Bitcoin's Unbreakable Vault: The Mathematics of Cryptographic Security
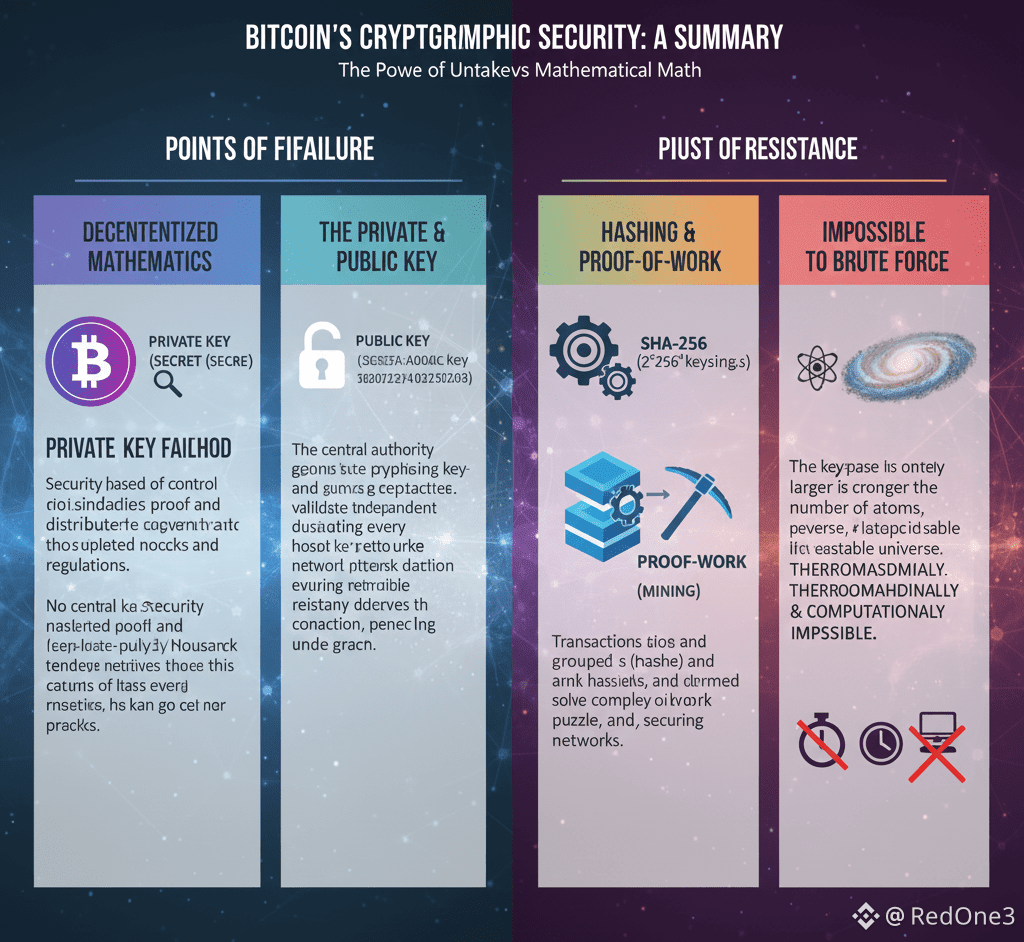
The foundation of Bitcoin's security lies not in firewalls or guarded servers, but in the immutable laws of mathematics, specifically through its use of cryptographic keys. Each Bitcoin wallet is secured by a pair of keys: a public address, which is shared openly to receive funds, and a private key, which is kept absolutely secret to authorize spending. The system's legendary security stems from the one-way nature of the Elliptic Curve Digital Signature Algorithm #ECDSA it employs.
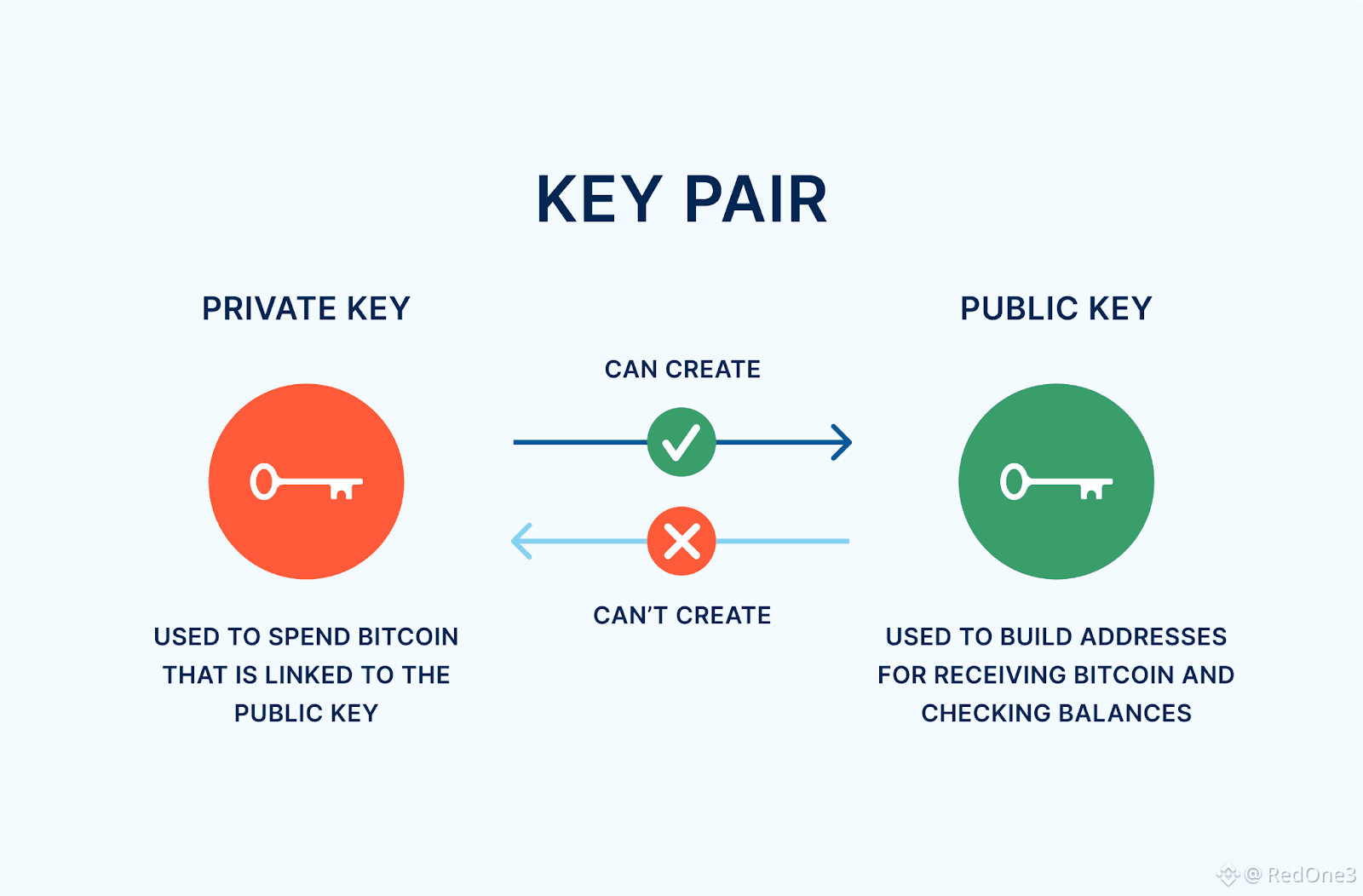
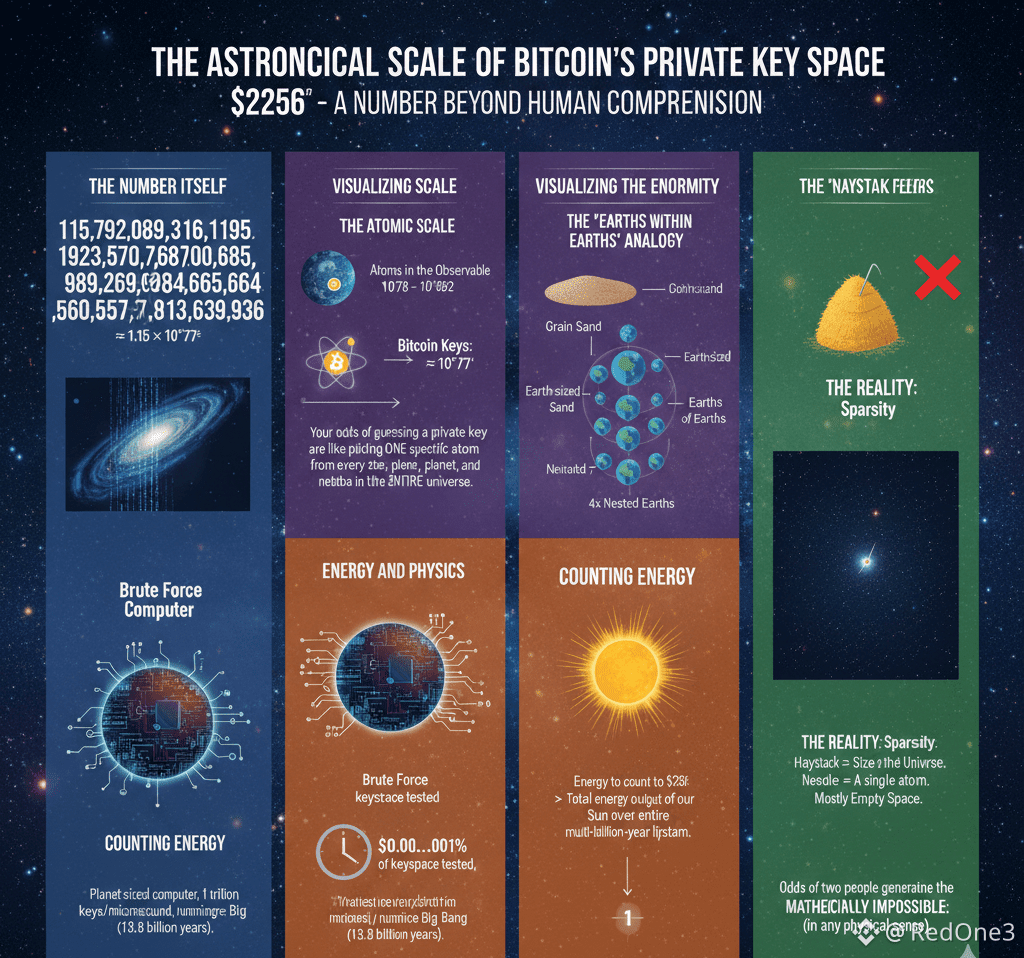
Generating a public address from a private key is a straightforward computational process. However, reversing this operation—deducing the #PrivateKey from its corresponding public address is designed to be computationally infeasible. The private key is an astronomically large random number, one of approximately 2^256 (or 10^77) possible combinations. To visualize this scale, this number far exceeds the count of all atoms in the observable universe.
Attempting to "guess" or brute-force a specific private key, like one belonging to the enigmatic creator Satoshi Nakamoto's early wallets, is an exercise in futility. Even with the combined computing power of every supercomputer on Earth running for billions of years, the probability of success remains effectively zero. This is not a matter of improving technology; it is a fundamental mathematical barrier. The energy cost alone for such an attempt would dwarf the global economy.
This cryptographic design creates a paradigm of true digital ownership. #CryptographicSecurity
Your Bitcoin is secured by mathematical proof, not by the permission of a bank or government. It cannot be confiscated through force or copied like a file—it can only be moved by the holder of the private key. #DigitalSignature
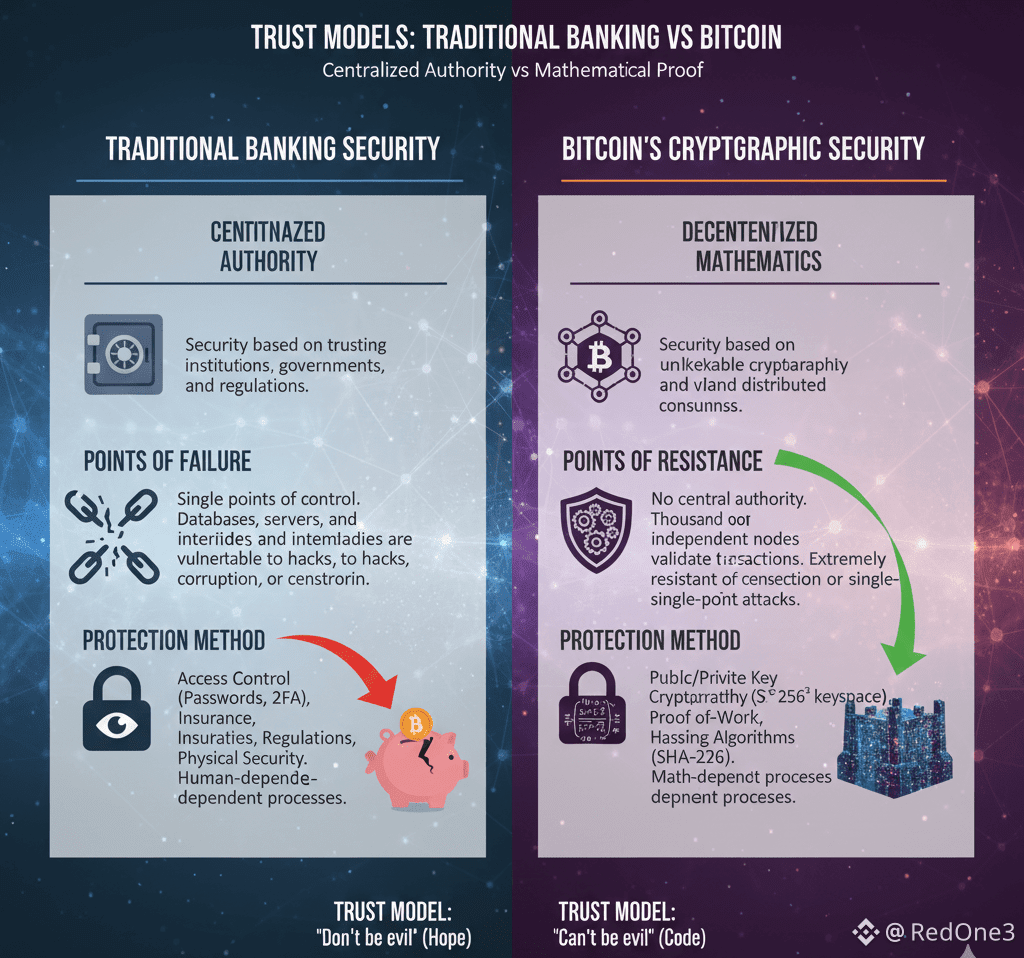
While users must guard against phishing, malware, and personal key mismanagement, the underlying protocol itself has remained impregnable since its inception. Satoshi's untouched fortune, likely locked in wallets with lost or deliberately unused keys, stands as the ultimate testament to this cryptographic strength.
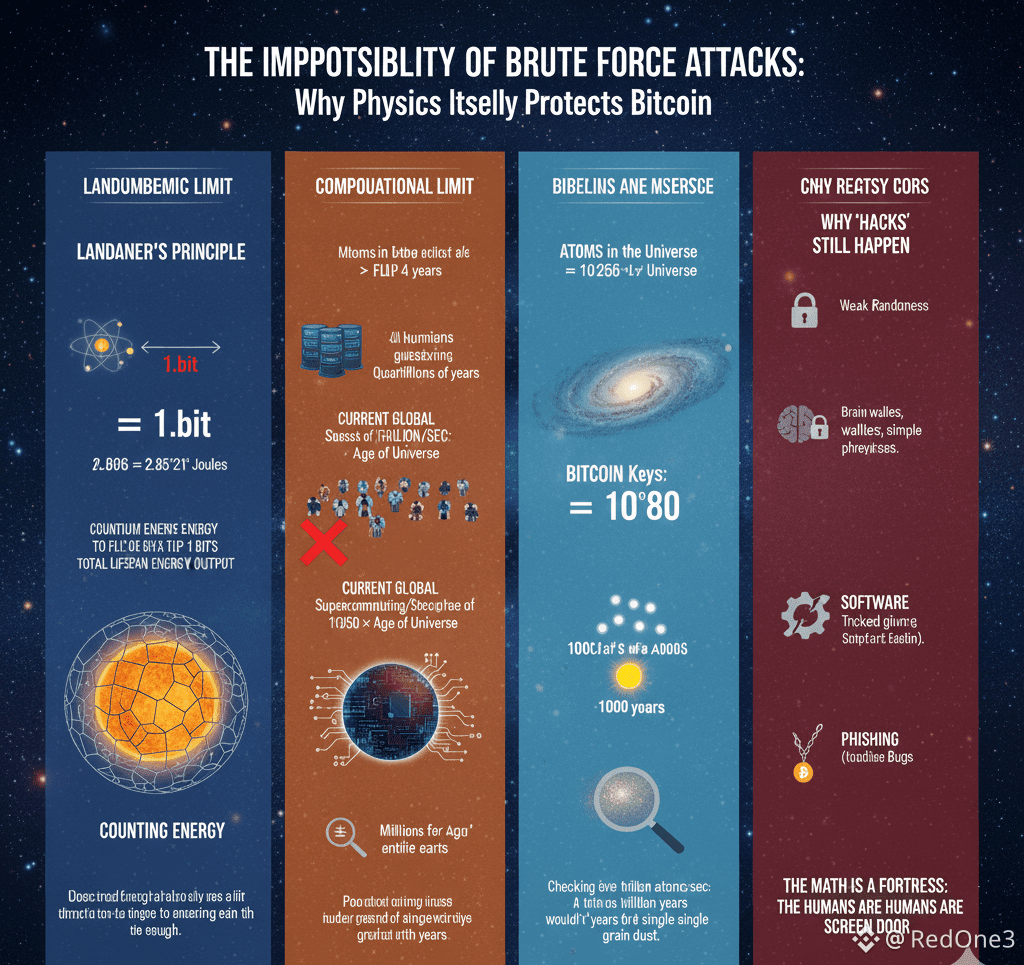
It proves that in the digital realm, mathematics can create a vault more secure than any physical one, establishing scarcity and ownership through pure, unbreakable code.