amplification therefore has a much higher return than chasing perfect detection.
APRO’s architecture is built around this insight. By dampening the system’s response to transient distortions, it limits how much damage a single manipulated signal can cause.
As DeFi grows more complex, flash loans are not going away. They are a natural consequence of composability. Trying to eliminate them is unrealistic. Designing systems that are resilient to them is the real challenge.
APRO’s oracle design accepts flash loans as part of the environment and builds accordingly. It assumes adversarial behavior and refuses to treat every data point as trustworthy by default.
This approach becomes even more important as oracles expand beyond prices. Event-based data, cross-chain signals, and real-world inputs can all be distorted briefly. Systems that react blindly will be exploited.
My take is that flash loan attacks are best understood as belief attacks. They succeed when systems confuse observability with truth. Oracle networks that make this mistake repeatedly will keep suffering the same failures under different names.
APRO Oracle’s emphasis on contextual validation and restraint directly addresses the conditions that make flash loan attacks profitable. By strengthening the data layer, it reduces the attack surface across the entire stack.
In a world where capital moves at machine speed, belief must be earned, not assumed. That is the lesson flash loan attacks keep teaching. APRO is one of the few oracle designs that appears to be listening.