One of the most mature design signals in Dusk Network is not about privacy, cryptography, or speed. It is about how the system expects things to fail—and what happens next. Dusk does not assume perfect behavior, perfect code, or perfect coordination. It assumes the opposite: components will break, participants will drop out, and applications will behave unexpectedly. The protocol is built to survive that reality without cascading damage.
Most blockchains implicitly trust that failures will be rare or externally managed. When something goes wrong, recovery often depends on social coordination, emergency patches, or ad-hoc governance decisions. That approach works in experimental systems. It does not work in infrastructure meant to host long-lived financial logic.
Dusk takes a more disciplined stance. It isolates responsibility at multiple layers so that failure in one area does not automatically poison the rest of the system.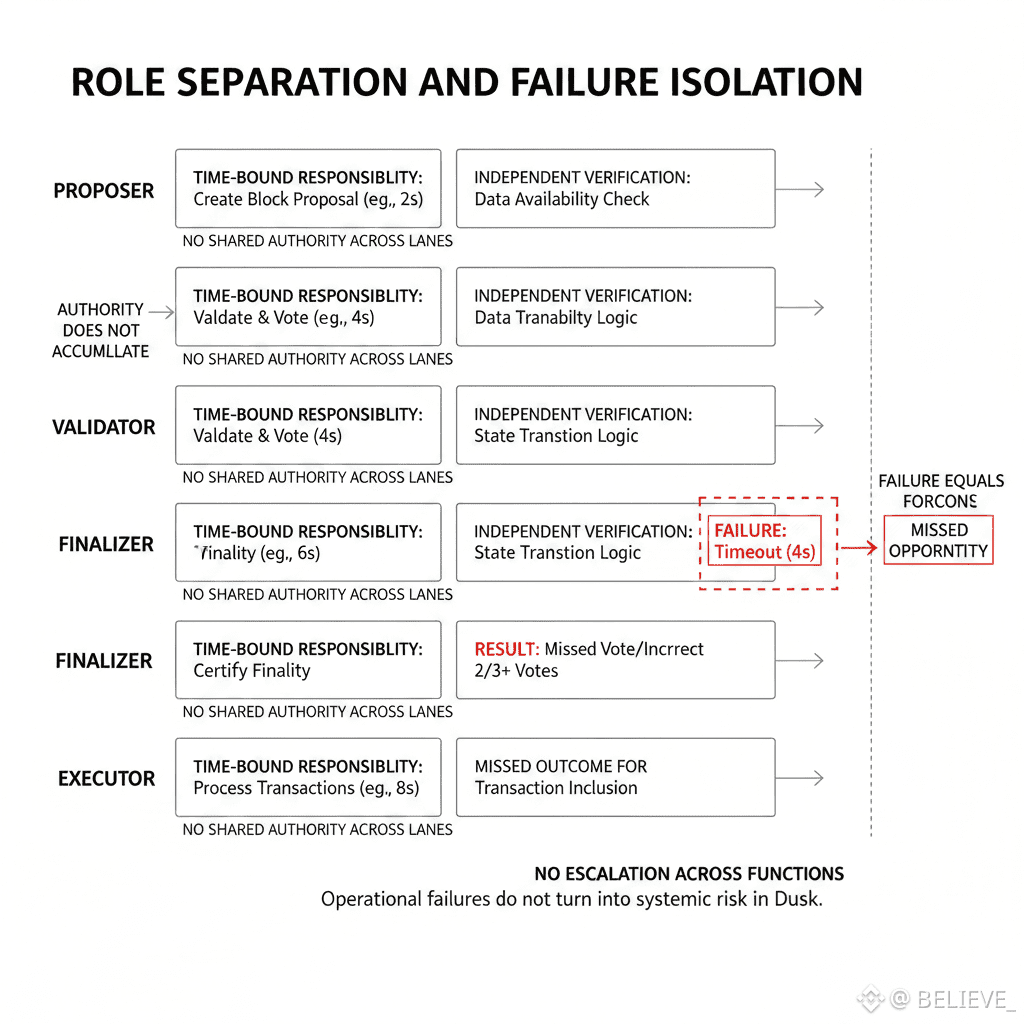
The first layer of containment is role separation. Participants are never asked to do “everything.” Proposing, validating, finalizing, executing—each responsibility is scoped, time-bound, and verifiable. If a participant fails in one role, that failure does not grant them leverage elsewhere. Authority does not accumulate across functions.
This matters because real-world failures are rarely malicious. They are operational: downtime, misconfiguration, delayed responses. By narrowing what each role can affect, Dusk ensures that ordinary failure looks like missed opportunity, not systemic risk.
The second layer of containment is execution isolation. Application logic does not bleed into protocol logic. Contracts operate within strict execution boundaries, and they do not mutate global behavior. If an application behaves poorly—whether through bugs or unexpected logic—the damage is localized. The protocol remains intact.
This is a sharp contrast to ecosystems where popular applications become de facto protocol dependencies. In those systems, an application failure can destabilize the network simply because too much value or activity depends on it. Dusk’s architecture resists that gravitational pull.
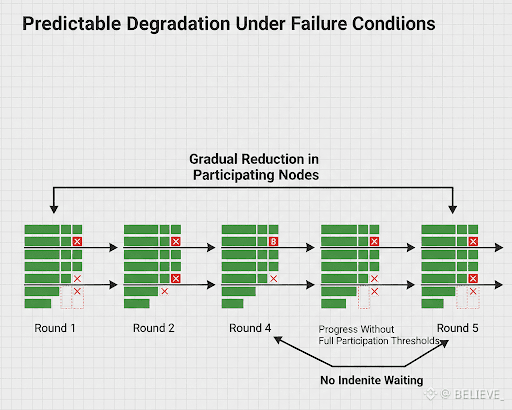
Another underappreciated aspect is how Dusk handles incomplete participation. The protocol does not assume everyone will show up. It defines exactly how much participation is enough and moves forward once that threshold is met. Nodes that fail to respond are not punished theatrically. They are simply excluded from outcomes they did not contribute to.
This design prevents what might be called “failure amplification.” In some systems, a few missing participants can stall progress, which creates stress, which leads to rushed fixes, which introduce more failure. Dusk breaks that loop by making absence non-fatal.
From an operational perspective, this is crucial. Infrastructure operators need systems that degrade gracefully. If a few machines go offline, the system should slow slightly—not collapse or fork unpredictably. Dusk’s bounded assumptions enable exactly that behavior.
There is also a psychological dimension to this design. Participants are not incentivized to over-optimize or take extreme measures to avoid minor penalties. Missing a window means missing a reward—not risking catastrophic loss. This encourages sustainable operation rather than brittle perfectionism.
The DUSK token participates in this containment strategy implicitly. Economic influence is always conditional. Capital only matters when it is actively and correctly applied under current conditions. Dormant or mismanaged resources do not quietly accumulate systemic importance.
Over time, this produces a healthier ecosystem. Participants invest in reliability, not heroics. Applications are built with clear assumptions about what the protocol guarantees—and what it does not. Users interact with a system that behaves consistently even when parts of it misbehave.
What stands out is that Dusk does not treat failure as an exception. It treats it as a design input. That mindset is common in aviation, power grids, and financial clearing systems—but rare in blockchain design.
Instead of promising that “the system is secure unless something goes wrong,” Dusk asks a harder question: what happens when something goes wrong anyway? The answer is not panic or central intervention. It is contained, predictable degradation.
In a landscape where many protocols optimize for best-case performance, Dusk optimizes for worst-case realism. That choice may not produce flashy benchmarks, but it produces something more valuable: confidence that the system will behave sensibly under pressure.
Ultimately, infrastructure is not judged by how it performs on good days. It is judged by how it behaves on bad ones. Dusk’s architecture suggests a clear priority: when failure happens—and it always does—the system should bend, not break.
That is not a marketing promise.
It is an engineering philosophy—and one that only becomes more important as blockchain systems move from experimentation into responsibility.

