After delving into Walrus's latest technical roadmap, especially the details of its validator node client upgrade, I have an increasingly strong feeling.
I believe that the current mainstream narrative of cross-chain security models, whether it is multi-signature or optimistic verification, is caught in a dilemma of compromising between 'trust costs' and 'degree of decentralization.'
Walrus has chosen a more hardcore and engineering-oriented path, which makes me feel that its goal is not merely to serve asset cross-chain.
In my opinion, it attempts to leverage hardware security technologies like trusted execution environments to build verifiable and highly private 'secure data channels' in a mutually distrustful multi-chain environment.
This channel can not only transmit asset states but may also carry broader inter-chain messages in the future. In this piece, I will analyze how Walrus integrates TEE with cryptography to redefine the security assumptions of the cross-chain layer.
First, we must face the reality that traditional cross-chain bridge security models have trust bottlenecks. I believe this is an unspoken pain point in the industry.
Multi-signature schemes have their security limits entirely dependent on the honesty and physical dispersal of the signers, which is essentially traditional social trust.
The optimistic verification model introduces challenge periods and game mechanisms but shifts the security costs onto complex monitors and long waiting times.
They are all making efforts at the software and game theory level, but it seems to have hit a certain ceiling.
My view is that when the value and complexity of states needing to be transmitted across chains grow exponentially, the economic security and finality latency of these models will become unacceptable.
Walrus's starting point is to shift part of the critical security assumptions from "trust in people/institutions" to "trust in mathematically verified hardware environments."
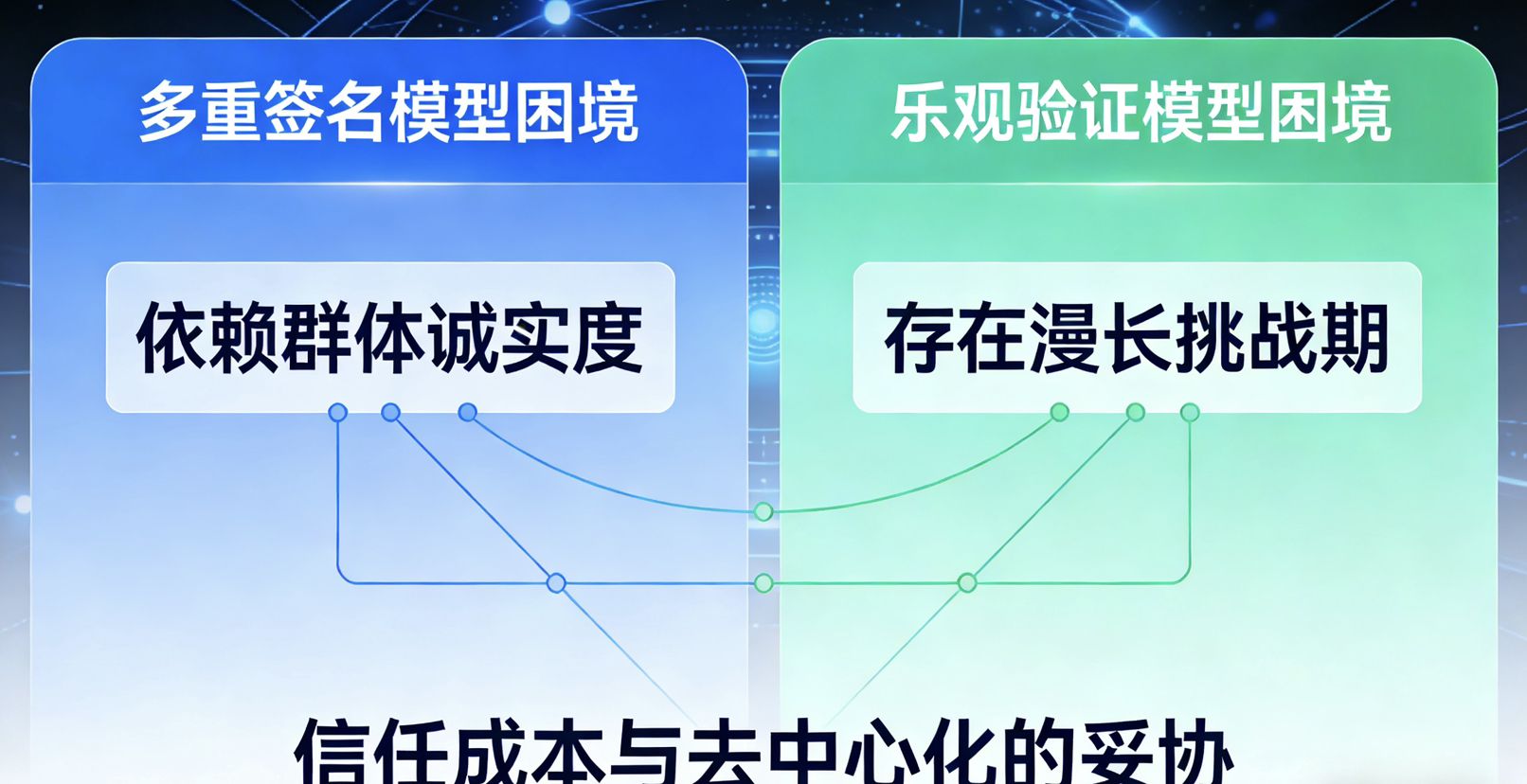
Secondly, the integration of TEE in Walrus's validator nodes is fundamentally about creating a "verifiable black box" execution environment. I believe this is the beginning of its architectural brilliance.
Trusted execution environments, such as Intel SGX or ARM TrustZone, provide an encrypted area isolated from the host operating system.
The code and data running in this area cannot be peeked at or tampered with, even by the node operators themselves.
Walrus's validator client runs its core "state validation logic" and "private key signing module" within a TEE enclave.
What does this mean?
When the block header or state proof of the source chain is sent into the TEE, its verification process is completed in an environment that is isolated from the outside world and cryptographically proven to be pure.
The verification results (signatures of the validity of cross-chain transactions) are issued by the secure key inside the TEE and come with a "remote attestation" generated by the CPU hardware.
This proof can be verified by anyone to confirm that the signature indeed comes from a legitimate TEE environment running specified, untampered code.
My view is that this essentially creates a form of "verifiable objectivity." We no longer need to trust the character of node operators, but rather trust the security features of the hardware and mathematical proofs.
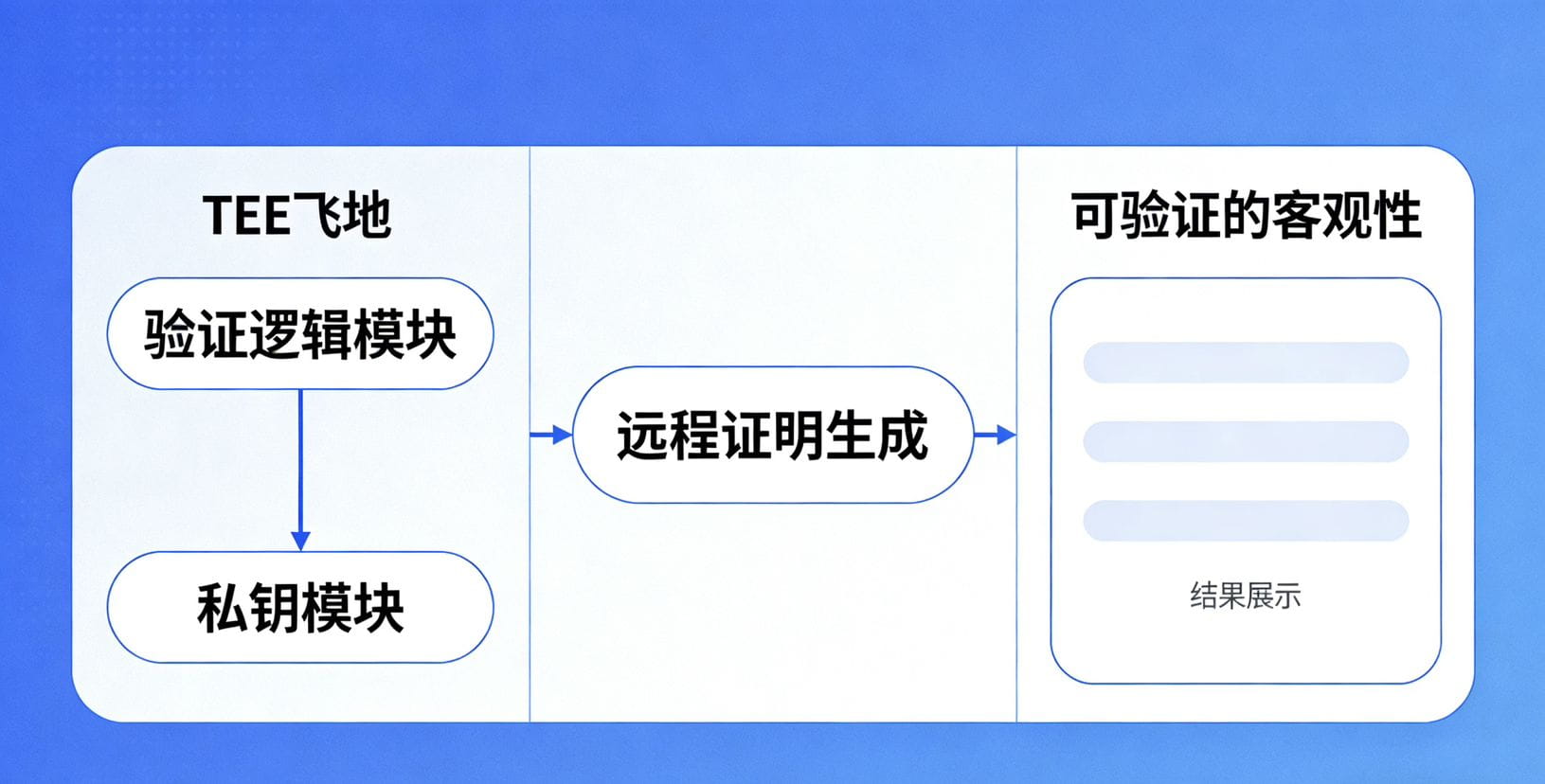
Third, how does this mechanism specifically construct a "security corridor"? I believe its key lies in the "unity of privacy and validation."
In traditional models, validators need to fully understand transaction details to sign, which itself is a point of information leakage.
In Walrus's TEE solution, sensitive cross-chain transaction data (such as amounts, receiving addresses, specific state details) can be encrypted before entering the TEE enclave.
The TEE uses its secure key to decrypt and process internally, and after processing, it encrypts the result before sending it out.
To the outside world, they can only see: "A certified TEE enclave has confirmed and signed the validity of a certain encrypted message."
As for what the message specifically is, aside from the two parties involved in the transaction and the TEE itself, no one knows.
This achieves a form of "verifiable computation under privacy protection."
For high-value institutional transactions or complex state cross-chain involving business strategies, I believe this feature is not just an embellishment but a necessary condition. It enables the cross-chain channel itself to possess the capability for confidential communication.
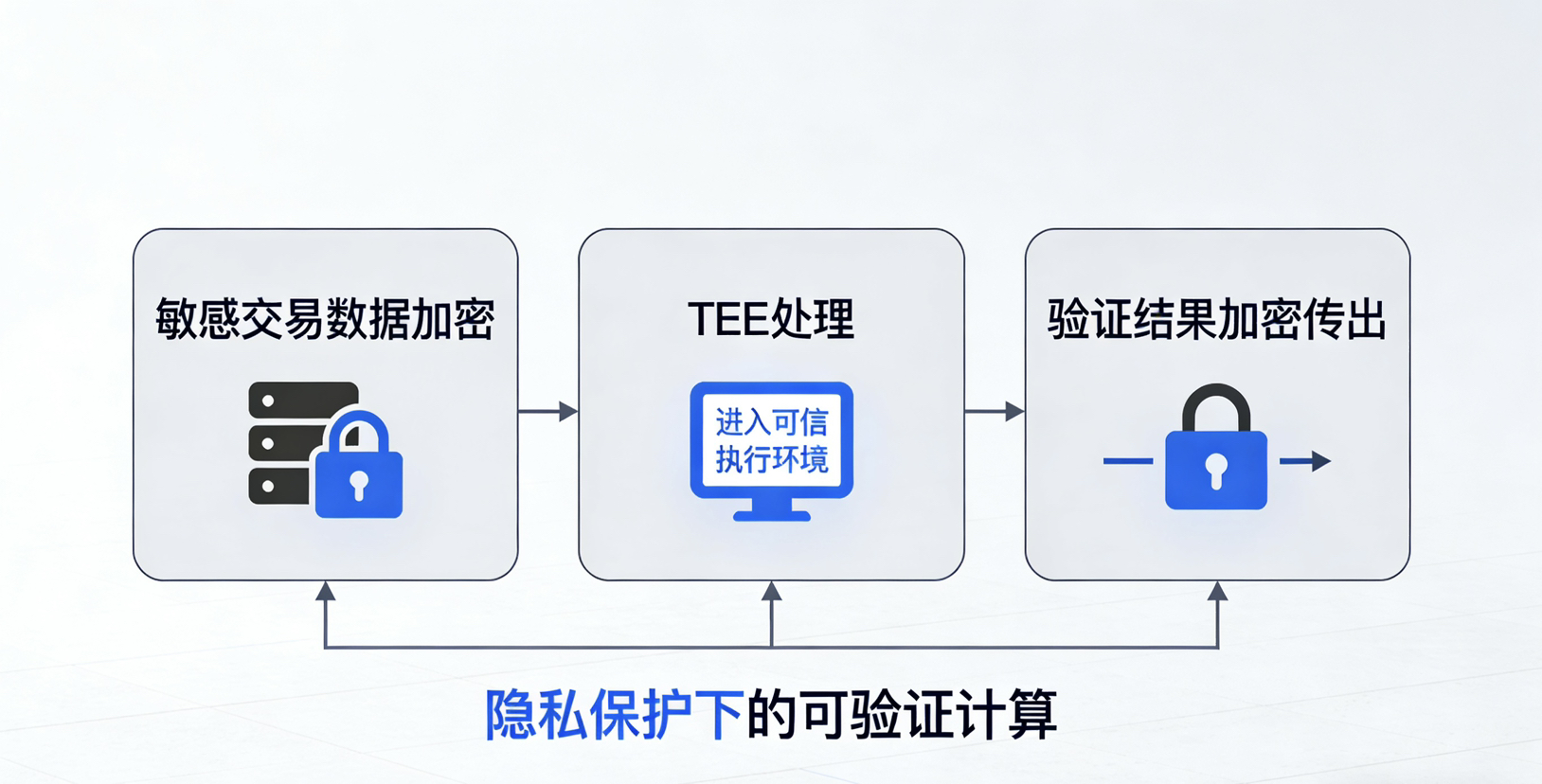
Fourth, from the latest dynamics, its cooperation with cloud service providers and hardware manufacturers aims to scale and standardize this security model. I noticed that the team recently reached a partnership with a giant providing confidential computing cloud services and a server hardware manufacturer.
The cooperation content far exceeds simple node hosting.
First, jointly optimize the deployment and management templates of TEE clients in cloud environments to lower the operational threshold and costs for validator nodes.
Secondly, jointly design a dedicated hardware reference architecture that meets future cross-chain validation requirements, which may involve deeper integration of TPM, secure boot chains, and TEE.
My judgment is that these cooperations reveal a signal: Walrus is not satisfied with small-scale technological experimentation; it hopes to promote the hardware-based trust model to become a reliable, scalable option in cross-chain infrastructure.
When enough geographically dispersed validator nodes operate in a certified secure hardware environment, the entire network's resistance to attacks and reliability will be qualitatively improved.
Fifth, I increasingly feel that Walrus's TEE approach is preparing for the future of "inter-chain messaging." Asset cross-chain is merely the initial form of cross-chain interaction.
Broader scenarios include cross-chain calls between smart contracts, synchronous state updates, and even private data interactions between blockchains and off-chain oracle networks.
These scenarios demand higher integrity, confidentiality, and execution reliability for message delivery.
A TEE-based verification network can precisely play the role of a highly reliable "inter-chain message notary."
It can confidentially verify that a certain on-chain event has indeed occurred and provide a trusted signature for the triggering instructions pointing to another chain.
This will provide a foundational trust base for cross-chain DeFi portfolios, full-chain game state synchronization, and enterprise-level blockchain interconnection.
Sixth, to summarize my core observation:
Walrus's exploration in the field of cross-chain security embodies an engineering philosophy of "reducing trust costs through hardware and software collaboration."
It does not remain at the abstract level of cryptography and game theory, but pragmatically and prospectively introduces hardware security technology.
By using TEE as the core trust component of the validator network, it is attempting to build secure and confidential data channels.
This channel, which I call the "inter-chain security corridor."
It is not only to make today's assets more securely cross-chain, but also to support tomorrow's inter-chain communication that requires extreme privacy and reliability.
WAL tokens in this network will be used to incentivize validators to deploy and maintain these certified secure hardware nodes, and their value will be deeply tied to the total passage value of the "inter-chain security corridor" guaranteed by the network.
I believe that this model, which combines cryptoeconomic incentives with trust in physical hardware, may be a direction with great potential for solving the cross-chain "trust triangle paradox."


