Summary: Trust Wallet suffered a major security breach when a compromised update (version 2.68.0) to its official Chrome extension maliciously harvested users' seed phrases, leading to the theft of approximately $7 million across multiple blockchains. The company has confirmed it will fully reimburse affected users.
Major Points Highlighted:
Nature of the Attack: A supply-chain attack on the official Trust Wallet Chrome browser extension (v2.68.0), not a phishing scam or user error.
Method of Exploitation:
The update contained a malicious JavaScript payload disguised as analytics code.
It silently captured and exfiltrated users' seed phrases to attacker-controlled servers as soon as they were entered or accessed.
Impact & Unprecedented Access:
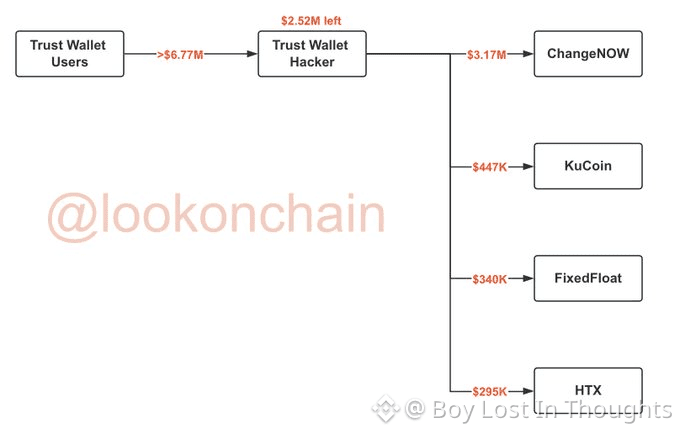
$7 million in user funds was confirmed stolen by Trust Wallet and founder CZ.
Attackers could drain wallets across all supported chains (Bitcoin, Ethereum, Solana, BNB Chain, etc.) without needing any further user interaction, approvals, or transaction signatures.
Timeline & Discovery:
The malicious update was released on December 24, 2025.
On-chain investigator ZachXBT first publicly linked the drains to the update, framing it as an extension compromise.
Trust Wallet confirmed the incident and urged users to upgrade to v2.69 on December 26, 2025.
Funds Movement:
Stolen funds were rapidly moved through instant exchange services (ChangeNOW, FixedFloat) and centralized exchanges (KuCoin, HTX) to launder the proceeds.
Response & Critical Issue:
Trust Wallet and Binance founder CZ committed to full user reimbursement for all losses.
A critical unresolved question is how a malicious build passed review and was published under Trust Wallet's official brand on the Chrome Web Store.
Scope:
Only the Chrome extension v2.68 was affected; mobile app users were not impacted.




