Dusk Network lies a carefully designed interaction model that defines how users, institutions, and applications communicate with the protocol. Instead of exposing raw low-level operations, Dusk introduces a small but powerful set of core message types that structure all meaningful activity on the network. These actions-REGISTER, SEND, and CREATE-may look simple on the surface, but together they form the backbone of a private, programmable, and regulation-ready blockchain.
This design choice is intentional. Dusk is not built for chaotic experimentation or anonymous systems with unclear accountability. It is built for real financial use, where every interaction must be secure, verifiable, privacy-preserving, and compliant by design.
REGISTER: Entering the Network Privately
The REGISTER action is the gateway into the Dusk ecosystem. When a participant wants to join the network, they do not simply generate an address and broadcast it publicly. Instead, REGISTER allows the protocol to securely create a new account by generating a cryptographic key pair.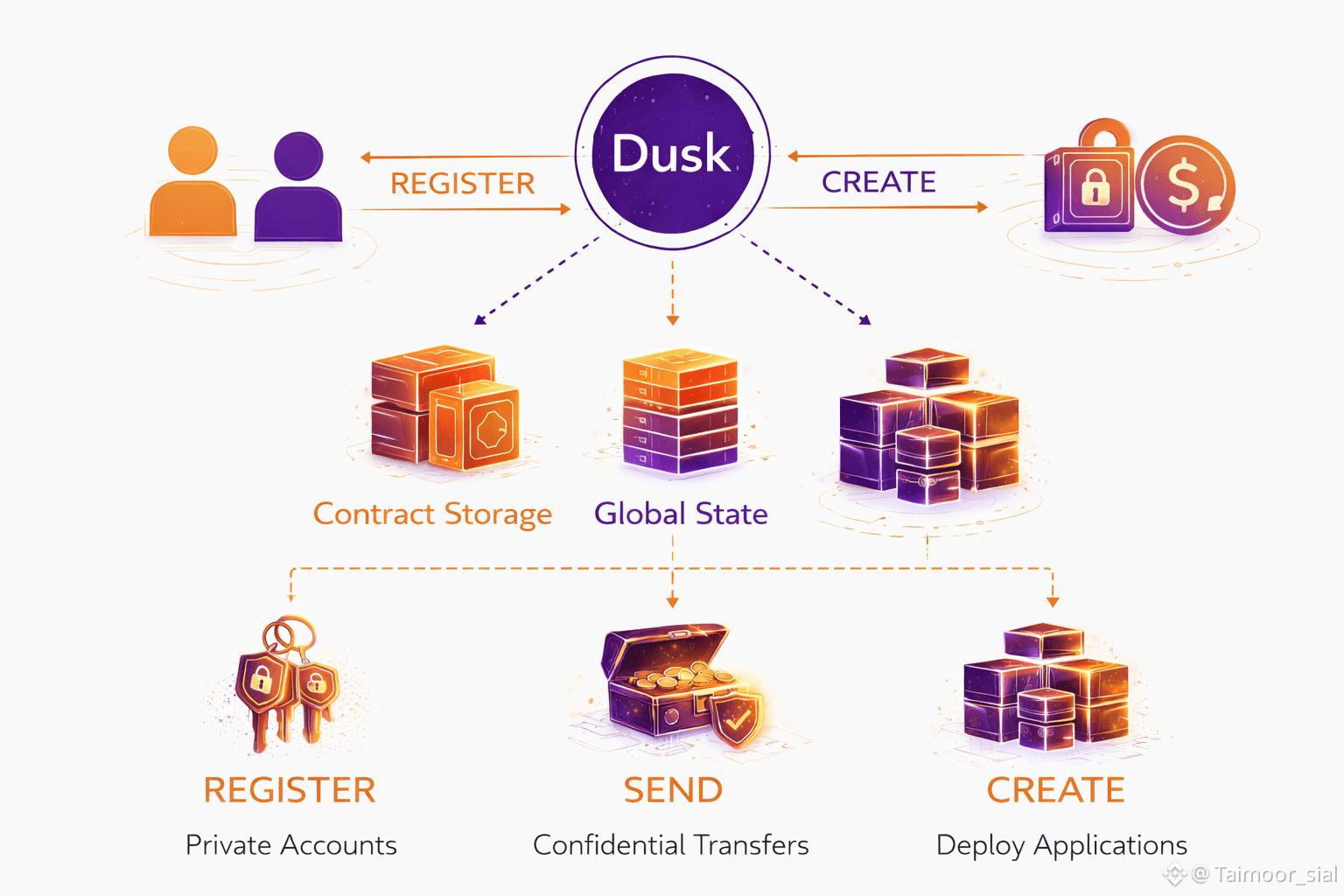
What makes this process unique on Dusk is that identity and account creation are separated from public exposure. Users can register without revealing personal data, wallet history, or external identifiers. The network only sees what it needs to verify correctness-nothing more. This allows Dusk to support privacy-preserving onboarding while still enabling future compliance workflows such as selective disclosure or private KYC when required.
For institutions, this matters deeply. It means accounts can be created under controlled conditions, audited when necessary, and integrated into regulated workflows without turning account creation into a public data leak.
SEND: Confidential Value Transfer
The SEND action handles the movement of native DUSK tokens between participants. On most blockchains, sending tokens exposes sender addresses, receiver addresses, amounts, and sometimes even behavioral patterns. Over time, this creates a transparent financial graph that can be analyzed, exploited, or surveilled.
Dusk takes a fundamentally different approach. SEND transactions are fully validated by the network but remain confidential in their internal details. The protocol verifies that the sender has sufficient balance and that the transaction is valid, without revealing balances, transaction histories, or wallet contents to the public.
This makes SEND suitable not only for retail transfers, but also for institutional use cases such as payroll, treasury management, settlement between counterparties, and asset movement within regulated environments. Value can move on-chain without turning the ledger into an open financial database.
CREATE: Deploying Privacy-Aware Applications
The CREATE action enables users and developers to deploy applications on the Dusk Network. These applications are not limited to simple transfers; they can represent complex financial logic such as tokenized securities, voting systems, dividend distribution, compliance rules, and lifecycle management of assets.
What distinguishes CREATE on Dusk is how it handles state visibility. Applications can interact with one another and expose non-sensitive state where appropriate, but specific operations—such as asset transfers, ownership checks, voting results, or dividend claims—can remain private. This allows applications to be both interoperable and confidential.
In practice, this means developers can build systems that behave like traditional financial infrastructure, where only authorized parties see sensitive data, while the network still enforces correctness and integrity.
A Unified Interaction Model for Real Finance
By limiting protocol interaction to REGISTER, SEND, and CREATE, Dusk achieves clarity without sacrificing power. Every action is intentional, auditable, and compatible with zero-knowledge verification. There are no hidden shortcuts or undefined behaviors.
This interaction model also makes Dusk easier to reason about from a regulatory and security standpoint. Authorities, auditors, and institutions can understand what actions exist, what they do, and how they are enforced-without needing to compromise user privacy or protocol integrity.
Most blockchains expose too much by default. Dusk does the opposite. It exposes only what is necessary, and nothing more. REGISTER protects identity, SEND protects value flow, and CREATE protects application logic. Together, they allow Dusk to support private users, institutional finance, and compliant on-chain systems within a single coherent framework.
This is not just protocol design-it is infrastructure design for the next generation of blockchain adoption.
