Azu thinks that AI payment has been destined to be a tug-of-war from the beginning: the regulators' intuition is 'don't connect the black box to the money,' while the developers' intuition is 'don't treat compliance as a development dependency.' The problem is that payments in the agency economy are not occasional transfers, but rather high-frequency, usage-based, and cross-service continuous settlements; as long as the scale increases, you cannot rely on 'everyone's self-discipline' to maintain order, so the regulators will definitely intervene, and the developers will definitely push back. KITE's ambition is actually to rewrite this tug-of-war from 'who wins and who loses' to 'both sides take a step back and still keep running.'
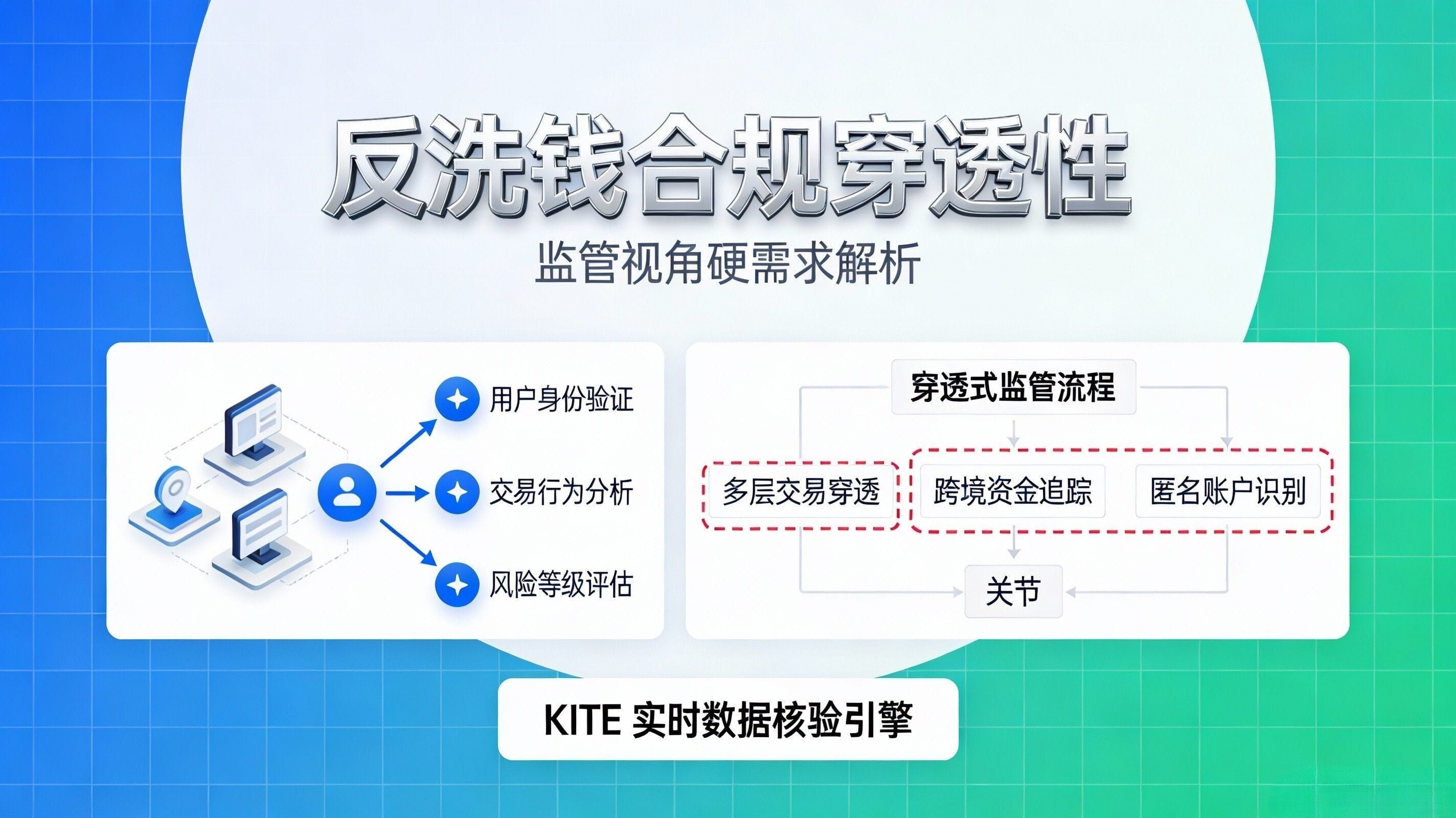
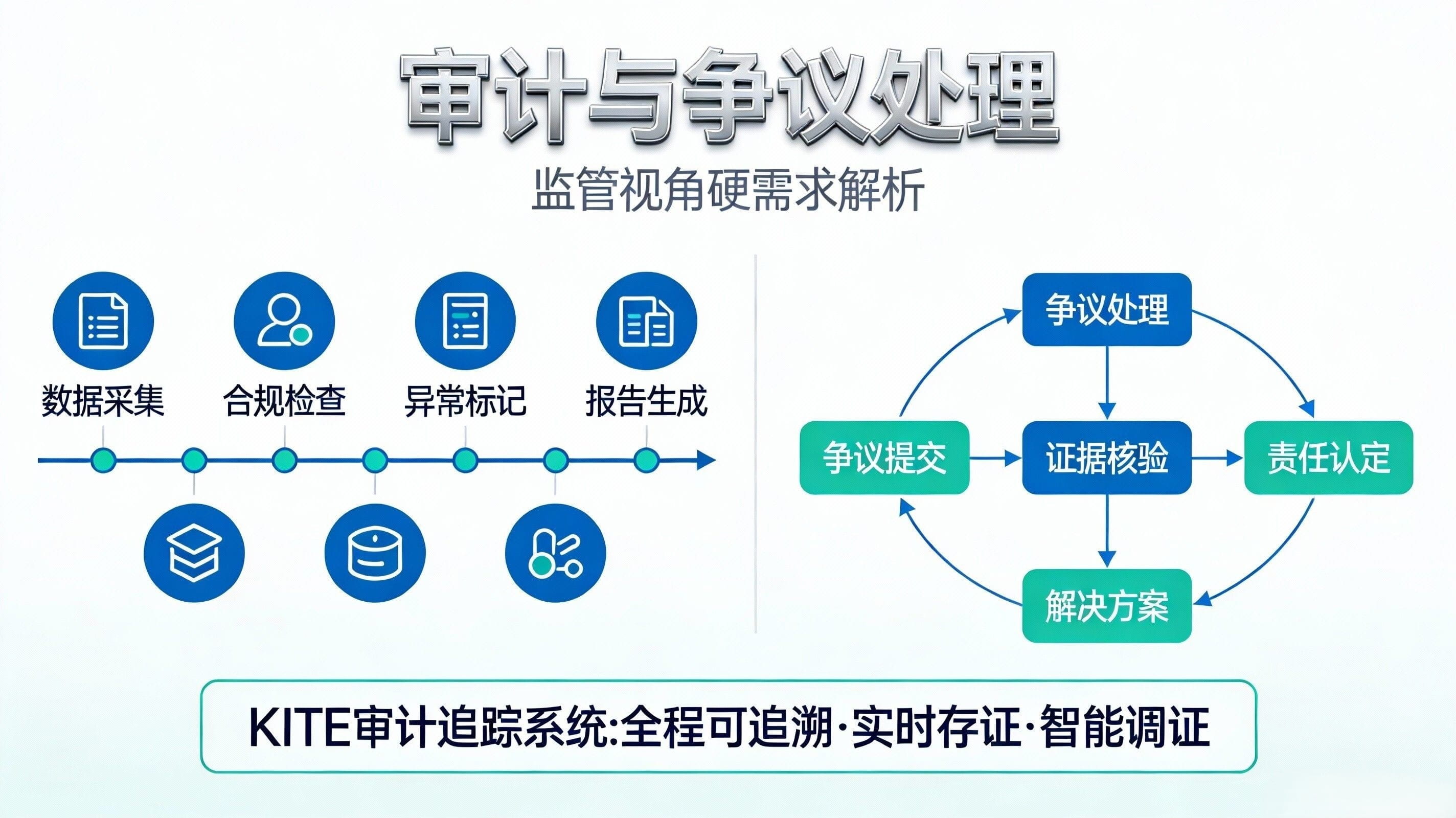
From the regulator's perspective, their concerns about AI payments typically do not revolve around 'on-chain innovation', but rather three hard issues: first, the transparency of anti-money laundering and sanctions compliance—you must be able to explain who authorized the money, why the agent can spend it, and where the money ultimately flows; second, the responsibility chain—who bears responsibility for bad debts, fraud, and mispayments, who can be held accountable, and who can quickly stop losses; third, audits and dispute handling—regulators and auditors do not want to see all your privacy, but rather want a replayable evidence chain that can link 'authorization → intent → execution → settlement → result'. At the same time, regulators will also have privacy requirements: it needs to be accountable, but cannot expose corporate secrets or user sensitive information entirely, this contradiction will force 'selective disclosure' to become a necessity.
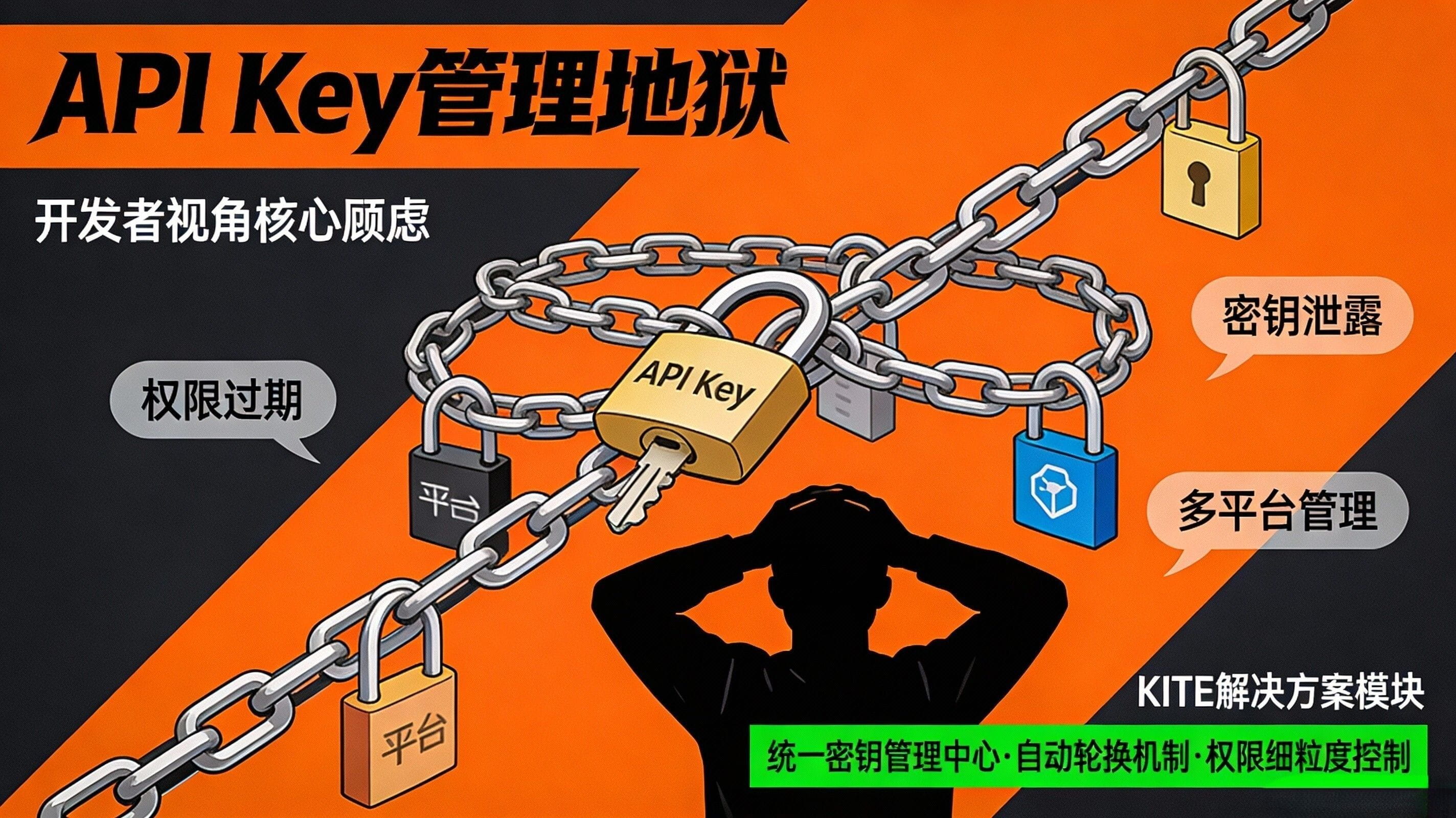
From the developer's perspective, the concerns are articulated in another language: they are not afraid of regulation itself, but of compliance turning the product into a 'crippled experience that requires manual confirmation for every call'. What they want is low-friction access methods, composable protocol interfaces, predictable costs and delays, and most importantly—don’t let 'API Key management hell' become a barrier to commercialization. To be more realistic, developers are also afraid of being locked into a single ecosystem: today you use A2A collaboration, tomorrow you use MCP interfaces, the day after you have to handshake with the enterprise system of OAuth 2.1. If the underlying payment track refuses to act as an 'interface envoy', then what you write is not a product but a migration cost.
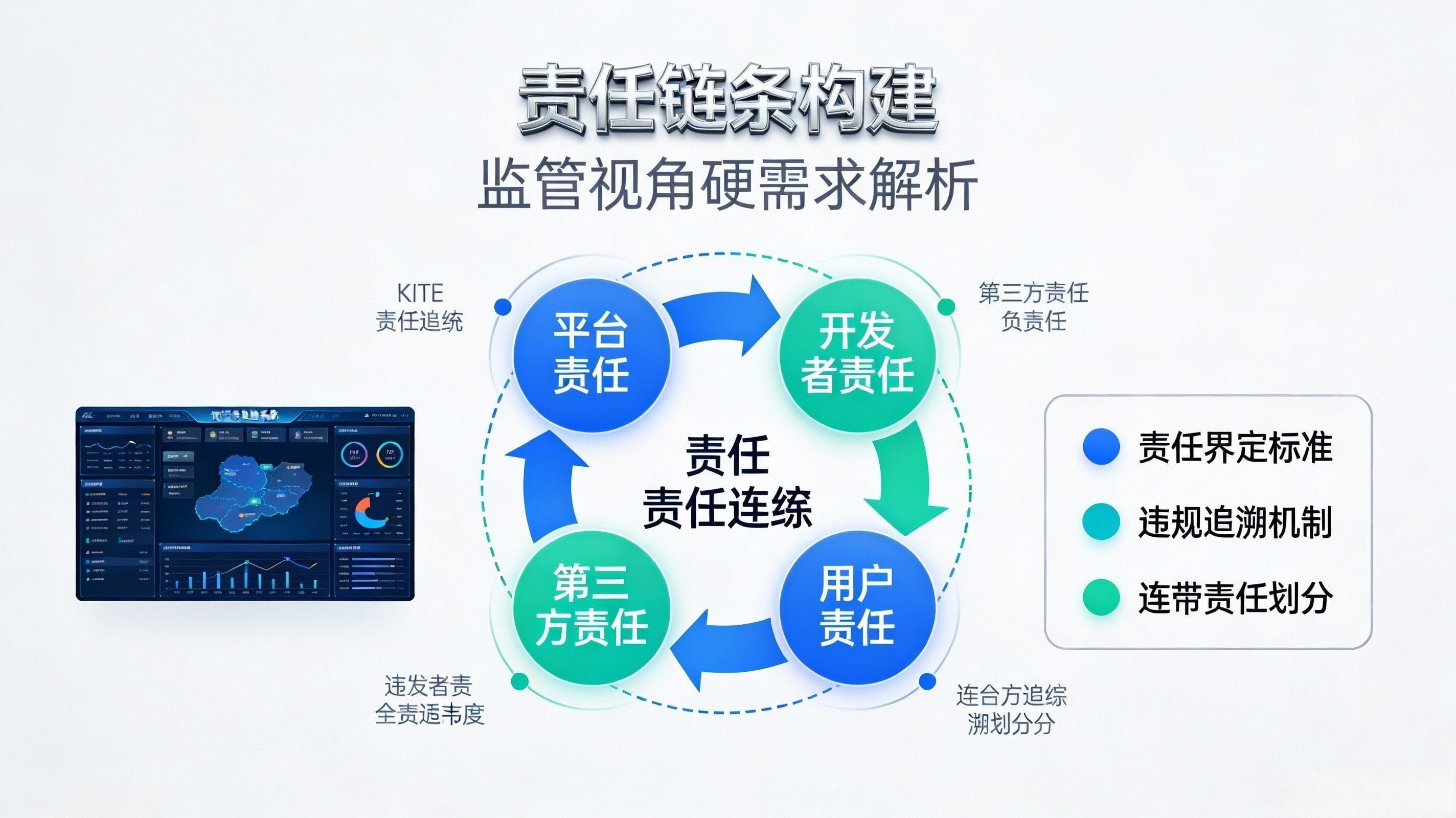
KITE attempts to provide a key handle for both sides to take a step back, as I understand it, by turning 'compliance' from external terms into internal primitives: using Kite Passport to bind the identity and capabilities of agents (how much they can spend, what services they can use) together, while also supporting selective disclosure, allowing agents to prove 'I belong to a verified entity' without exposing their full identity in every transaction; using DID/VC to structure 'who is who, who is allowed to do what', providing the responsibility chain required by regulators, and the minimal permissions required by developers; then using on-chain anchorable logs (referred to in official contexts as Proof of AI or similar auditable trails) to keep dispute handling and audit evidence in the system's default path, rather than forcing you to sift through chat records and bill screenshots afterward.
The clever part is that KITE does not pretend to replace all protocols; instead, it writes 'interoperability' into its architecture: the documentation clearly mentions native support for standards like x402 for agent payments, as well as bridging compatibility with A2A, MCP, OAuth 2.1, etc.—which means telling developers: continue using your familiar tools and collaboration protocols, I'll create reusable foundational components for 'payment, authorization, and audit'. For regulators, this design is also more acceptable because it naturally forms 'layered access': low-risk scenarios maintain smooth automation, while high-risk scenarios apply stricter thresholds using VC, whitelists, limits, and time windows, rather than a one-size-fits-all approach forcing everyone into KYC queues.
But Azu also doesn’t want to make promises too bold: whether regulators and developers can be satisfied simultaneously ultimately depends on where the boundary of 'taking a step back' is drawn. If regulators require full real-name identification and full visibility, then any selective disclosure will be crushed; if developers insist on completely no thresholds and completely uncontrollable, then any responsibility chain will be seen as 'betraying decentralization'. What KITE can do is more like providing a set of adjustable knobs: allowing the product to leave automation in low-risk zones, keeping the proofs and audits required by regulators in high-risk zones, and letting both use the same identity and payment primitives to connect, instead of having two systems fighting. Whether it can achieve the best of both worlds does not depend on slogans, but on whether truly scalable cases of 'whitelisted service providers + auditable receipts + minimal permission agents' can emerge in the ecosystem.
Finally, here’s a practical action guide for you: If you are a developer, don’t treat 'compliance' as UI copy from the start; treat it as a product stratification strategy—use small limits and short session permissions to run low-risk interfaces open to the public, and for high-risk interfaces involving funds, transactions, or corporate purchases, require VC/whitelisting. Make the x402 payment receipt and intent binding the default; if you are a team or enterprise user, treat the agent as an 'auditable digital employee'. First, set the budget envelope, service whitelist, and daily limits using Passport/policy sandbox, then gradually loosen permissions; if you care more about regulatory feasibility, focus on one thing: can every automatic payment be traced back to the 'authorization chain + intent + receipt + result'? If it can be traced, only then can we talk about 'having the best of both worlds'.

