Recently, the globally renowned blockchain media Cointelegraph published a special report titled (Meet the onchain crypto detectives fighting crime better than the cops), focusing on on-chain detectives and researchers in the crypto security industry. Cos (余弦), the founder of SlowMist, was one of the interviewees, sharing the team's handling processes in major security incidents, product system, and observations on the industry's security landscape.

Speed is the top priority for safety
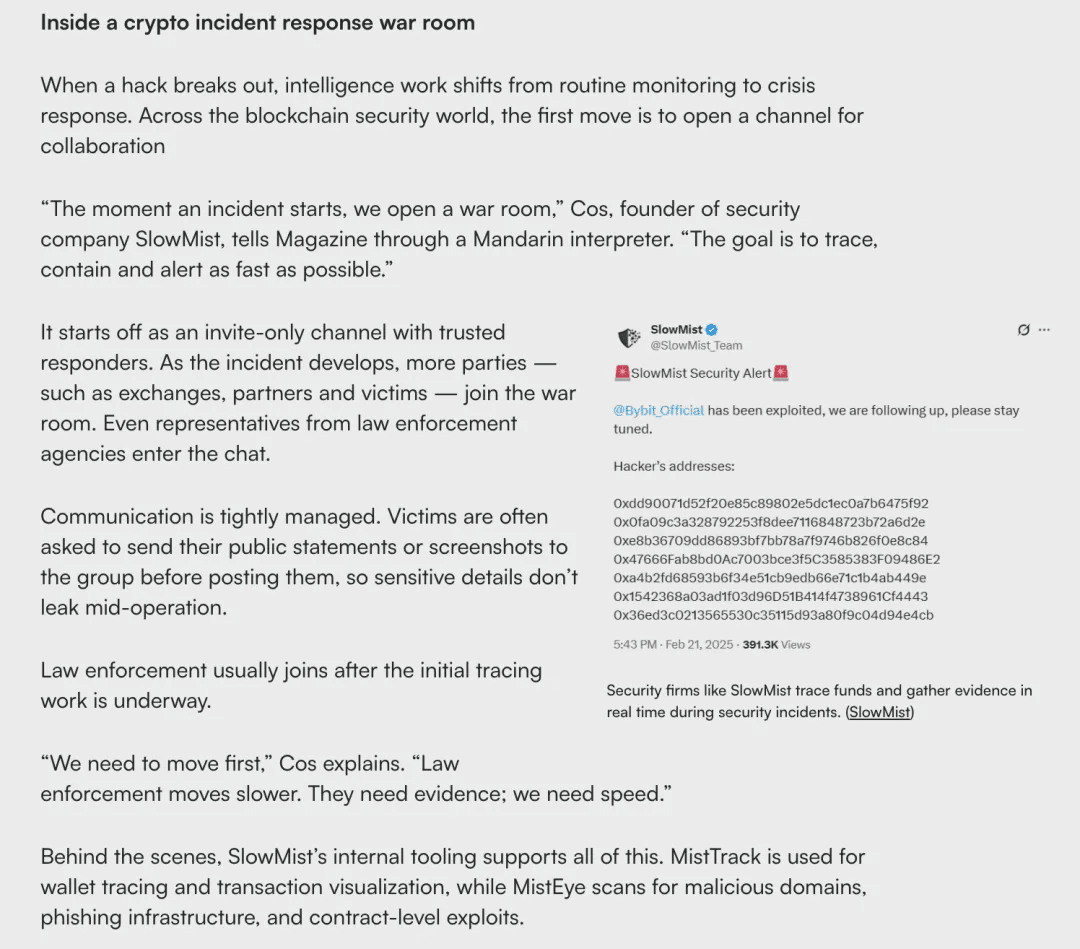
In the interview, Cos introduced SlowMist's standardized incident response mechanism. He pointed out that on-chain attacks typically have characteristics of "rapid spread, broad cross-chain impact, and very short windows," thus the response speed almost determines the upper limit of the final losses from the incident. "As soon as an incident occurs, we immediately activate the command center, aiming to quickly track, control, and issue alerts." In the command center environment, the team quickly divides tasks based on the attack path, such as on-chain tracking, infrastructure analysis, domain risk assessment, and secondary attack monitoring. As the incident progresses, trusted project parties, exchanges, partner teams, and victims will gradually join in to share intelligence, synchronize actions, while strictly controlling the risk of information leakage. Cos also admitted that professional security teams must take the lead in the early stages of an incident: "The involvement of law enforcement agencies is relatively slow; they need time to collect evidence, while attacks can cause significant losses in just a few minutes, so we need speed and must act before greater losses occur." This also explains why security teams in the industry often bear the earliest and heaviest response pressures.
Such emergency capabilities do not come from nowhere; they are the result of SlowMist's long-term investment in product systems and intelligence capability construction. For example, the report mentions: MistTrack (an on-chain analysis and anti-money laundering tool independently developed by SlowMist, which can track hacker fund flows, timely identify risk addresses, and assist users and enterprises in compliance checks), and MistEye (a Web3 threat intelligence and dynamic security monitoring system independently developed by SlowMist, which can detect potential attack behaviors in real-time and provide early warnings and protection for project parties and exchanges). Relying on these tools, combined with InMist Lab (a threat intelligence collaboration network led by SlowMist), the SlowMist security team can quickly lock down attack links and prevent further losses during critical windows after an incident occurs, providing clear and executable action recommendations to exchanges, project parties, and partners, significantly improving overall response efficiency.
Industry collaboration remains key
The report not only showcases SlowMist's defense system but also presents broader industry collaboration. Independent researchers like ZachXBT, Saiyan, Garcia, and many professional security teams play an irreplaceable role in on-chain security incidents: from tracking complex on-chain fund flows, analyzing phishing infrastructure, to utilizing OSINT (Open Source Intelligence) and HUMINT (Human Intelligence) techniques to identify potential malicious developers, almost every key step relies on close collaboration and real-time intelligence sharing across teams and regions.
Cos emphasized: "Attackers often use cross-chain and cross-platform methods for rapid attacks, making it difficult for a single team to grasp the overall situation comprehensively. Only through real-time intelligence sharing and synchronized actions within the industry can anomalies be detected and losses blocked in the shortest time." In practice, this means that project parties, exchanges, independent researchers, and professional teams need to establish highly trusted communication channels, which is also the result of all parties being willing to open resources and contribute efforts at critical moments.
At the same time, Cos reminds us that the challenges in the security industry come not only from technical complexity but also from the test of ethical judgment. His X account name is @evilcos, seemingly joking, but hiding a reminder: "You must decide what kind of person you want to become. The technology in this industry can protect people as well as harm them; do not become a bad person."
Conclusion
This special report by Cointelegraph not only showcases the daily work of security practitioners but also reflects the collaborative strength demonstrated by the entire industry in responding to risks. We thank all the researchers, project parties, exchanges, partners, and community members willing to actively share information who have fought alongside us. Security construction is a cross-ecosystem and long-term effort; in the future, we will continue to deepen on-chain tracking, intelligence analysis, and emergency response capabilities, and jointly promote the Web3 ecosystem towards a more robust and sustainable direction with industry partners.
Original report:
https://cointelegraph.com/magazine/meet-crypto-sleuths-fighting-crime-better-than-the-cops/