Dusk is often framed as a privacy-focused blockchain, but the way it approaches privacy feels deliberately restrained rather than ideological. Instead of treating privacy as a tool for disappearance, the system seems designed around controlled disclosure, where sensitive information can remain hidden from the public while still being provable under structured oversight. This distinction matters, especially in contexts where auditors, institutions, or regulated entities need verifiability without full transparency.
The architecture reflects this pragmatic stance. Rather than compressing execution, settlement, and cryptographic privacy into a single environment, Dusk separates these concerns. The settlement layer is intentionally conservative, prioritizing reliability. The EVM layer is designed to be familiar, reducing friction for developers. The privacy execution environment handles the heavy cryptographic workload without forcing the rest of the system to inherit that complexity. This modular separation suggests an acknowledgment that different users require different guarantees, and that a single unified model often leads to unnecessary compromises.
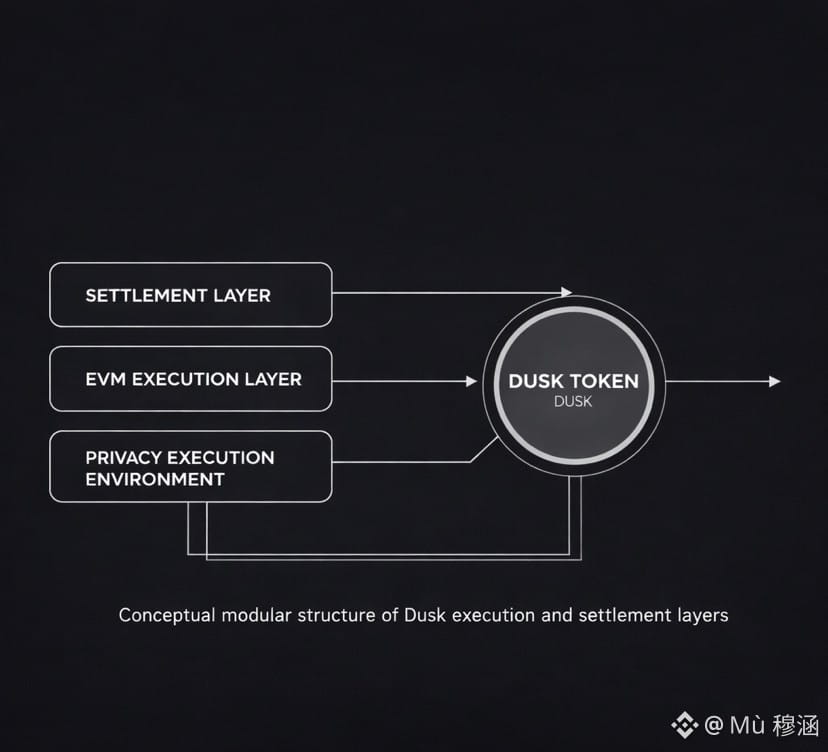
The role of the DUSK token within this structure is treated as infrastructural rather than decorative. It secures the network, pays for computation, and links the layers into a coherent system. From an institutional perspective, a single accounting and security token reduces operational overhead and simplifies internal processes, which can be more important than experimental design choices.
Dusk’s stance on multi-chain fragmentation is also notable. Instead of celebrating multiple wrapped representations across chains, the project treats fragmentation as a structural issue. The native chain is positioned as the authoritative ledger, with other networks acting as access points rather than peers. This mirrors traditional settlement models where a primary ledger exists and secondary systems reference it, which may align more closely with institutional workflows.
Operational behavior during stress events further reflects this mindset. During the early 2026 bridge incident, services were paused, infrastructure was rotated, and communication was direct. The response prioritized containment and process correction rather than narrative management. In regulated environments, such responses often carry more weight than uninterrupted uptime, as they demonstrate operational discipline.
Overall, Dusk appears to be optimizing for durability rather than visibility. The design choices emphasize predictability, auditability, and structured privacy rather than maximal anonymity or rapid experimentation. If successful, the system’s progress may look unremarkable on the surface steady usage, stable infrastructure, and privacy mechanisms that integrate quietly into institutional workflows rather than attracting attention.
