Over the last year, data availability and ownership have quietly become one of the most debated topics in crypto infrastructure. It’s not flashy like memecoins or ETFs, but it’s where real builders and serious capital are paying attention. Walrus has been part of that conversation, especially as teams rethink how decentralized storage, encryption, and migration actually work in practice. The recent discussion around Tusky’s encryption model and migration options fits directly into this broader shift, and it’s worth unpacking calmly, without hype.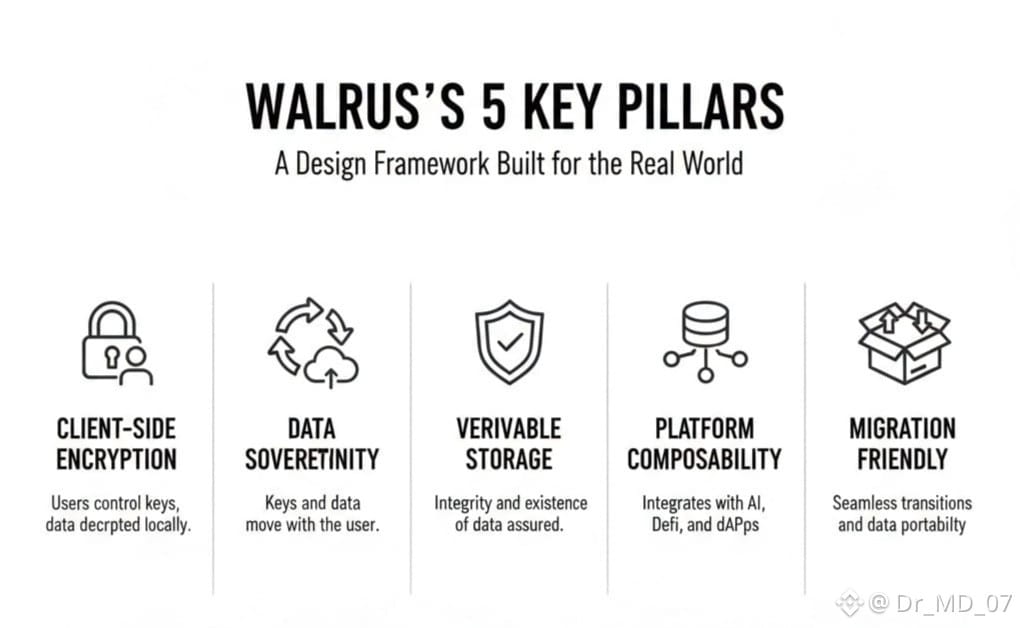
Tusky’s approach is fairly clear once you strip away the jargon. All encryption and decryption happens on the client side, handled by the Tusky SDK. That means data blobs are never decrypted on Tusky’s servers. Whether users choose self-hosted keys or keys supplied by the user and stored in encrypted form on Tusky, the control remains at the edge. Practically speaking, if you download your data through the SDK, the files are already decrypted when they reach you. There’s no hidden server-side process, no black box. For anyone who has lived through exchange hacks or centralized storage failures, that distinction matters.
What’s interesting is how this ties into migration. Tusky has been upfront that users can request their encryption keys before shutdown and potentially reuse them elsewhere. That’s not something we used to hear from Web2 platforms. In traditional cloud storage, migration often means starting from scratch, re-encrypting everything, or trusting another centralized provider. Here, the idea that encryption keys can move with the user reflects a more mature understanding of data sovereignty. It also aligns well with how Walrus is positioning itself in the decentralized data stack.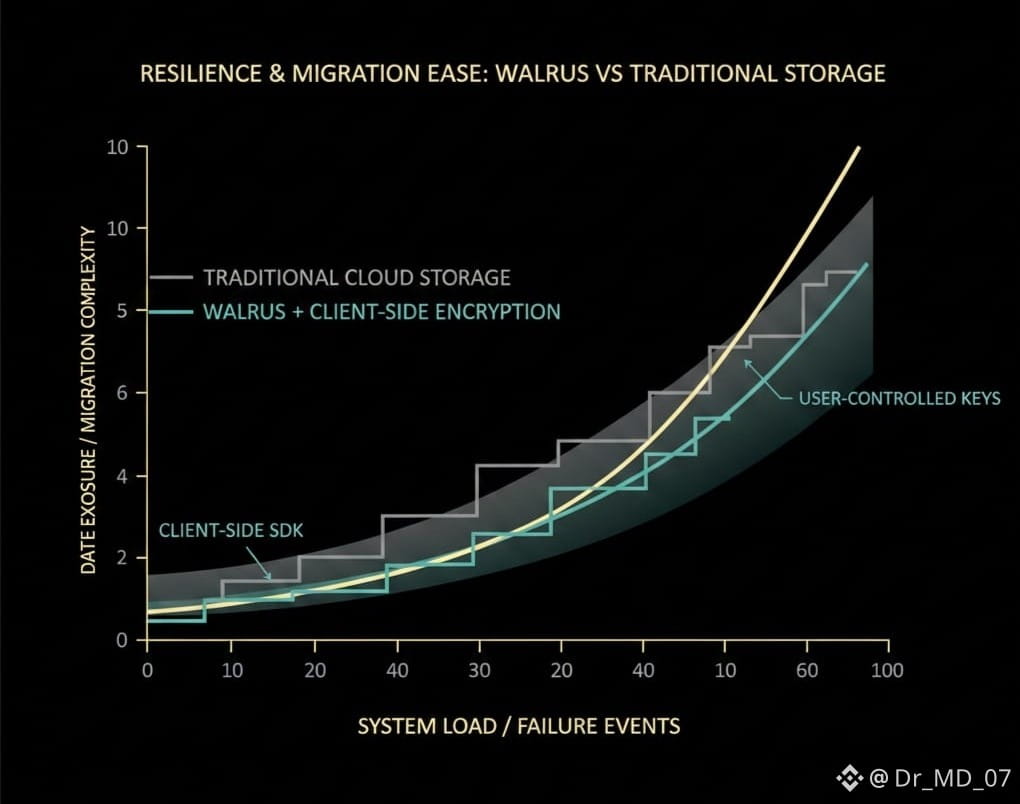
Walrus, at its core, is about programmable, verifiable data storage that can interact with AI, DeFi, and on-chain applications without forcing users to sacrifice control. Over the past few months, especially toward late 2025 and early 2026, the conversation around Walrus has shifted from “what is it” to “how does it fit into real workflows.” Storage alone isn’t enough anymore. Developers want guarantees about integrity, access control, and long-term usability, particularly when services shut down or evolve.
From a trader’s perspective, infrastructure narratives like this tend to surface quietly before they become obvious. In January 2026, several discussions in developer forums and ecosystem updates highlighted how projects are planning for graceful exits, not just growth. That’s a big change. Migration used to be an afterthought. Now it’s a design requirement. The Tusky encryption note reinforces this trend: client-side encryption, user-controlled keys, and flexibility in how data is secured after migration.
Technically, client-side encryption just means your device does the locking and unlocking, not the service. Even if someone accessed the storage layer, they’d see unreadable data. Walrus complements this by focusing on verification and availability rather than custody. It doesn’t need to know what your data is, only that it exists, hasn’t been tampered with, and can be referenced reliably by applications. That separation of concerns is subtle but powerful.
Why is this trending now? Part of it is regulatory pressure. Part of it is user fatigue with opaque systems. And part of it is AI. AI models rely heavily on data pipelines, and no serious team wants to feed sensitive or proprietary data into systems they can’t fully audit. Decentralized storage with clear encryption boundaries offers a middle ground between usability and control.
Progress-wise, Walrus has been steadily integrating with broader ecosystems rather than trying to dominate headlines. Recent updates have focused on improving data verification flows and making storage primitives easier for developers to plug into existing stacks. That’s not exciting marketing material, but it’s the kind of work that compounds over time. When paired with migration-friendly encryption models like Tusky’s, it paints a picture of an ecosystem that expects change rather than pretending permanence.
On a personal level, this is the kind of development I pay attention to more than price charts. Markets rotate. Narratives come and go. But infrastructure that respects users during transitions tends to stick around. I’ve seen too many projects lose trust not because they failed, but because they handled shutdowns poorly. Giving users access to their keys, their decrypted data, and real choices about re-encryption shows a level of professionalism that’s still rare.
As of early 2026, the broader takeaway is simple. Decentralized data isn’t just about storing files on-chain or off-chain. It’s about lifecycle management: creation, use, migration, and exit. Walrus fits into that story by focusing on verification and composability, while Tusky’s encryption approach highlights how client-side control can make migrations less painful and more transparent.
This isn’t a revolution. It’s slower than that. It’s infrastructure growing up. And for those of us watching the space with a long-term lens, that’s exactly the kind of progress that matters.


