In the eyes of most users, the 'Admin Key' in the smart contract always hangs like the sword of Damocles above their heads:
Once the private key is leaked, hundreds of thousands or even hundreds of millions of dollars in assets can be 'emptied' in a single transaction at any time.
The path chosen by LorenzoProtocol is to lock this sword in a 'cage' forged by code.
The CeDeFiManager contract is no longer a super backdoor that can arbitrarily change parameters and manipulate the vault, but rather an 'on-chain constitutional executor' with established rules:
Who can issue what instructions?
Which instructions can apply to which Vault?
To what extent can it be done, what consequences can it trigger?
These are no longer relying on 'team awareness', but are written into the logic of CeDeFiManager, and once on-chain, no one can change them.
One, why does LorenzoProtocol want to put a 'tightening spell' on the Admin Key?
In recent years, many DeFi protocols have experienced extremely tragic accidents because the Admin Key was stolen, social engineered, or mis-signed:
Some project vaults have been completely emptied by a transaction of 'upgrading contract';
Some protocol administrators made mistakes, changing key parameters to extreme values, triggering a chain liquidation;
Users think they are dealing with a 'decentralized smart contract', but in reality, they are betting that a small multi-signature group won't run into problems.
What LorenzoProtocol does with CeDeFiManager can be summarized in three layers:
Separation of funds and permissions
The Vault is only responsible for custodizing funds and executing specific strategy logic;
CeDeFiManager is responsible for 'administrative orders' and permission judgments, such as: creating new vaults, adjusting NAV, freezing suspicious shares.
All management actions go through the same door: executeCommand()
Any management instructions must go through the entry function of CeDeFiManager;
The function first performs permission checks and parameter checks internally, and only after passing is it allowed to issue to the Vault.
Administrators are also constrained by the code
No one can bypass CeDeFiManager to operate Vault directly;
Even with the management private key, what can be done and what cannot be done is also limited by the logic written in advance.
In this way, the trust path shifts from 'trust the administrator' to 'trust the rules designed by CeDeFiManager', which aligns more with the risk preferences of institutions and compliant funds.
Two, CeDeFiManager: From 'Universal Control Console' to 'Restricted Executor'
In the traditional proxy contract model, a proxy is often a 'universal transit station' that can freely point to new implementation contracts.
LorenzoProtocol does not simply replicate this paradigm but has set a narrower but clearer power boundary for CeDeFiManager.
CeDeFiManager can be understood as a 'restricted executor':
CeDeFiManager only does three types of things:
Representing governance or administrators, issuing verified instructions to the Vault (such as updating NAV, handling blacklists);
Managing strategy templates, standardizing how to deploy new Vault instances;
Performing unified permission and logic checks on all high-risk operations.
All these actions must go through the executeCommand() entry:
First, verify the identity of the caller: is it a DAO, is it a multi-signature, is it on the whitelist;
Second, verify the instruction type: does it belong to the allowed operation list;
Finally, verify the parameters: for example, whether the amount is within a reasonable range, whether the target Vault is in an operable state.
If there is a failure at any step, the transaction directly reverts, and the administrator only sees a failed transaction, not a security incident.
Three, the 'dual-layer architecture' of fund custody and instruction execution: Vault + CeDeFiManager
In the overall design of LorenzoProtocol, CeDeFiManager does not directly hold user funds:
The Vault contract is responsible for:
Deposits, withdrawals, redemptions, profit distribution;
Specific interactions with CEX, RWA custodians, or other strategy modules;
Recording each user's shares and corresponding net asset values.
CeDeFiManager contract is responsible for:
Connecting governance and administrators, unified entry;
Interpreting and verifying management instructions;
After passing verification, calling the corresponding management function of the Vault.
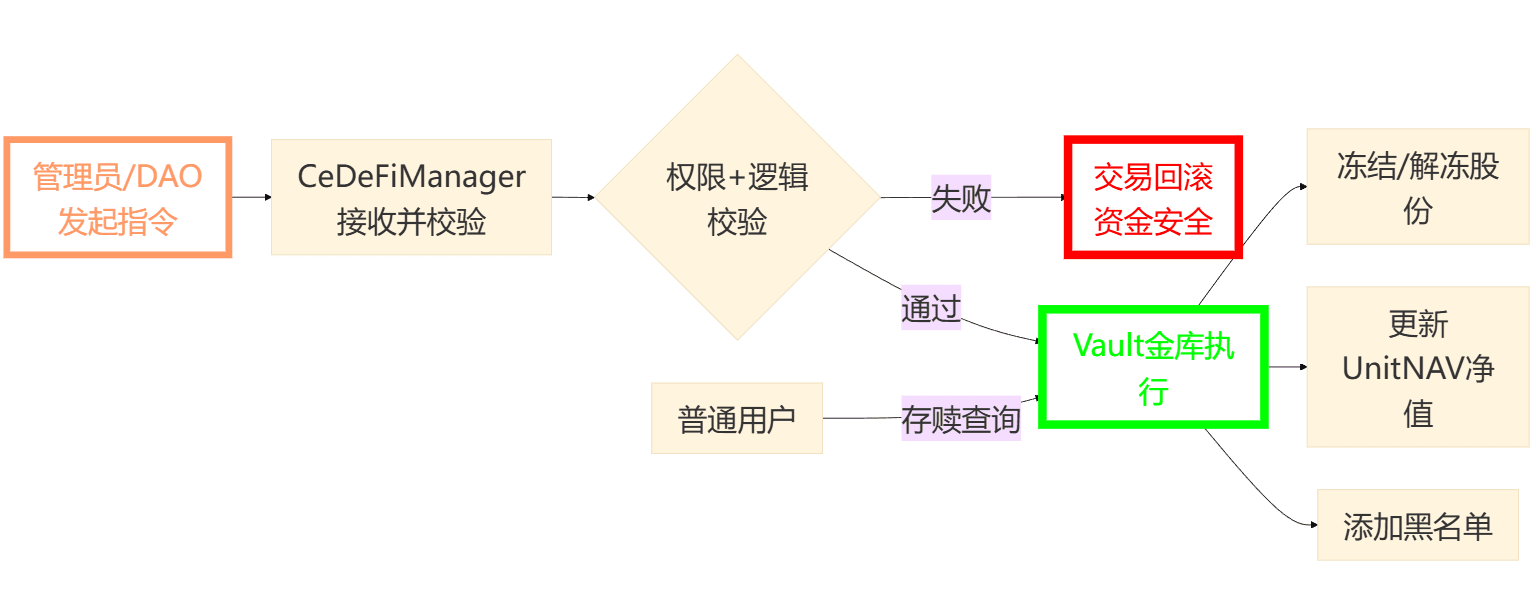
The key point of this structure is:
Users only interact with the Vault, and the interface experience is simple and clear;
All high-risk actions involving 'moving the vault' must be issued by CeDeFiManager;
Any attempt to bypass CeDeFiManager and take shortcuts is directly blocked at the contract level.
Four, under compliance requirements, how to clearly define the boundaries of 'fine sanctions': freezing, blacklists, NAV adjustments?
In the compliance environment of the real world, LorenzoProtocol will inevitably encounter such scenarios:
Certain addresses are marked as high-risk sources by external compliance services;
A small portion of LP shares involves disputes and needs to be temporarily frozen;
Cooperative custodians or auditors request NAV adjustments for a mispriced transaction.
Without CeDeFiManager, these demands can easily evolve into a dangerous 'universal backdoor'.
LorenzoProtocol's approach is to consolidate all these actions into clearly defined contract interfaces and strictly limit their scope:
freezeShares(...)
Only freeze specific addresses or specific shares corresponding to the LP;
The deposits and withdrawals of other users remain unaffected;
Leaving undeniable audit trails on the chain.
addBlacklist(...)
Only effective for subsequent operations, will not 'retroactively' affect historical interactions;
Cooperative agreements can decide whether to accept the liquidity of that address based on this status.
updateUnitNAV(...)
Make limited adjustments centered on the net asset value field within the contract;
Synchronously update the calculation basis for subsequent profit distribution or redemption.
What the compliant party sees is: LorenzoProtocol has the ability to cooperate with regulatory requirements, but this cooperation is 'surgical', not 'one-click lock down the entire protocol'.
What ordinary users see is: their funds will not be wiped out because of someone else's problems.
Five, Upgradable vs Immutable: LorenzoProtocol's 'middle road' choice
In terms of contract upgradability, extreme practices have their own problems:
Hardcoded logic, refusal to upgrade:
Once a serious bug is discovered, only migration to a new contract is possible, and both user experience and asset migration costs are very high;
New assets, new strategies, and new compliance requirements are difficult to integrate in a timely manner.
Administrators have complete upgrade rights:
Too many tainted events, and any slight disturbance will make users worry, 'Is this an upgrade or a rug pull?'.
LorenzoProtocol has taken a middle path with the help of CeDeFiManager:
The contract architecture retains necessary upgrade space (such as adding new strategy types, connecting with new custodians);
All upgrades and high-risk operations are included in the whitelist of CeDeFiManager's instructions and governance processes;
Set more protective measures for key instructions (for example, can only be triggered by DAO decisions, higher multi-signature thresholds, time locks, etc.).
On this path, LorenzoProtocol does not deny the existence of 'people', but locks the power of 'people' into the pre-agreed rules:
Administrators can still play a role, but can only operate within boundaries;
DAOs can still govern, but each governance action will leave an auditable process record on-chain.
Six, why is CeDeFiManager more like a 'digital constitution'?
If LorenzoProtocol is imagined as a 'small financial system on the chain',
then:
Vault acts like various functional departments (stablecoin vault, RWA vault, yield strategy vault);
Users are like 'citizens' in this system;
CeDeFiManager is like the 'constitutional execution agency' written into the system.
CeDeFiManager is not just a contract, but a digital contract:
Outwardly: telling users and institutions where LorenzoProtocol's power boundaries lie, what can be done and what absolutely cannot be done;
Internally: constraining the LorenzoProtocol team itself and future governance participants to prevent them from taking 'shortcuts' and 'abusing power' in times of pressure.
In this sense,
when LorenzoProtocol transferred key permissions from 'private key will' to 'CeDeFiManager rules',
CeDeFiManager completed a true 'constitutional moment'.
Risk warning
This article analyzes the design concept of LorenzoProtocol using CeDeFiManager from the perspectives of architecture and risk control, and does not constitute any investment advice or profit commitments.
Specific contract implementations, parameter configurations, permission settings, etc., may be upgraded or adjusted over time, and the actual situation is subject to the official public information and on-chain data of LorenzoProtocol.
Before participating in any DeFi protocol, please complete your own due diligence (DYOR) and fully understand the risks of smart contracts, compliance risks, and market risks.
I am a sword seeker, an analyst who only looks at essence and does not chase noise.@Lorenzo Protocol #LorenzoProtocol $BANK

