In many blockchains, the virtual machine exists for one reason: to run code. It is treated as a neutral box that executes instructions and charges fees. Dusk Network assigns a very different responsibility to its virtual machine. In Dusk, the VM is a translation layer—one that bridges cryptography-heavy protocol guarantees with human-written application logic.
This distinction is subtle, but it changes how the entire system behaves.
Dusk’s environment is built around cryptographic enforcement: zero-knowledge proofs, commitments, confidential state, and strict correctness rules. None of that is naturally developer-friendly. Left exposed, it would make application development brittle, error-prone, and accessible only to specialists. The VM exists to absorb that complexity, not push it outward.
Rather than forcing developers to reason directly about low-level cryptographic primitives, Dusk’s VM provides structured host functions. These functions encapsulate complex operations—proof verification, Merkle interactions, signature checks—behind deterministic, auditable interfaces. The VM becomes a translator between what the protocol requires and what developers can realistically build.
This is an intentional design choice. Dusk does not try to simplify the protocol by weakening guarantees. It simplifies interaction with the protocol by giving developers a controlled surface area.
From a professional standpoint, this is how serious systems are designed. In operating systems, applications do not manipulate hardware registers directly. In databases, users do not manage disk pages manually. Abstraction layers exist to prevent mistakes from becoming systemic failures. Dusk applies that same discipline to blockchain execution.
Another important aspect is that the VM is deliberately constrained. It is not designed to be endlessly extensible or permissive. Certain behaviors are impossible by construction. Time-dependent calls, external state access, or non-deterministic operations are excluded. This is not a limitation born of caution—it is a requirement for maintaining cryptographic correctness under privacy.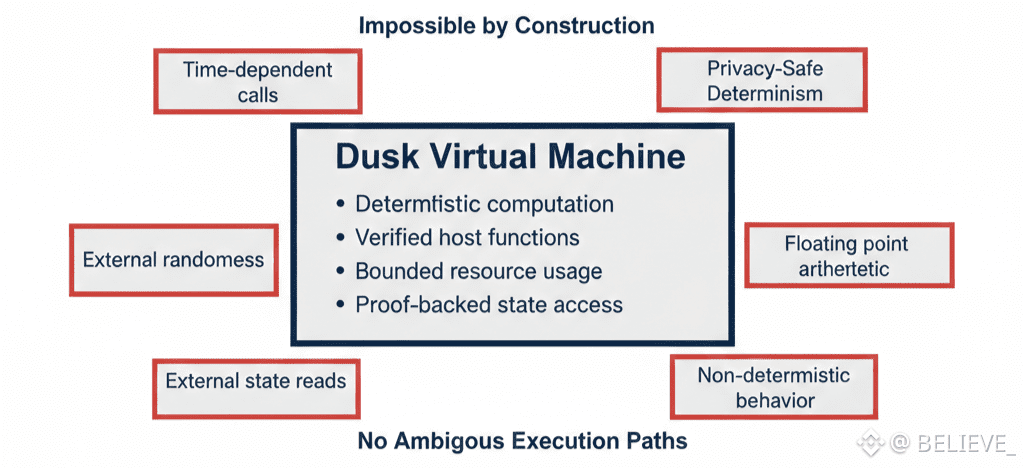
When execution outcomes must be provable without revealing internal state, ambiguity is unacceptable. The VM enforces a world where every operation has a well-defined meaning, cost, and effect. Developers trade flexibility for certainty.
What makes this especially relevant is that Dusk targets applications that are long-lived. Regulated assets, governance logic, lifecycle management—these are not short-term experiments. They must behave consistently over years. A permissive VM might feel empowering early on, but it becomes a liability as contracts age and assumptions shift.
The VM serves as a containment boundary. Protocol logic cannot be influenced by application logic. A contract cannot change consensus assumptions, rewrite rules, or interfere with unrelated states, even if it exhibits unexpected behaviour. The system is shielded from becoming application-dependent by this division.
This has ecosystem implications. In some blockchains, a handful of popular applications become de facto infrastructure. Their bugs, upgrades, or failures ripple outward. Dusk’s VM resists that pattern. Applications remain consumers of the protocol, not co-authors of it.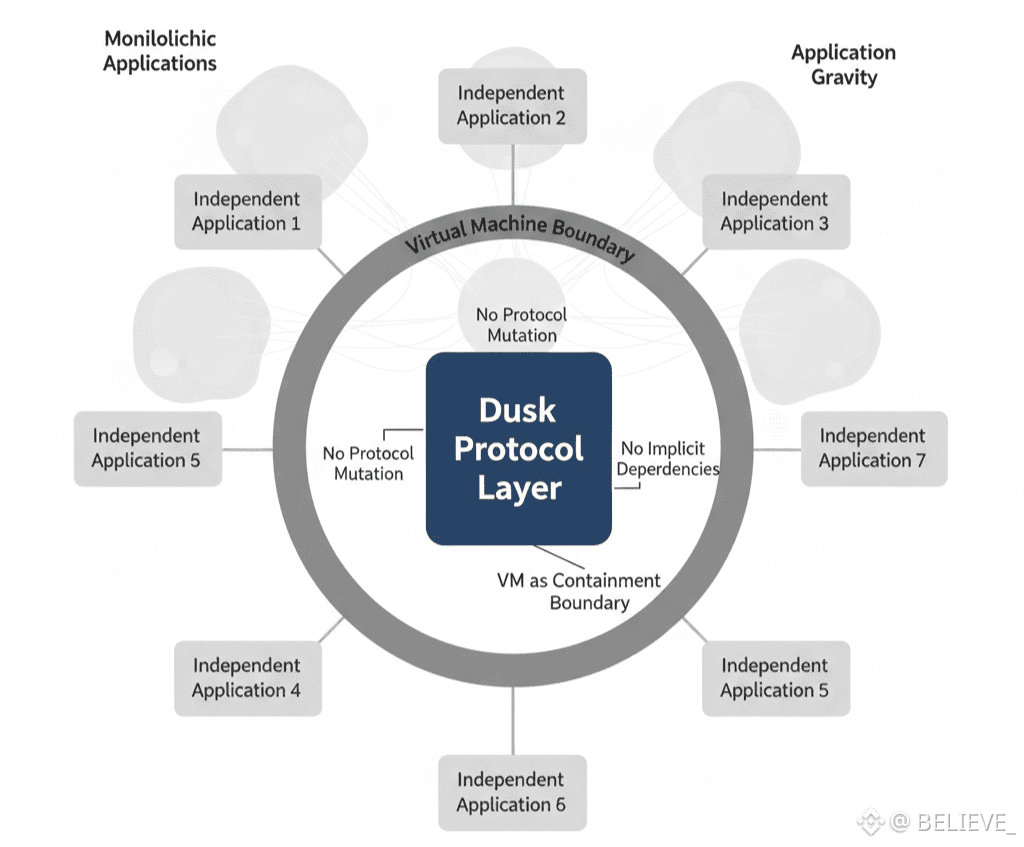
Additionally, there is a security advantage that is frequently disregarded. Dusk minimises redundant logic across contracts by centralising intricate cryptographic verification within the host functions of the virtual machine. There are fewer chances for subtle errors when there are fewer custom implementations. The most delicate operations in the protocol are implemented once, carefully examined, and repeatedly used.
From the developer’s perspective, this changes how trust is allocated. Instead of trusting each application to “do crypto correctly,” developers trust the VM to enforce correctness uniformly. That trust is easier to audit and easier to reason about.
The DUSK token benefits indirectly from this structure. Economic actions—fee accounting, execution limits, settlement—depend on correct execution. When the VM enforces strict boundaries, economic behavior becomes predictable. Participants can model costs and outcomes without worrying about hidden execution paths.
Importantly, this design does not eliminate creativity. It channels it. Developers are free to build sophisticated logic, but within a framework that guarantees compatibility with privacy, correctness, and determinism. Innovation happens at the application level without destabilizing the foundation.
This balance is difficult to achieve. Too much abstraction, and the system becomes rigid. Too little, and it becomes fragile. Dusk’s VM aims for a middle ground: expressive enough to support real applications, disciplined enough to preserve protocol guarantees.
What stands out is that Dusk does not treat its VM as an implementation detail. It treats it as part of the protocol’s philosophy. The VM is where human intention meets cryptographic enforcement. It is where mistakes are either prevented or amplified.
By designing the VM as a translation layer rather than a sandbox, Dusk ensures that developers are not asked to become cryptographers—and cryptographic guarantees are not compromised to accommodate convenience.
In a space where many platforms equate flexibility with progress, Dusk makes a quieter argument: systems that must last need boundaries that teach developers how to build safely.
That philosophy may not produce viral demos.
But it produces software that can survive scrutiny, audits, and time—and that is the standard Dusk is clearly aiming for.

