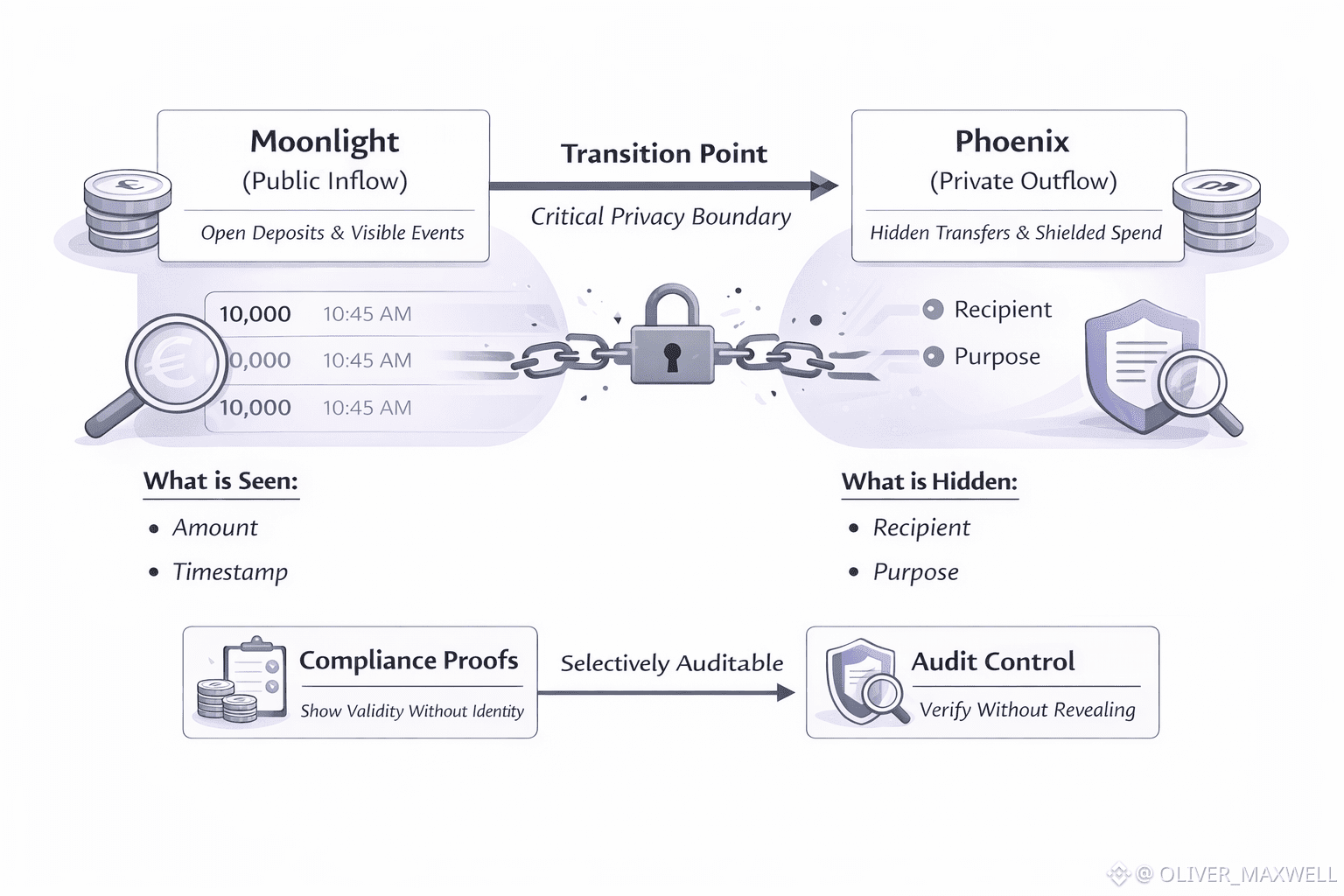
On Dusk right now, Moonlight-visible inflows are easy to explain and record, and the first Phoenix spend after those inflows is where the chain either protects intent or leaves a trail. A Moonlight receipt can be logged cleanly, but the moment that value crosses into Phoenix and later moves again is where Dusk’s privacy promise is actually tested. I keep coming back to this pressure point because it is the moment when most privacy designs stop feeling like privacy and start feeling like a ledger of clues.
Dusk’s dual transaction model matters here for a reason that is easy to miss if you treat privacy as a blanket. Moonlight is the lane where a public inflow can be received in an account-based form that institutions can explain, record, and reconcile. Phoenix is the lane where Dusk tries to make the subsequent movement of that value stop being an intelligence feed for everyone watching the chain. Dusk is tested when a Moonlight-visible inflow can move into Phoenix without the entry acting like a tag that follows it. Because Moonlight is account-based and public on Dusk, the chain creates crisp event boundaries, and Phoenix has to stop observers from chaining the next shielded action back to that boundary. If a Moonlight inflow with a distinctive fingerprint enters Phoenix and the activity that follows preserves that fingerprint in timing or size patterns, Dusk has hidden fields while leaving linkage intact. Phoenix is therefore not merely a private transaction format for Dusk, it is a boundary mechanism that must actively break narratives that begin in Moonlight. When Phoenix is treated as a boundary, the questions become operational: how does value enter, how is it represented inside, and what does Dusk allow a user to prove about that value without forcing them to reveal who they are paying.
Phoenix exists in Dusk to let value that must arrive publicly through Moonlight be spent privately without dragging its origin along. A tokenized instrument issued on Dusk is likely to need a visible issuance event, visible supply discipline, and visible administrative actions, which pushes those flows toward Moonlight. Yet the same instrument will often require confidential secondary activity, because positions, counterparties, and execution intent are sensitive under both market logic and supervisory logic. Dusk’s design implication is that privacy cannot start at issuance, it has to survive the transition from issuance into circulation, and Phoenix is where Dusk claims that circulation can happen without publishing the market’s internal map. The compliance requirement does not disappear at the Phoenix boundary, it becomes more technical. Dusk has to let a regulated participant demonstrate constraints about a Phoenix spend without converting that spend back into a public event. That is why Dusk’s emphasis on auditability changes the shape of Phoenix’s problem, because the goal becomes selective visibility rather than blanket opacity. If Phoenix can provide verifiable spend correctness while keeping counterparties and amounts shielded, Dusk can support regulated flows without forcing private outflows back into Moonlight for reassurance.
This is where Dusk’s modular approach is not decoration, it is part of the containment strategy for the boundary. A regulated application on Dusk will want predictable hooks for permissioning, reporting, and dispute handling that do not require rewriting the privacy layer each time. For Dusk to serve regulated applications, a Phoenix spend has to support tightly scoped, on-demand disclosure of specific properties to an authorized party, otherwise institutions will keep value in Moonlight to stay governable. I cannot assume a single universal compliance flow across jurisdictions, so the modularity in Dusk has to show up as flexibility around Phoenix, not as a separate story about extensibility.
The trade-offs around the Phoenix boundary on Dusk become real only when enough unrelated activity shares the same shielded lane to make Moonlight-to-Phoenix transitions unremarkable. Phoenix is stronger when many unrelated values share the same shielded environment, because indistinguishability grows with participation. Phoenix is weaker when usage is thin, when values enter and exit in predictable sizes, or when the boundary is used in a highly scripted way by a small set of actors. That means Dusk’s privacy strength is partially social and economic, and Dusk’s incentives and application design need to make Phoenix activity normal enough that public inflows can disappear into it without standing out.
There is also a cost surface that Dusk cannot hand-wave, because Phoenix transactions on Dusk inherently demand heavier proving and verification work than Moonlight transfers. If Phoenix operations are expensive, slow, or operationally brittle, Dusk will see the boundary used only when it is absolutely necessary, which makes every Phoenix entry itself a signal. If Phoenix operations are cheap and routine, Dusk gives public inflows a plausible way to transition into private circulation without advertising that transition. This is the paradox of the boundary: friction creates rarity, rarity creates detectability, and detectability is a privacy leak even when the data fields are hidden.
Because Dusk pairs privacy with auditability, Phoenix forces Dusk to define who can see what, under what control, and what can be proven without reopening the flow graph. A Phoenix spend that is selectively auditable implies some controlled capability to reveal, explain, or prove properties of the spend when a legitimate authority demands it. Dusk has to make that capability usable without making it abusable, because a compliance feature implemented as an unstructured backdoor would collapse trust in Phoenix. The hard requirement for Dusk is that any audit path at the Phoenix boundary must be narrow, intentional, and defensible, so that a public inflow can be spent privately without turning every private spend into a potential coercion point.
I also watch how the boundary interacts with composability, because regulated financial applications on Dusk will not tolerate privacy that breaks basic operational logic. If a Phoenix balance cannot be used with the kinds of instruments Dusk is targeting, then users will keep assets in Moonlight longer than they should, and the public inflow will keep bleeding metadata through ordinary interactions. If Phoenix can participate in the right classes of transfers and settlement flows while still protecting the outflow graph, then Dusk can keep sensitive activity inside Phoenix without forcing users into awkward detours that create new signals.
What makes Dusk distinctive is that it does not treat the Phoenix boundary as an optional privacy feature bolted onto a transparent chain, because Dusk’s target market forces the boundary to be the product. Regulated issuance on Dusk creates public inflows that must be clean, and real market behavior on Dusk creates private outflows that must be safe, and the credibility of Dusk lives in whether Phoenix can separate those two truths without breaking either. Dusk earns institutional trust when a Moonlight-visible inflow can remain inside Phoenix long enough to lose its identity, while still allowing a controlled explanation under audit that does not rebuild the transaction graph. Phoenix is the place where Dusk turns tokenized finance from public intake into private circulation without making the boundary the loudest signal on the chain.
