Azu is here, brothers. After writing for so long, I want to change to a more 'on-site perspective': Don't treat KITE as another new chain, but as a set of 'default security configurations' prepared for the era of agents. Because once AI agents start running their own business, the first thing that drags you down is often not throughput, nor Gas, but that familiar feeling of helplessness—who granted the permissions, who approved the quotas, whose accounts need to be reconciled, and who takes the blame when something goes wrong. What KITE is trying to do is to turn these issues from 'compliance modules added after product launch' into 'underlying primitives that can be called during development' ahead of time.

Traditional developers rely on a patchwork for risk control: account systems, OAuth, KYC service providers, anti-fraud, billing systems, audit reports, and finally adding a 'don’t overspend' backend permission. The problem is, agents are not just 'faster fingers' of human users; they are execution entities that can make parallel service calls, negotiate, and continuously pay. The ideas provided by KITE in the documentation are straightforward: the platform layer uses 'agent-oriented APIs' to push the complexity of the chain to the back, allowing developers to directly obtain capabilities like identity management, authorization, payment processing, and even SLA execution, including session key generation and management, state channel opening and settlement, etc. It sounds like engineering details, but fundamentally it is providing an auditable process framework for 'machines spending money'.
What I care most about, 'default security configuration', is actually hidden in the design of KITE Passport. The official describes it as a type of encrypted identity card: it not only proves 'who you are', but also writes into the capability boundaries 'what you can do, how much you can spend, which services you can access', and it can even do selective disclosure, allowing you to prove compliance or hold certain permissions without having to hand over your entire privacy. In simple terms, this is a way to shift permissions from backend management pages to cryptography—agents must first reveal their 'driver's license + credit limit' on-chain before taking action.
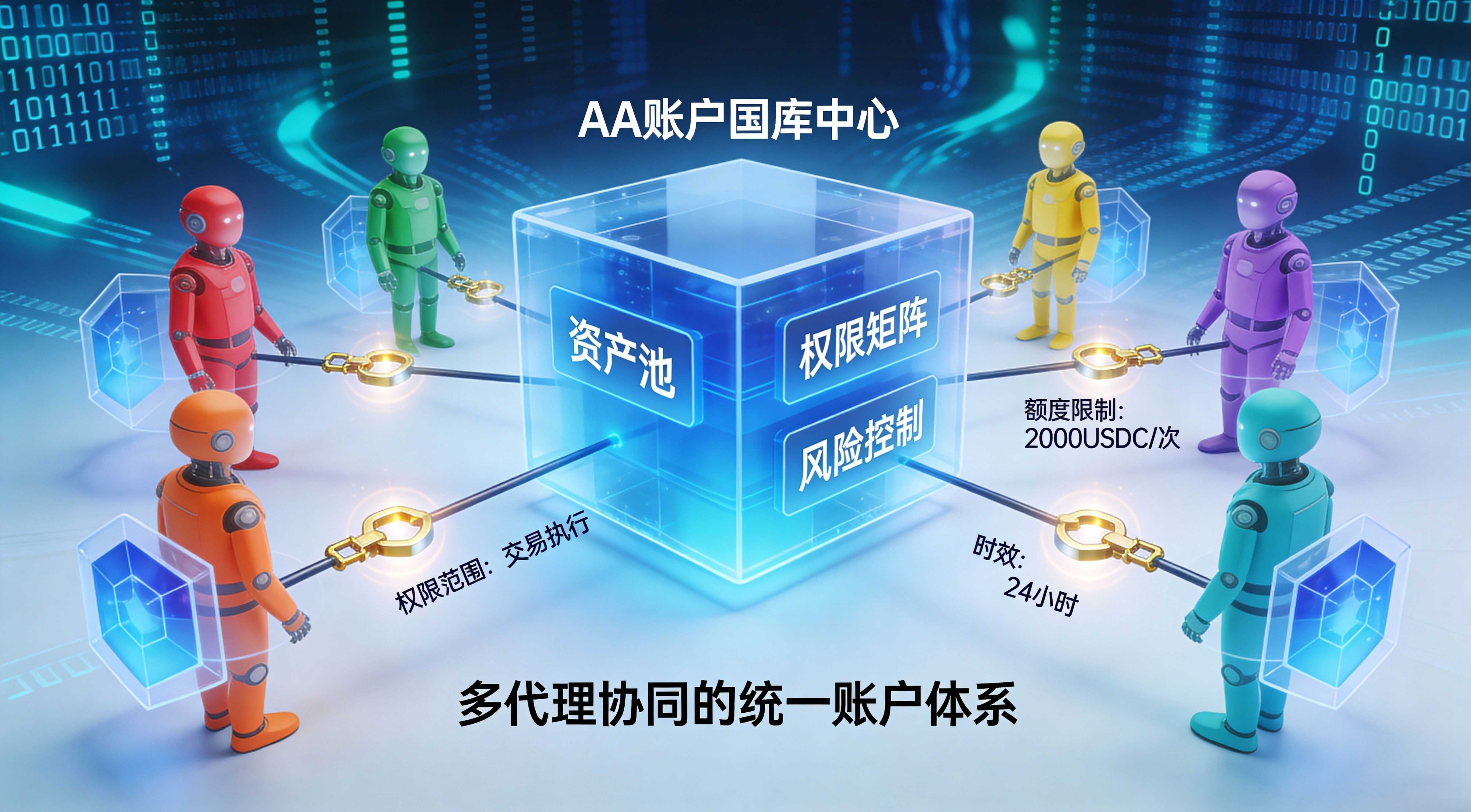
Looking further down, KITE is also pushing developers not to 'manage their own money and bear their own burdens'. The documentation mentions a unified account model: users hold a stablecoin fund pool on-chain with an AA account, different agents operate within a limited scope using their own session keys, sharing the same treasury. However, each session isolates risks, and permission boundaries are auditable. If issues arise, you can clearly delineate responsibilities along the authorization chain, rather than playing hide and seek among a bunch of API keys, sub-accounts, and invoices.
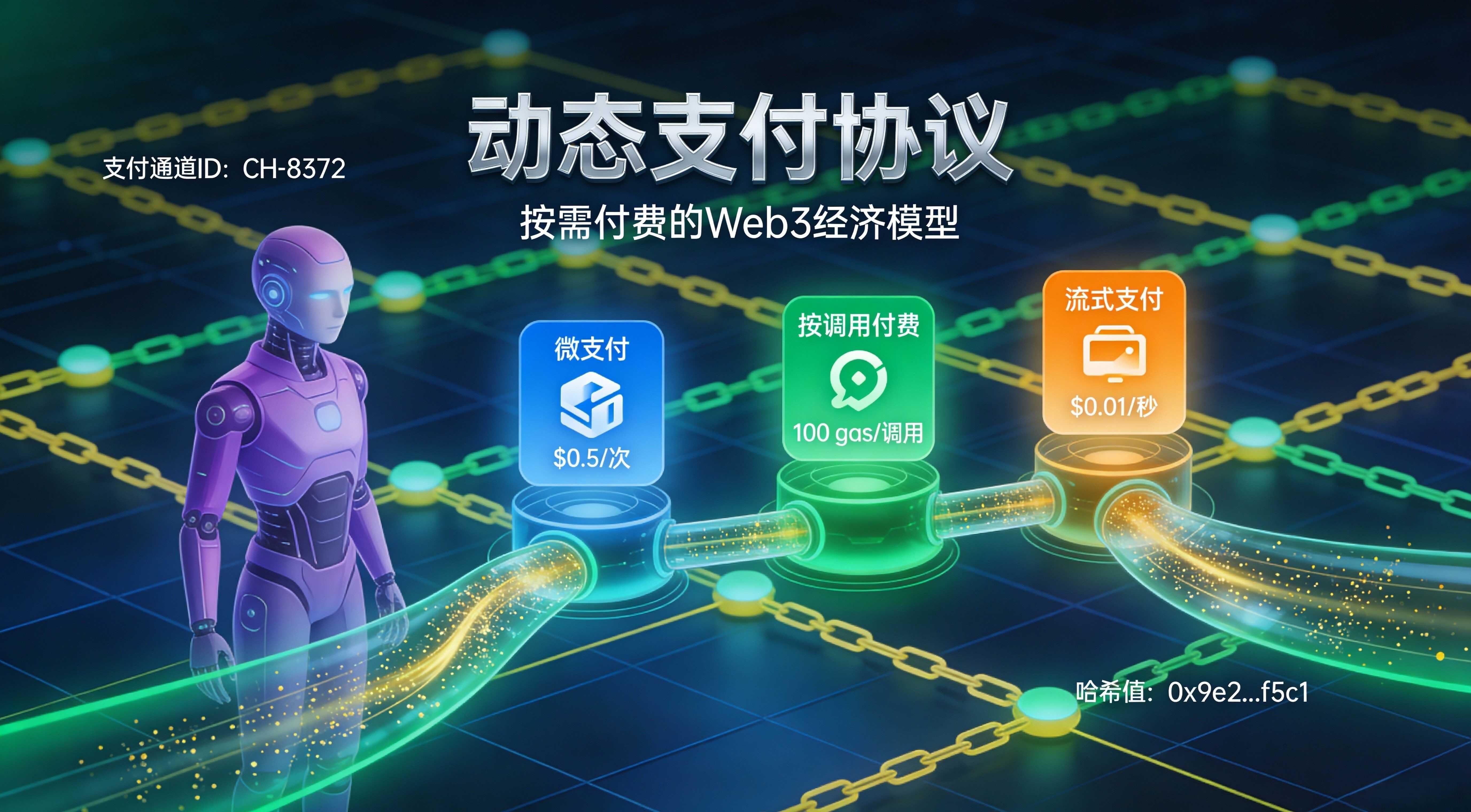
Then there is the payment itself. KITE has written the 'agent payment protocol' into a set of expressible capabilities: micro-payments to tiny units, pay-per-call, streaming payments, conditional payments, instant settlements, combined with state channels that are closer to high-frequency calls, aiming to make 'every API interaction can carry value settlement' a reality beyond just being on a PPT. You will find that this directly changes the compliance mindset of developers: you no longer just need to 'prevent fraud', but you need to ensure 'every payment has a replayable authorization basis'.
If you're looking for a more practical 'toolbox feel', I would break it down into three parts, but I won’t write it as a list; you can align it in your mind: the first part is a runnable development path, with the official standard process for Solidity contract development, supporting Remix and Hardhat, and presenting full-stack examples of 'how to go from contract to front-end' directly. Familiar tools like React + Ethers.js + wallet connections can still be used; the second part is a reusable modular framework on-chain, where they manage 'AI assets' like models, datasets, proxies, and services as first-class citizens, while incorporating production-grade components like resource monetization, cost allocation, role permissions, factories, and registries into the framework; the third part is a list of directly usable contracts and components, such as the ERC-4337 account abstraction wallet contract, factory contracts, and service registries prepared for service discovery and pricing models. You don’t have to use everything, but at least you don’t have to invent a set from scratch.
The 'compliance toolbox' also serves as a means for debugging and auditing. The KITE documentation provides access to the testnet's block explorer and multi-signature wallet, which can be understood as two bottom lines: one allows you to see what is happening on-chain, while the other ensures that critical operations are never reliant on single-point signatures. Meanwhile, they emphasize in the security chapter the shift-left security processes, layered defenses, least privilege and zero trust, as well as practices like multi-signatures and independent audits. This expression certainly does not equate to 'always secure', but at least it tells developers: this chain expects you to treat security acceptance as a threshold for going live from the design stage, rather than patching up public relations after an accident.
By the way, if you are from the Python ecosystem, there is a Python SDK named gokite on PyPI, which introduces itself as a tool for interacting with the Kite Network, covering capabilities like identity management, wallet operations, and on-chain payments; I won’t vouch for it without running the code, but at least it shows they are trying to make the 'on-chain' experience suitable for data scientists.
The rule change can actually be summed up in one sentence: in the era of agents, compliance is no longer about 'adding a backend after going live', but rather 'the authorization chain must be provable before a transaction occurs'. When identity, session keys, quotas, and service access rights can all be expressed cryptographically, risk control shifts from 'manual review + post-event accountability' to 'default guardrails + revocable during the process + replayable afterward'.
The impact on ordinary users is very real: you will be more willing to entrust money to agents because you see not only 'it's smart', but also 'what it's allowed to do and what it can't do'; the impact on developers is even more direct: you will write fewer pieces of fragile permission glue and use a set of auditable authorization primitives to define product boundaries.
My action guide is simple: if you are already doing API, SaaS, data services, or any 'pay-per-call' business, don’t rush to treat KITE as a public chain to study; treat it as a 'programmable billing + provable authorization' toolbox to experiment with. First, go to the testnet to get the browser and wallet running, follow the documentation to run a minimal dApp or contract example, and then pick out the most challenging permission logic from your current product—such as quotas, whitelisted services, or session key revocation—and try to express it again using the Passport/AA approach. Once you complete this step, you will know whether this is the direction you should bet on.

