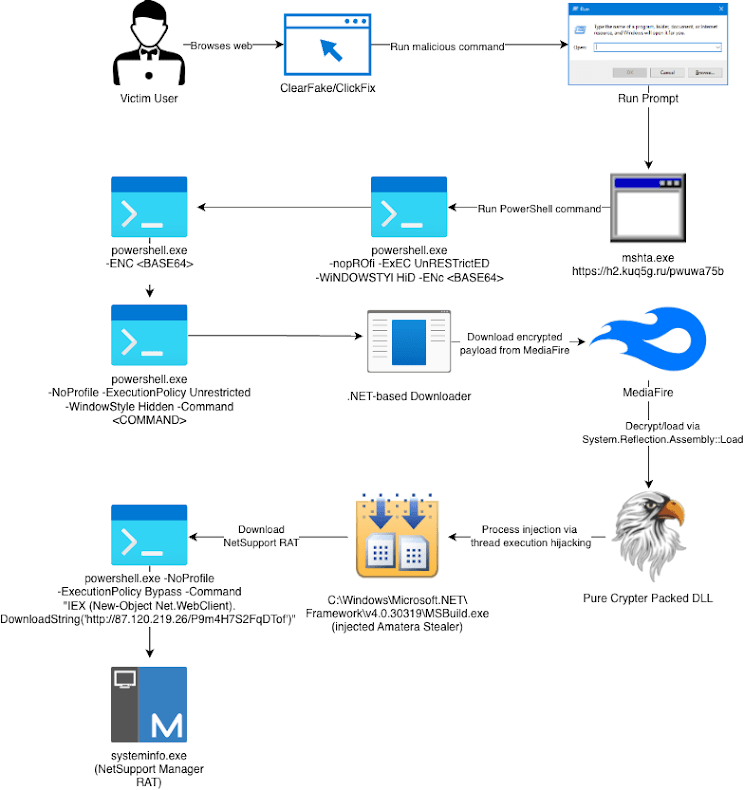
Scammers use fake CAPTCHA pages to trick victims into executing malicious commands.
Malware looks for Bitcoin wallets, browsers, emails, and messaging apps.
Attacks manage to bypass antivirus and only install RATs on computers with valuable data.
A growing attack is concerning cryptocurrency users: a new malware, based on the old ACR Stealer, is using the 'ClickFix' tactic to deceive victims and steal Bitcoin wallets.
The campaign mixes social engineering, fake pages, and advanced malware delivery techniques that make detection difficult.
How the 'ClickFix' scam works
Criminals create fake pages that mimic CAPTCHAs, system alerts, and notifications from services like Booking.com. In addition, they induce users to run a command in Windows under the promise of 'fixing an error' or 'granting access.' This command installs the malware.
The attack evolved from the ACR Stealer, previously sold as a service. Now, it operates by subscription. Therefore, criminals have expanded their reach and diversified campaigns with:
Fake ClickFix pages used in the SmartApeSG campaign.
VBS files with fake invoices.
Emails with fake internal alerts.
These pages also distribute the NetSupport RAT, a tool used for secret remote control. However, criminals only activate remote access on machines that show signs of cryptocurrency use, avoiding wasting resources.
According to security analyst John Hammond (Huntress Labs):
These attacks become more dangerous because they combine psychological manipulation with methods capable of bypassing security solutions.
Why Bitcoin wallets are such valuable targets
Cryptocurrencies can be transferred in minutes and without intermediaries. Therefore, a compromised wallet can yield high amounts quickly—often irreversibly.
Additionally, malware such as Amatera Stealer has been designed to:
identify wallets installed on the computer;
scan browsers for crypto extensions;
extract private keys and seed phrases;
capture login cookies and sessions on crypto platforms.
Therefore, this type of attack is growing because a single scam can yield hundreds of thousands or even millions of dollars.
Experts warn that antivirus and EDR are not enough. The malware can avoid sandboxes and use techniques that mask its execution.
The impact on the crypto ecosystem
This type of campaign directly affects traders, holders, and companies dealing with digital assets. In addition, it increases security costs, reduces trust, and pressures platforms to strengthen authentication and monitoring.
As transactions are irreversible, victims rarely recover funds. Therefore, there is a growing need for good practices, such as:
use of hardware wallets;
strong passwords and 2FA on all platforms;
avoid executing any commands requested by unknown websites;
be suspicious of unusual CAPTCHAs or out-of-standard system alerts.
Conclusion
The ClickFix campaign shows that scams using social engineering continue to be the weakest link in digital security.
Moreover, it reveals that criminals are combining old techniques with new methods that are difficult to detect. Therefore, cryptocurrency users should strengthen their precautions and treat any request for suspicious interaction as a potential threat.

