When I examine decentralized storage systems, privacy rarely presents itself as the headline feature. Conversations usually begin with durability, availability, and resistance to censorship. Yet as more sensitive datasets move toward decentralized infrastructure, a quieter question emerges: not only whether data survives, but who might observe it, analyze it, or derive signals from it over time.
While studying Walrus, I find that privacy is best understood not as a singular feature but as an architectural posture. Walrus is designed to distribute large blobs across a decentralized network using erasure coding while anchoring cryptographic commitments on the Sui blockchain. This structure prioritizes integrity and recoverability, but it also reveals an important truth about distributed systems — privacy is never absolute. It is negotiated across transparency, verification requirements, performance constraints, and economic viability.
Rather than positioning itself as a privacy-maximalist protocol, Walrus appears engineered with privacy awareness. Confidentiality is achievable, but it is largely implemented through layered practices that developers adopt alongside the protocol rather than delegated entirely to the storage layer.
Privacy Begins Before the Upload
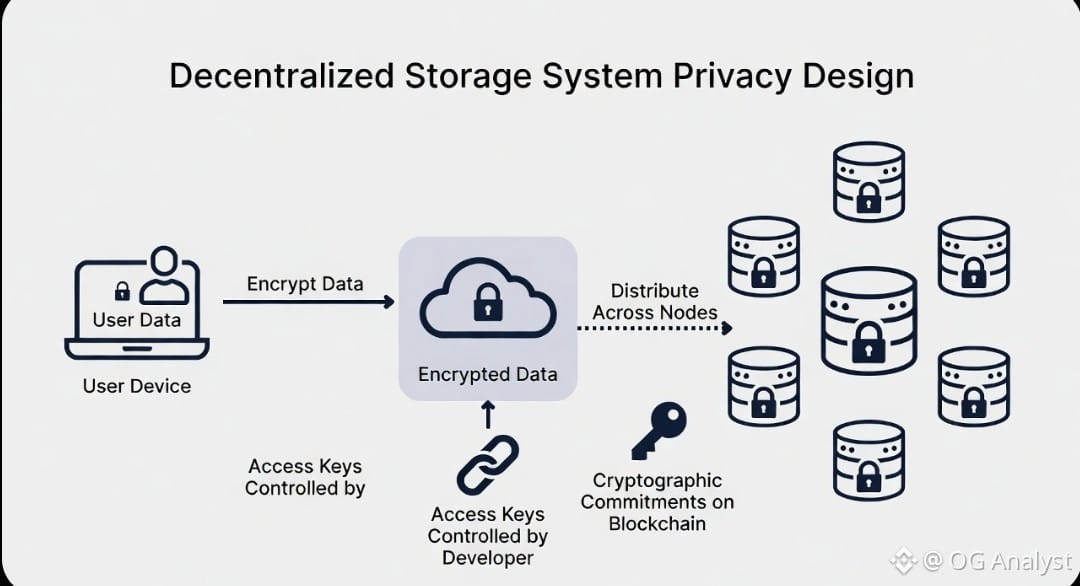
One of the most important realizations when working with Walrus is that privacy typically starts with the developer.
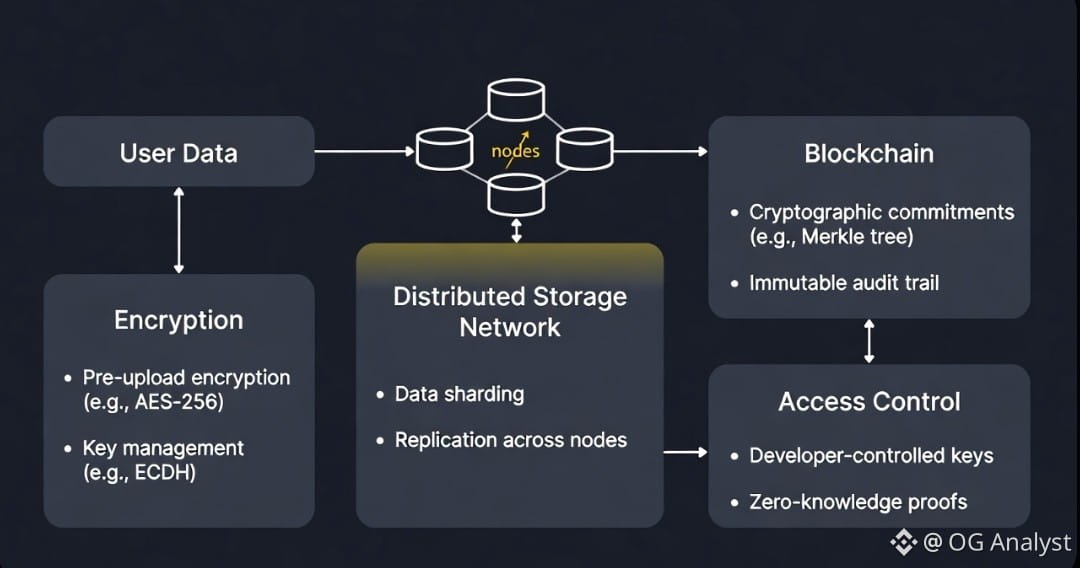
The network is responsible for distributing and preserving data, not automatically concealing it. As a result, sensitive datasets are generally encrypted prior to upload. Once encrypted, Walrus encodes the blob into slivers and disperses them across nodes, ensuring durability while the payload itself remains unreadable without the appropriate keys.
This separation of responsibilities is deliberate. Walrus focuses on guaranteeing that data remains available and verifiable; control over readability stays with the data owner. From a systems perspective, this model avoids embedding heavy confidentiality mechanisms directly into the storage protocol, allowing it to scale efficiently while still supporting private workflows.
After upload, the system returns a cryptographic reference — typically a hash or blob identifier — which developers can anchor on-chain within Sui smart contracts. What lives on the blockchain is not the raw dataset but the commitment to it. Integrity becomes publicly verifiable without exposing the underlying content.
The Structural Trade-Off: Privacy and Verifiability
Every distributed storage protocol must expose some information in order to prove that data exists and remains recoverable. Commitments, proofs, and availability checks all require observable structure.
Walrus appears to navigate this tension by allowing encryption at the data layer while maintaining transparent verification at the network layer. Content can remain confidential, yet correctness can still be audited through cryptographic evidence.
This equilibrium is significant. Absolute secrecy would undermine trustless verification, while excessive transparency would weaken confidentiality. By separating encrypted payloads from publicly verifiable commitments, Walrus leans toward a balanced middle ground — one that supports both auditability and discretion without forcing either to the extreme.
Metadata: The Quiet Privacy Frontier
Even in encrypted systems, metadata can reveal patterns. Object size, upload frequency, and relational behavior between datasets may offer indirect insights into activity.
Walrus does not claim complete metadata obfuscation, and acknowledging this is important for realistic threat modeling. Developers handling highly sensitive information often design application-layer strategies — such as batching uploads or standardizing object sizes — to reduce unintended signal leakage.
Recognizing metadata as part of the privacy surface reflects a mature understanding of decentralized storage. Protecting the payload is only one dimension; limiting the story surrounding that payload is another.
Privacy Within Economic and Performance Constraints
Stronger confidentiality typically introduces heavier computation, additional verification steps, or increased storage overhead. These factors influence latency and, ultimately, pricing.
Walrus appears calibrated for large-scale blob storage, suggesting that privacy mechanisms must coexist with throughput expectations. Overly burdensome cryptography could distort the network’s primary objective: efficient, resilient data availability.
Similarly, decentralized storage only remains viable if it is economically sustainable. Reliability, redundancy, and verification already carry costs, often expressed through WAL-denominated storage payments. Introducing aggressive privacy guarantees at the protocol layer could amplify those costs and create friction for adoption.
The resulting posture feels pragmatic rather than absolutist — privacy is supported, but not at the expense of operational stability.
A Practical Mental Model for Private Storage on Walrus
For developers, integrating private storage is conceptually straightforward once responsibilities are clearly divided.
A typical workflow might look like this:
Encrypt locally.
Generate a key and encrypt the dataset before interacting with the network.
Upload the encrypted blob.
Walrus handles encoding, distribution, and availability across nodes.
Anchor the commitment on Sui.
Store the blob reference inside a Move module or contract so applications can verify integrity without exposing raw data.
Control access through keys.
Authorized parties retrieve the encrypted object and decrypt it client-side, preserving confidentiality while allowing independent hash verification.
What stands out in this flow is what does not happen: sensitive data never needs to reside directly on-chain. The blockchain maintains truth; Walrus maintains the data.
Understanding Walrus as Privacy-Aware
If I were to characterize Walrus’s current stance, I would describe it as privacy-aware rather than privacy-maximalist.
The protocol emphasizes:
Recoverability
Verifiability
Network resilience
These priorities sometimes require structural visibility. Instead of attempting to eliminate that visibility entirely, Walrus allows developers to layer confidentiality where necessary.
This approach signals engineering restraint. Systems that pursue theoretical perfection often become impractical, while those that ignore privacy risk becoming unsafe. Walrus appears to favor an operational middle path — one grounded in realistic infrastructure demands.
Looking Ahead — Carefully
It is reasonable to observe that technologies such as confidential compute environments, stronger cryptographic proofs, or improved metadata protections are gaining momentum across distributed infrastructure. Should tools like these mature further, they could complement storage networks broadly.
However, it is important to separate architectural possibility from declared roadmap. Walrus does not currently depend on specialized hardware confidentiality or advanced zero-knowledge storage proofs. Any future evolution in these areas would likely reflect the broader trajectory of decentralized systems rather than a single protocol decision.
Maintaining that distinction helps keep analysis grounded while still acknowledging where the field itself may progress.
Human Reflection on Confidential Storage
The longer I study decentralized infrastructure, the more I see privacy not as a binary property but as a design attitude. Durable systems plan for node churn, hardware decay, and adversarial conditions. Responsible systems also recognize that sensitive data requires thoughtful handling long before it touches the network.
Walrus does not promise invisibility. Instead, it offers a framework in which encrypted data can remain confidential, commitments can remain verifiable, and storage can persist despite operational volatility.
In practice, that combination often proves more valuable than absolutist guarantees.
Conclusion
Privacy in decentralized storage emerges from layered decisions rather than a single protective mechanism. Walrus reflects this reality by pairing encrypted data workflows with authenticated commitments, allowing confidentiality and verification to coexist without overwhelming performance or cost structures.
For developers, the path is clear in principle: encrypt before upload, store through Walrus, anchor references on Sui, and manage access through cryptographic keys. The protocol safeguards availability; discretion remains in the hands of those who control the data.
By avoiding both privacy minimalism and privacy absolutism, Walrus presents a measured architectural stance — one that acknowledges the constraints of distributed systems while still enabling confidential use cases.
In infrastructure designed to last, that kind of balance is rarely accidental.

