It was a tiny change.
So ordinary it almost felt insulting.
I opened @Walrus 🦭/acc to upload a blob I’d been sitting on for weeks — nothing dramatic. A compressed archive of private work notes, a handful of API logs, and some old wallet exports I didn’t want living unencrypted on my laptop anymore. When the interface loaded, everything looked familiar.
Except for one line.
Tucked beneath the storage panel, barely noticeable, was a quiet reminder:
“Encryption keys are session-scoped.”
Most people would scroll past that.
I almost did.
But the phrase stuck with me longer than it should have. Session-scoped. Not account-scoped. Not wallet-scoped. Just… session. The kind of word that subtly suggests you’re not meant to rely on permanence.
I uploaded the file, paid the WAL fee, and watched the progress bar inch forward. Walrus did what it always does — split the data, apply erasure coding, distribute the fragments across its decentralized storage network on Sui. Elegant engineering, sure.
But my mind wasn’t on architecture.
It was on a much more human question.
What happens if I mess up?
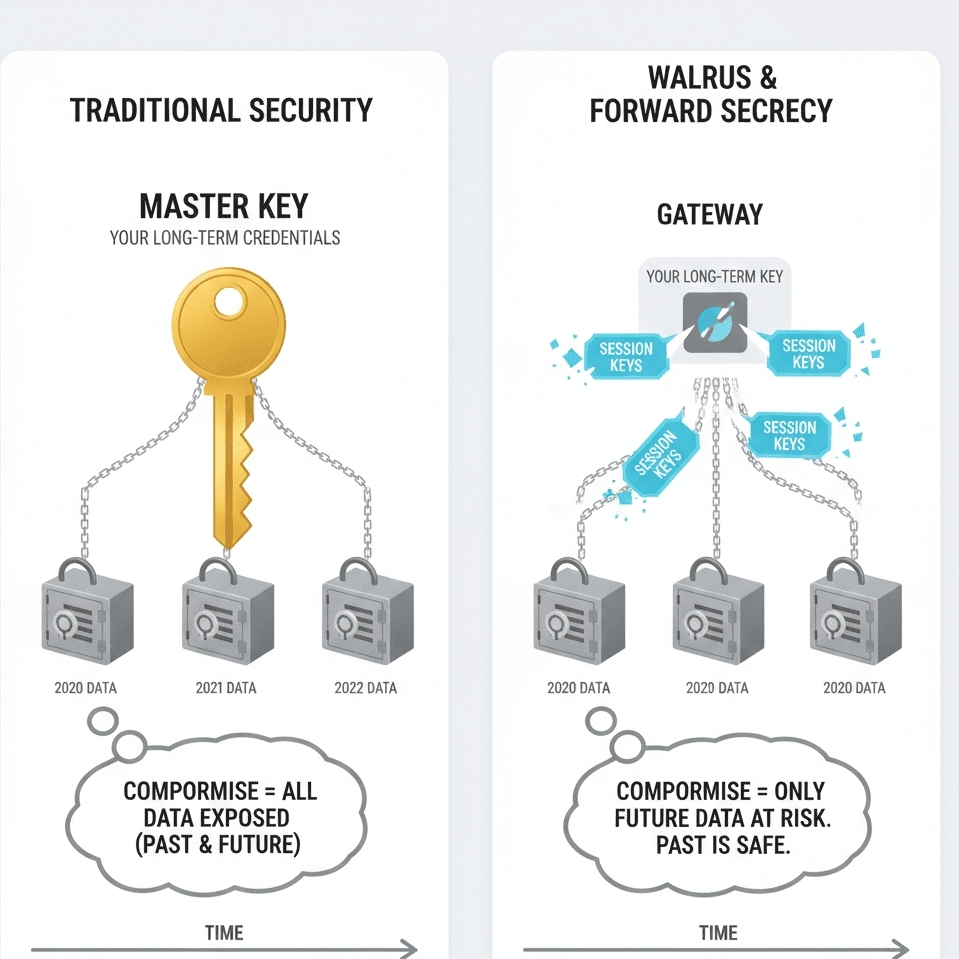
Not the harmless kind of mistake — not a misclick or a wrong setting. The real one. The nightmare scenario. The day your long-term key is compromised. Your seed phrase leaks. Your hardware wallet gets stolen. Your signing device turns out to be infected.
The kind of mistake that doesn’t just cost money.
It costs history.
Because in most systems, when someone gets your key, they don’t just gain access to what you’ll do next. They gain access to what you already did. Your past opens up. Every file you stored. Every transaction you assumed was private. Every moment you believed was safely behind you.
That’s the unspoken danger of long-lived keys.
They don’t just authenticate you.
They become time machines.
So I did something uncomfortable.
I imagined my key being stolen.
I pictured a stranger holding my long-term credentials, staring at Walrus like a vault door that had finally been left ajar. And that’s when the realization landed, heavy and unsettling: if a system relies on a single persistent encryption key, then compromise doesn’t mean “I’m vulnerable now.”
It means I was vulnerable the entire time — I just didn’t know it yet.
That’s when forward secrecy stopped feeling like a cryptography term and started feeling like a survival instinct.
Walrus doesn’t assume your key will stay clean forever.
It assumes the opposite.
It assumes that one day, something will leak.
So instead of encrypting stored blobs with a static, reusable key tied to your identity, Walrus leans on ephemeral session keys — fresh keys generated for specific interactions, meant to live briefly and then disappear.
Your long-term key becomes a gate, not the lock itself.
It can authorize access, but it isn’t the master secret protecting everything you’ve ever stored.
Each blob can be encrypted with its own symmetric key. That key can be derived or wrapped through ephemeral exchanges that don’t repeat. Even if your long-term credentials are compromised later, the attacker doesn’t automatically inherit the ability to decrypt your old data.
Because the keys that mattered were never meant to survive beyond their moment.
And the network doesn’t make it easy to cheat.
Walrus storage isn’t a single server holding a neat encrypted file. It’s fragments scattered across decentralized blob storage, distributed with erasure coding. Even if someone gathers pieces, what they get is still locked behind encryption that was never designed to be timeless.
That’s what forward secrecy feels like in practice.
It’s your past refusing to be rewritten.
It’s not dramatic.
It doesn’t announce itself.
It doesn’t flash across the UI with a celebratory banner.
It sits quietly in a line of text — “session-scoped” — and waits for the day you realize why it matters.
Because the real promise was never that your key would stay safe forever.
The real promise is this:
If it doesn’t, the damage doesn’t travel backward in time.