Recently, the Multilateral Sanctions Monitoring Team (hereinafter referred to as "MSMT") published a report titled "DPRK's Activities Violating and Evasion of UN Sanctions through Cyber and Information Technology Workers." This report systematically outlines the full picture of the Democratic People's Republic of Korea (DPRK) utilizing cyber capabilities, information technology workers, and cryptocurrency activities to evade UN sanctions, steal sensitive technology, and raise funds. This article will summarize the core content of the report to help readers quickly grasp the development trends and changes in methods of DPRK's cyber threats, thereby enhancing awareness and prevention capabilities against complex cybersecurity threats.
The following content is from a report published by MSMT, and SlowMist is only providing translation and excerpts for readers to quickly understand the information, without representing SlowMist's stance on the content, views, or conclusions of the report.
Report link: https://msmt.info/Publications/detail/MSMT%20Report/4221

MSMT aims to monitor and report on behaviors that violate and evade sanctions measures established by relevant United Nations Security Council Resolutions (UNSCRs). MSMT member states include Australia, Canada, France, Germany, Italy, Japan, the Netherlands, New Zealand, South Korea, the UK, and the US, and its goal is to assist the international community in fully implementing UN sanctions against DPRK by releasing information based on investigations into sanction violations and evasion behaviors.
The report indicates that DPRK has continuously violated multiple UN Security Council resolutions in a systematic manner during the period from 2024 to 2025, through large-scale cyber attacks, cryptocurrency theft, and cross-border money laundering, as well as deploying information technology workers globally to evade sanctions and raise funds for its weapons of mass destruction and ballistic missile projects. The maturity of DPRK's cyber capabilities is close to that of cyber powers, with at least $1.19 billion in cryptocurrency stolen in 2024, followed by another $1.645 billion in the first nine months of 2025, with some cases laundered through globally registered cryptocurrency services and numerous over-the-counter brokers. The report also confirms that DPRK has dispatched IT workers to at least eight countries and relies on its overseas intermediaries and financial institutions to operate funds and identity cover; meanwhile, it continues to acquire sensitive technologies through malware, supply chain intrusions, and social engineering methods. Overall, almost all related activities are supervised by state-level entities that have been sanctioned by the UN and implemented through overseas shell companies and dispatched IT personnel, with its global evasion network continuously expanding.
I. DPRK Cyber Plans
The MSMT report indicates that DPRK's cyber capabilities have significantly improved in terms of organization, technical capabilities, and cross-border behaviors in recent years, with its maturity believed to be close to other cyber powers. This is primarily executed by multiple APT organizations carrying out remote infiltration, destruction, intelligence collection, and revenue generation tasks. These organizations are continuously expanding in scale, with new research centers, liaison offices, and activity clusters emerging, indicating a systematic expansion of DPRK's cyber system. Although the technical expertise and task directions of different units vary, the collaboration between cyber attackers and overseas IT workers is increasingly close, with significant overlap in tool development, technology sharing, and fundraising.
The report outlines the core organizational framework of DPRK's existing cyber capabilities, which can be roughly summarized in the following diagram:
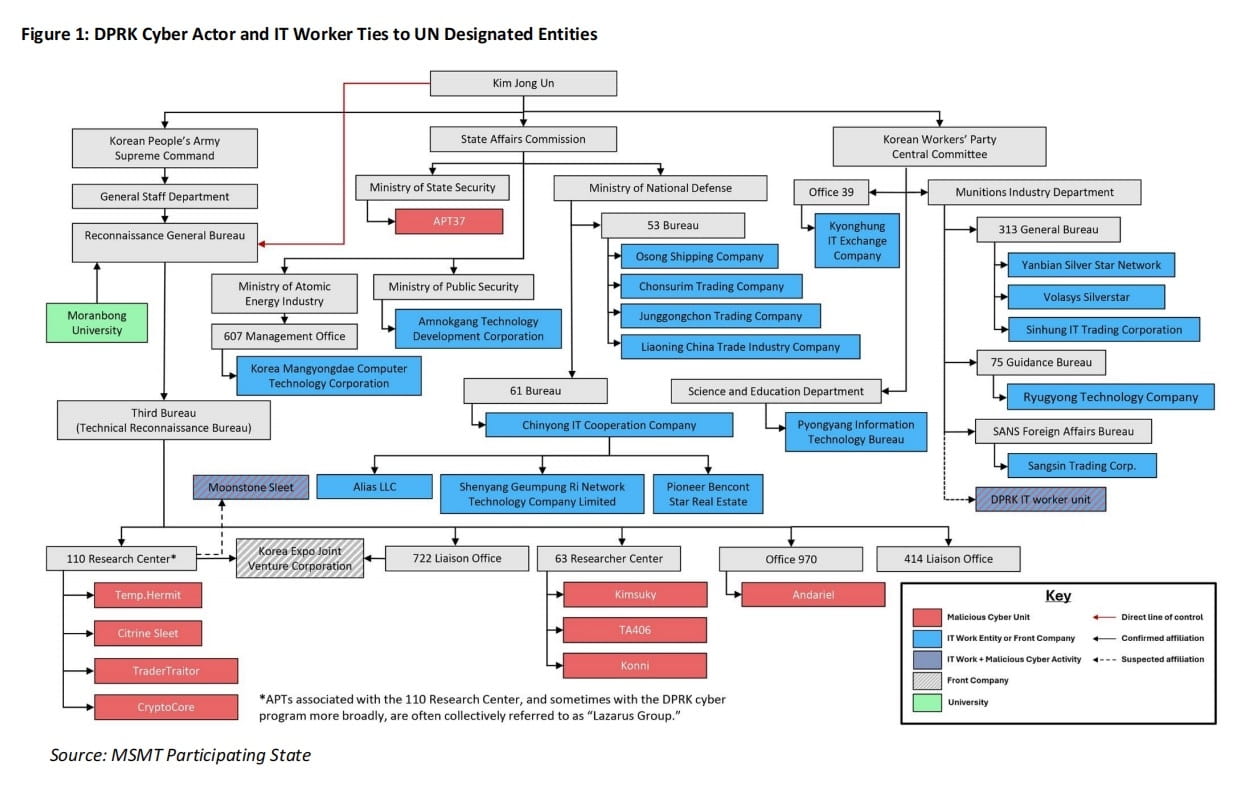
Overall, DPRK cyber operations function through a multi-layered structure both domestically and overseas, achieving multiple functions from malicious cyber activities, IT outsourcing revenue generation, to cross-border money laundering.
II. DPRK Cryptocurrency Theft Activities
Overall Revenue and Impact
Since 2017, due to domestic economic pressure and increasing international sanctions, DPRK cybercriminals have begun to use cryptocurrency theft as a means of generating revenue. At that time, the cryptocurrency industry was rapidly developing but lacked a mature regulatory framework and security measures, making it a target for their attacks. According to analyses by MSMT member states, Mandiant, and Chainalysis, DPRK stole at least $1.19 billion in cryptocurrency in 2024, a year-on-year increase of about 50%; from January to September 2025, it reached $1.645 billion, totaling at least $2.8 billion during the entire period from January 2024 to September 2025.
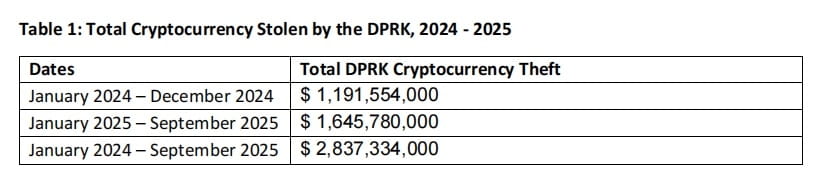
Major cases include the February 2025 TraderTraitor breach of the Dubai-based cryptocurrency exchange Bybit, stealing nearly $1.5 billion, marking the largest cryptocurrency theft in history. Additionally, exchanges like Japan’s DMM Bitcoin and India’s WazirX were significantly impacted, with some exchanges ceasing operations as a result. According to estimates from MSMT participating countries, the proceeds from cryptocurrency theft in 2024 accounted for about one-third of DPRK's total foreign exchange income, with the following cryptocurrency theft cases attributed to DPRK:
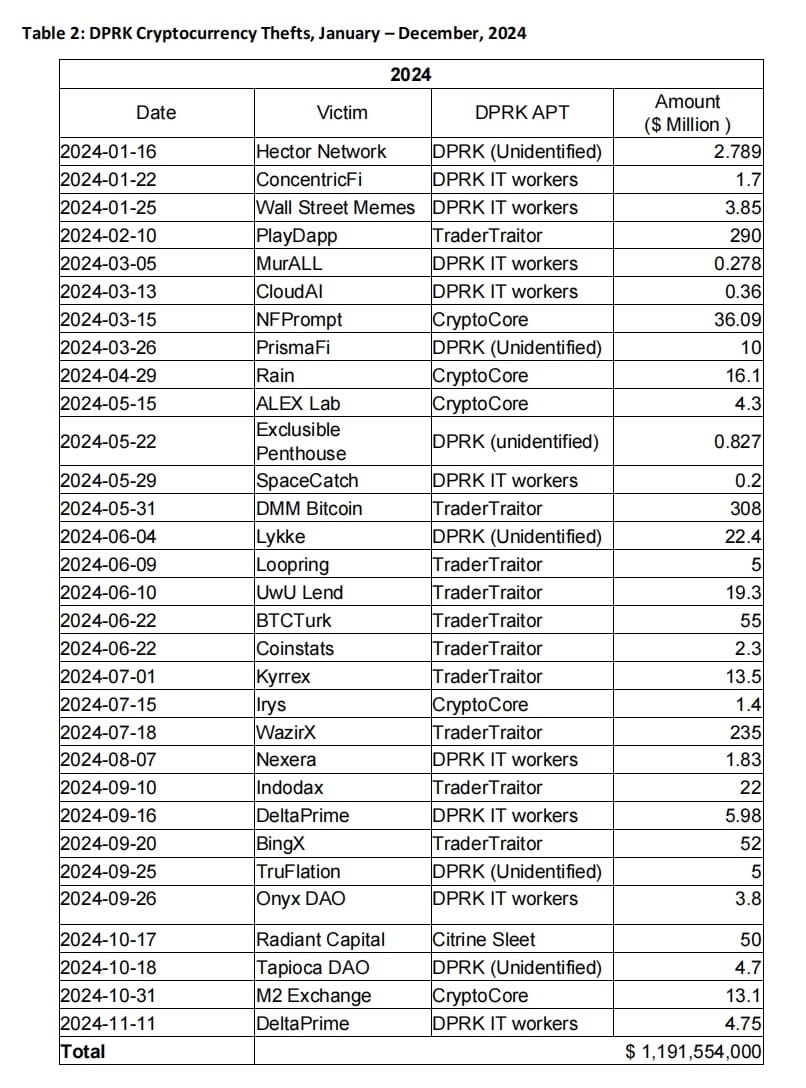
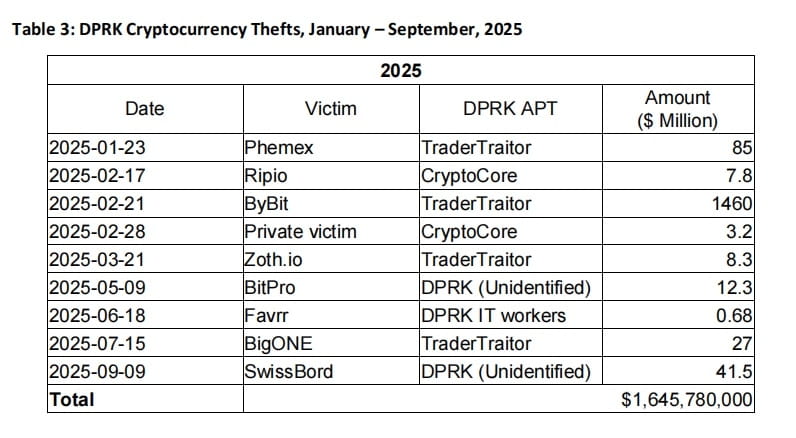
These incidents demonstrate that DPRK's cyber attacks not only pursue direct revenue generation but also expand the impact of attacks through supply chain attacks and third-party service intrusions, resulting in asset losses and operational disruptions for enterprises.
Participating Gangs and Organizations
According to the report, multiple DPRK APT organizations and IT personnel have participated in cryptocurrency theft, mainly including:
TraderTraitor (also known as Jade Sleet, UNC4899)
DPRK's most sophisticated cryptocurrency theft gangs, leveraging social engineering techniques and supply chain attack strategies to conduct large-scale theft, stole approximately $2.58 billion in cryptocurrency from January 2024 to September 2025. Key cases include the DMM Bitcoin, WazirX, and Bybit incidents, where attacks often obtained exchange credentials by compromising third-party custody services, bypassing security mechanisms such as multi-factor authentication and transaction limits.
CryptoCore (also known as Sapphire Sleet, Alluring Pisces)
The operational mode is similar to TraderTraitor, stealing at least $33.5 million from January 2024 to May 2025, with targets in the cryptocurrency industry including employees from companies in over ten countries globally. Attackers often use spear phishing attacks, disguising themselves as recruiters offering seemingly promising job opportunities to entice victims to execute their spread malicious code, links, or attachments; they also utilize malicious NPM software packages for skill assessment tests and subsequently infiltrate the victim's device after the social engineering attack.
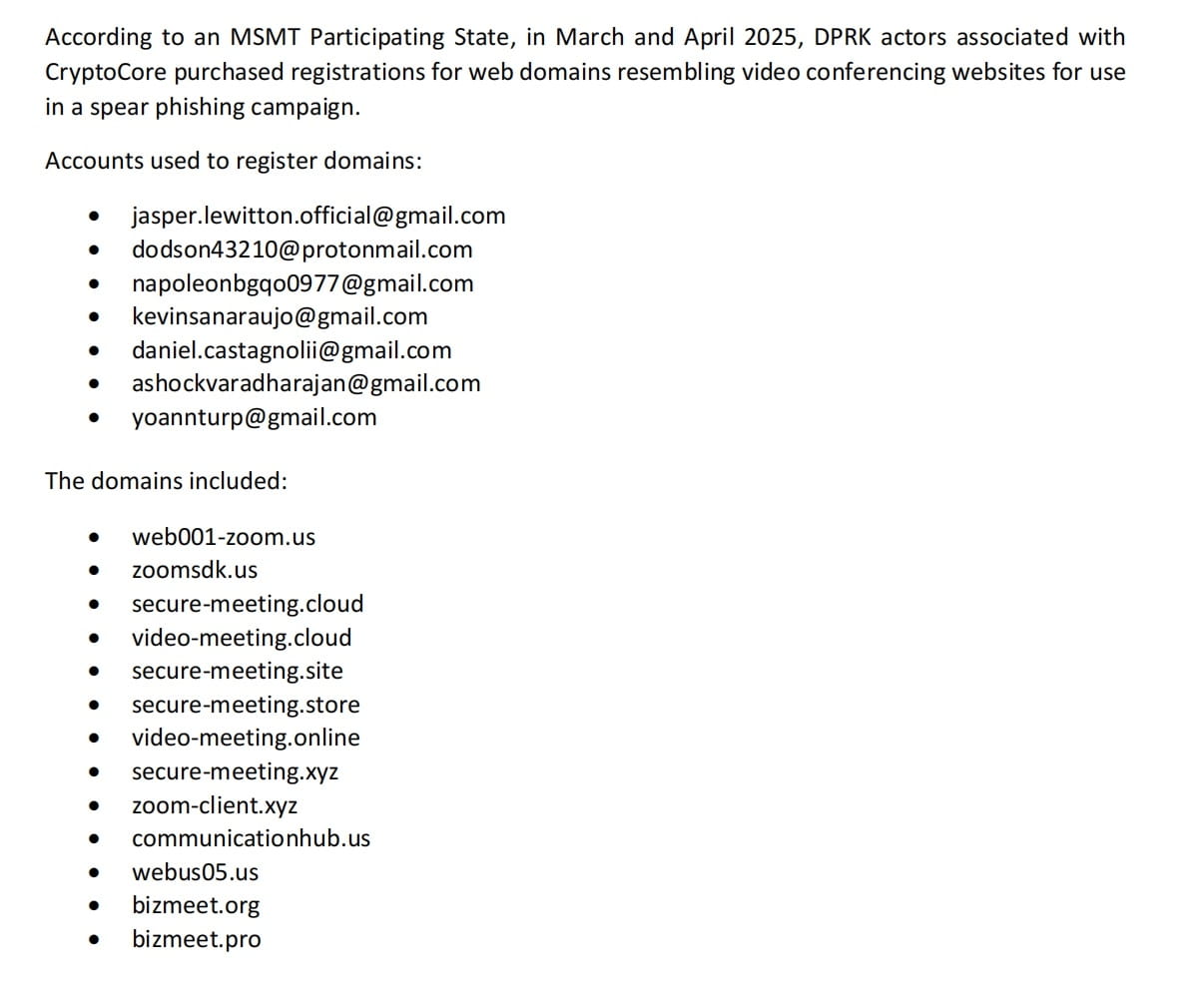
Citrine Sleet (also known as AppleJeus, Gleaming Pisces)
Focusing on spreading trojan-embedded cryptocurrency-related software, exploiting vulnerabilities in common internet infrastructure, and conducting social engineering attacks, this group became notorious in the early 2020s for its AppleJeus malware activities. A notable case in 2024 involved stealing $50 million from Radiant Capital, where the attacker precisely simulated the identity of a former contractor to gain the victim's trust.
DPRK IT Workers
According to relevant information, DPRK IT personnel have also participated in cryptocurrency theft activities, including the theft of cryptocurrency from Munchables ($62.5 million, which has been recovered), OnyxDAO ($3.8 million), Exclusible Penthouse ($827,000), and BTCTurk in 2024. The case of Munchables is particularly notable, as hackers may not have adequately prepared for laundering after the initial attack and were more focused on smart contract development rather than on-chain laundering, resulting in funds being intercepted.
Attack Methods and Techniques
DPRK APT organizations and IT personnel implement cyber attacks using diversified and highly organized methods, including:
Social Engineering and Spear Phishing
Recent attacks led by DPRK cyber actors indicate that their strategies have expanded from targeting core R&D personnel to various roles within the cryptocurrency industry chain, creating increasingly interconnected attack chains. Among them, 'Contagious Interview' is a typical attack activity specifically targeting software developers. This attack was first discovered by Palo Alto Networks in 2023. Attackers impersonated employers recruiting software developers, inviting target users to participate in online interviews and requesting them to download a software package that, once executed, would implant BeaverTail malware to steal sensitive data such as cryptocurrency wallets and credit cards stored in the browser, while secretly loading the InvisibleFerret backdoor for remote infiltration and persistent control. As we enter 2025, 'Contagious Interview' evolved into the 'ClickFake Interview' attack, expanding the target group to non-technical positions such as asset management and BD. Attackers first sent a link to users via social media, inviting them to visit a third-party website for a fake interview. Once victims entered the site, they were guided through a series of interview processes. When users were prompted to enable their cameras, an error message would pop up, suggesting they needed to download a driver to resolve the issue. At this moment, attackers would use 'ClickFix' technology to trick victims into copying and executing malicious commands: guiding macOS users to use curl to download and execute a malicious bash script (coremedia.sh); instructing Windows users to download a ZIP archive (nvidiadrivers.zip), unzip it, and run a VBS script (update.vbs) contained within the archive. Attackers also impersonated multiple company names (such as Coinbase, KuCoin, Kraken, Circle, Bybit, Tether, Robinhood, Archblock) to deceive victims into completing the application process. Meanwhile, the 'Wagemole' attack demonstrated different deception methods: attackers utilized generative AI tools like ChatGPT to create fake identities, build resumes, and simulate interview responses, infiltrating corporate internal systems as real IT outsourcing personnel to profit and carry out commercial espionage.
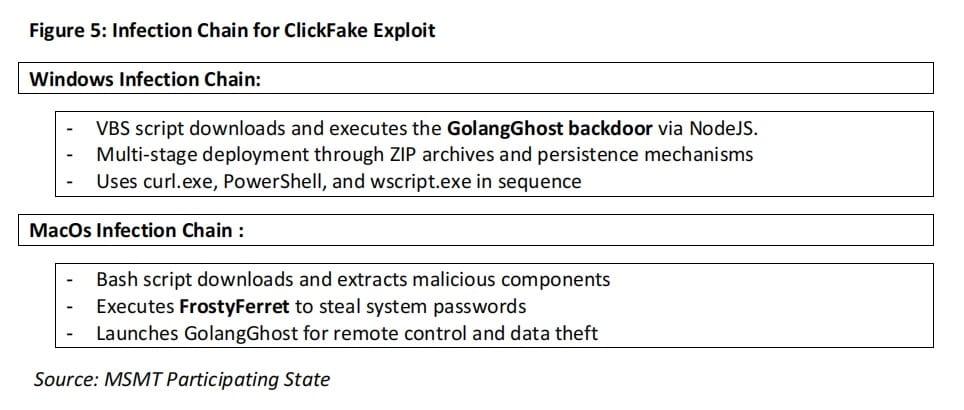
Ransomware and Selling Stolen Data
Between January 2024 and May 2025, organizations including Moonstone Sleet and Andariel (also known as Onyx Sleet, Silent Chollima, and APT 45) launched multiple ransomware attacks globally. Andariel's primary mission is to conduct cyber espionage but also carries out ransomware attacks to directly raise funds for its operational expenses, such as acquiring virtual infrastructure. The Moonstone Sleet organization, after stealing sensitive data, also employs simple extortion methods, demanding victims pay ransom to DPRK-controlled cryptocurrency addresses. DPRK cybercriminals also sell data, network access, and exploit programs acquired from ransomware and extortion activities on dark web markets or online crime forums for profit.
Cooperation with Overseas Cybercriminals
According to public reports, DPRK cybercriminals have been collaborating with overseas cybercriminals since the 2010s. At least since February 2025, DPRK cybercriminals associated with Moonstone Sleet have rented ransomware from a non-state Russian cybercriminal organization named Qilin (also known as Agenda). Between May and September 2024, hackers from the Andariel organization were found to be using known open-source malware (such as Dtrack) to compromise victim systems and deploy Play ransomware.
Utilizing Artificial Intelligence Tools
DPRK cybercriminals are using large language models (LLM) and generative AI, such as ChatGPT and DeepSeek, to enhance the authenticity of spear phishing, develop malware, and automate intrusion methods.
III. DPRK Cryptocurrency Money Laundering Activities
DPRK cybercriminals not only steal cryptocurrencies through cyber attacks but also need to launder the proceeds into usable funds to evade tracking by cryptocurrency exchanges, blockchain intelligence firms, and global law enforcement agencies. In most cases, stolen assets are ultimately exchanged for cash through over-the-counter (OTC) brokers and intermediary networks in third countries to support their priorities. DPRK cybercriminals are often observed to utilize various laundering tools and platforms, including cryptocurrency mixers, bridges, decentralized exchanges (DEX), cross-chain aggregators, and peer-to-peer (P2P) trading platforms, to obscure fund sources, diversify tracking paths, and evade regulation.
Money Laundering Processes
DPRK cybercriminals typically launder stolen cryptocurrencies through a complex multi-step process, and according to analyses provided by MSMT member states and private sector partners, common processes include:
Exchange (Swap): Mainly exchanging stolen tokens for ETH, BTC, or DAI through decentralized exchanges and storing these assets concentrated in non-custodial wallets. Tokens may also be exchanged for USDT and other stablecoins, such as USDD, but typically only for a very short time.
Mix: Sometimes quickly mixing these tokens before concentrating them in non-custodial wallets, for example, using Wasabi Wallet, CryptoMixer, Tornado Cash, JoinMarket, and Railgun.
Bridge: Using a series of Bridges, instant exchanges, and P2P trading platforms to convert ETH into other cryptocurrencies, mainly BTC.
Store: Storing funds in difficult-to-intercept cryptocurrencies (mainly BTC) that are usually kept in non-custodial wallets (including cold wallets).
Mix Again: Sometimes mixing cryptocurrency again, usually using Bitcoin mixers, and sending funds to non-custodial wallets.
Bridge: Using Bridges and P2P trading platforms to convert mixed BTC into TRX on Tron's network.
Exchange (Swap): Converting TRX into USDT and aggregating funds for withdrawal.
Exchange (Convert): Transfer USDT to an over-the-counter broker with an account at a centralized exchange.
Remittance (Remit): Receive fiat currency from an over-the-counter broker.
Despite criminals and money launderers constantly changing their laundering strategies and attempting to abuse various legitimate services, during the reported period, they consistently relied on certain specific platforms, and the following list is not exhaustive but compiled from various information sources:

Exchange and Cashing Channels
Cryptocurrency after laundering is usually exchanged for fiat currency through DPRK overseas affiliates, over-the-counter brokers, or intermediary networks.
Connections with Overseas Financial Systems
Multiple over-the-counter brokers have assisted DPRK cybercriminals in converting cryptocurrencies into fiat currency and transferring funds into DPRK-controlled bank accounts, usually charging a portion of the cryptocurrency as a service fee before delivering the equivalent fiat currency to DPRK affiliates.
According to information provided by MSMT member states, The DPRK’s First Credit Bank (FCB) has utilized an American financial services company to exchange US dollars for Chinese yuan and holds reserves in dozens of cryptocurrency wallets; some DPRK cybercriminals have also opened accounts in foreign financial institutions for money laundering activities.
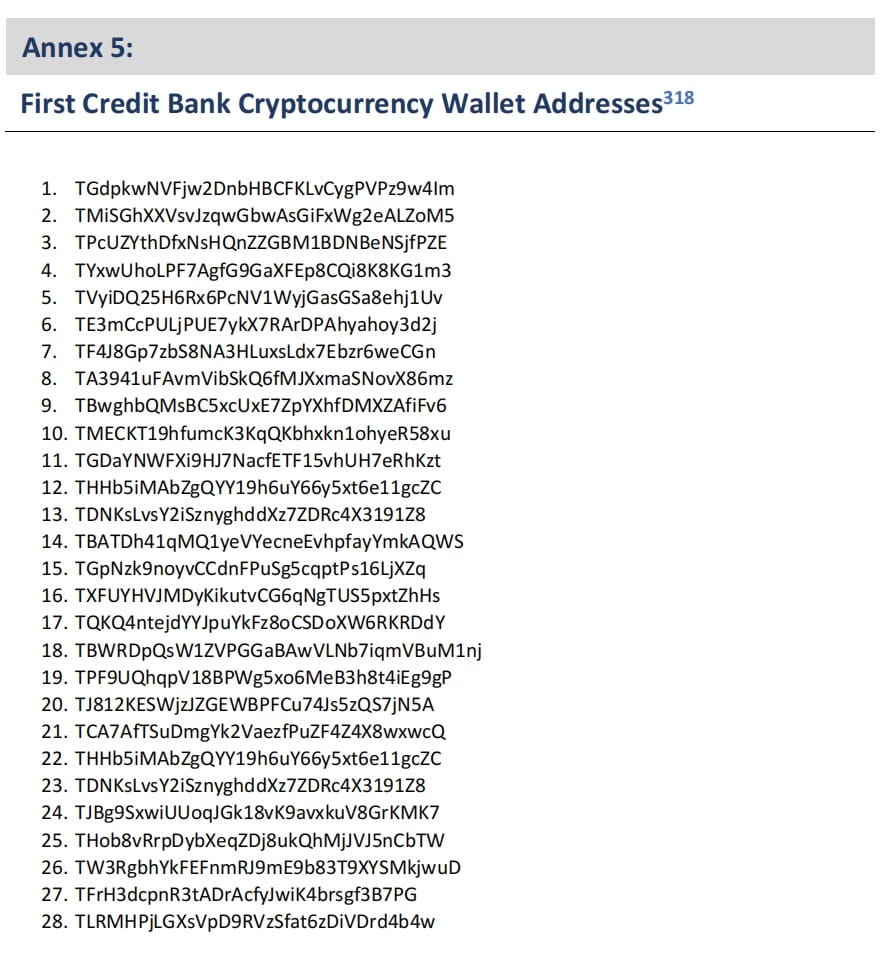
Overseas Intermediary Networks
Although DPRK cybercriminals typically participate personally in the money laundering process, they may also outsource laundering work to other third parties to expand the scale of laundering. For example, through Huione Pay in Cambodia and its affiliated accounts, stolen cryptocurrencies are exchanged for fiat currency and then transferred to other regions.
Using cryptocurrency for transactions and payments.
According to information provided by MSMT member states, at least since 2023, DPRK has attempted to expand the use of cryptocurrency from cybercrime to the exchange and payment for goods and services, such as using USDT in procurement-related transactions involving the sale and transfer of equipment and raw materials.

Using stablecoins for payments allows DPRK to bypass cash transportation restrictions, increase transaction convenience, and lower tracking risks, as issuers of stablecoins like Tether retain the ability to freeze and cooperate with law enforcement to freeze sanctioned transactions.
IV. DPRK Information Technology Workers
Overview and Strategic Role
According to the report, IT workers are the highest-paid group within the DPRK workforce. DPRK manages and supervises IT workers through higher institutions, ensuring that part of their income is used for infrastructure construction and procurement of consumer goods. Typically, IT workers are required to remit half of their income to higher authorities, retaining only 5% to 10% of their total income; in some cases, they may even have to pay these amounts out of their own pockets. In 2024, DPRK may generate approximately $350 million to $800 million in income from its global IT workers.
Each IT team is managed by a manager who sets monthly performance targets (usually at least $10,000 per person) and assists the team in obtaining authentication, payment accounts, and other necessary conditions. DPRK IT personnel dispatched overseas earn an average monthly salary of $10,000. The average income of DPRK domestic IT personnel may be roughly the same as that of overseas IT personnel, but overseas work offers broader opportunities for international business exposure.
Target Industries and Geographical Distribution
According to information collected by Mandiant for the MSMT report, DPRK IT workers operate globally, targeting industries including artificial intelligence, blockchain technology, website development, defense industry, government departments, and related research institutions. Some dismissed IT personnel have threatened to leak sensitive data from their former employers or provide it to competitors. This data includes proprietary information and source code for internal projects.
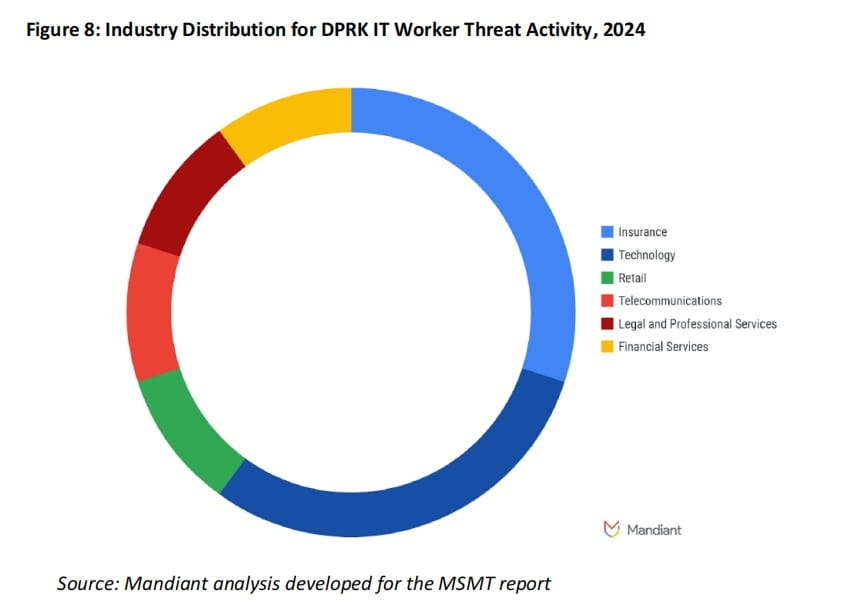
Geographical Distribution (2024 - 2025):
China: About 1,000 to 1,500 people;
Within North Korea: About 450 to 1,200 people;
Russia: About 150 to 300 people;
Laos: About 20 to 40 people;
Equatorial Guinea: About 5 to 15183 people;
Guinea: About 5 to 10 people;
Nigeria: Fewer than 10 people;
Tanzania: Fewer than 10 people;
Cambodia: Unknown.
IT workers typically acquire overseas positions through freelance platforms (such as Upwork, Freelancer, Fiverr), social media, and professional networks (such as LinkedIn, Discord). They often use multiple identities and forged documents to evade background checks and receive payments via cryptocurrency, Wise, and Payoneer.
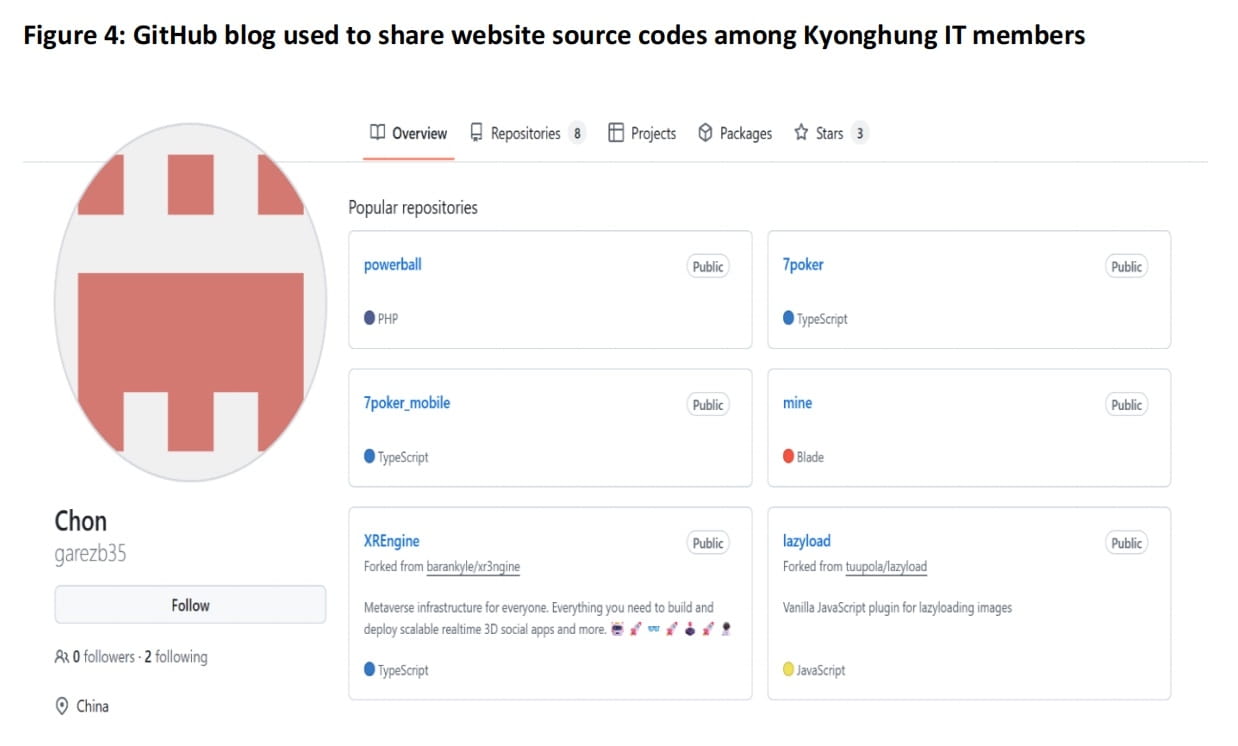
Operational Strategies, Techniques, and Processes
The common tactics of DPRK IT workers can be divided into three phases: establishing identity, applying for jobs, and receiving funds.
Phase One: Establishing User Profiles
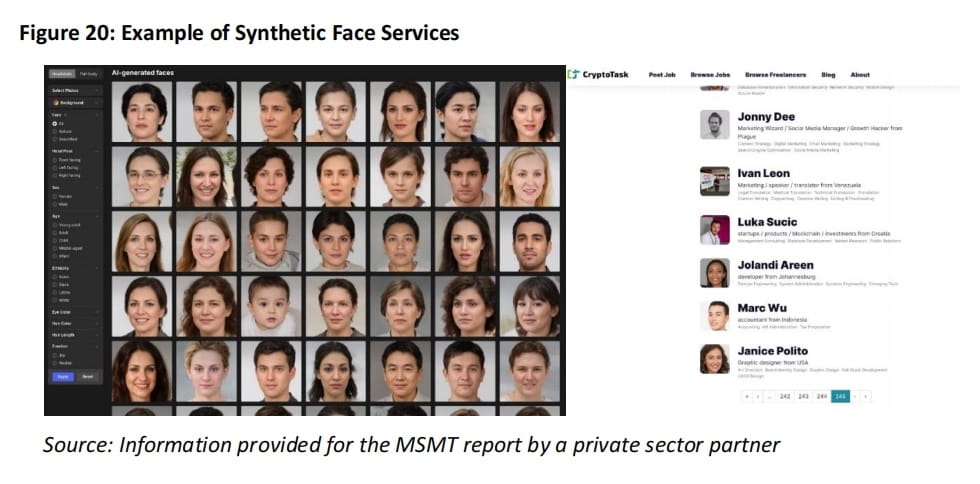
Using forged or stolen personal information (such as names, photos, and professional certificates) to create profiles; using AI (such as Thispersondoesntexist.com, generated.photos) to synthesize faces to beautify their profiles.
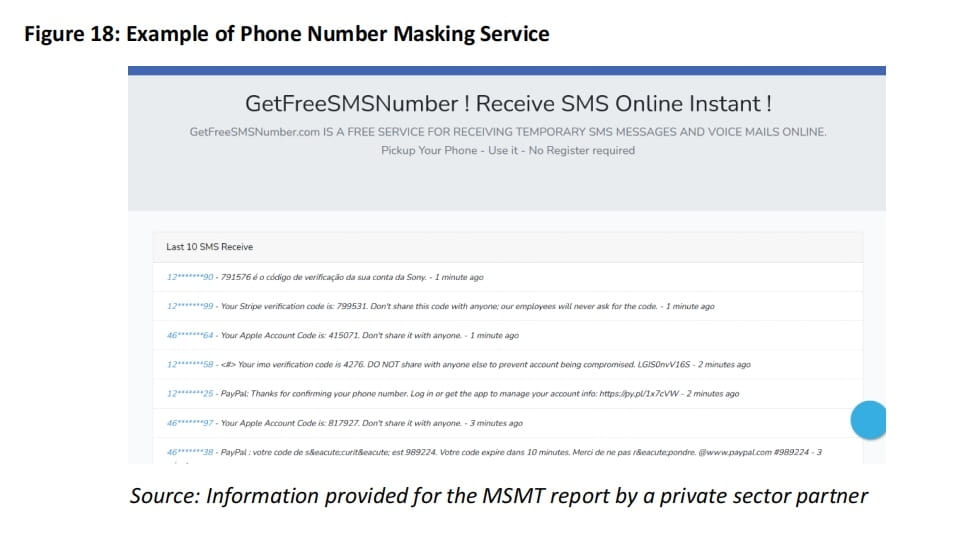
Using proxy services to create temporary virtual phone numbers for KYC verification; using synthetic KYC documents and submitting forged key verification photos to bypass ongoing or periodic identity verification.
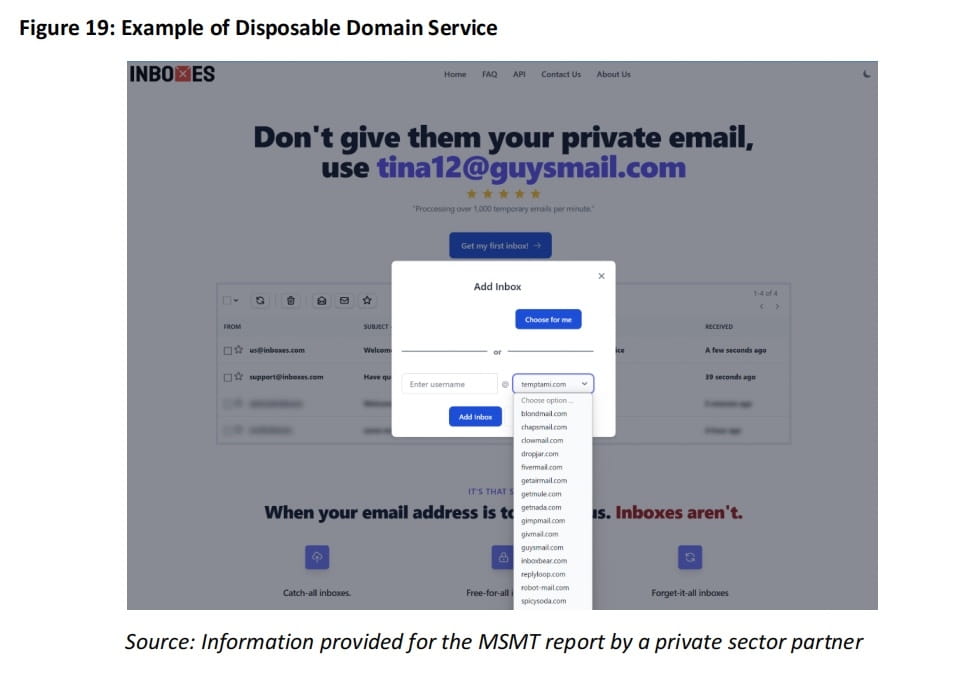
Using virtual private network (VPN) services to hide real locations; leveraging filtering aliases and Gmail's dot-filtering feature to create multiple email variants.
Purchasing accounts from verified account trading platforms or maintaining control over purchased accounts through remote access.
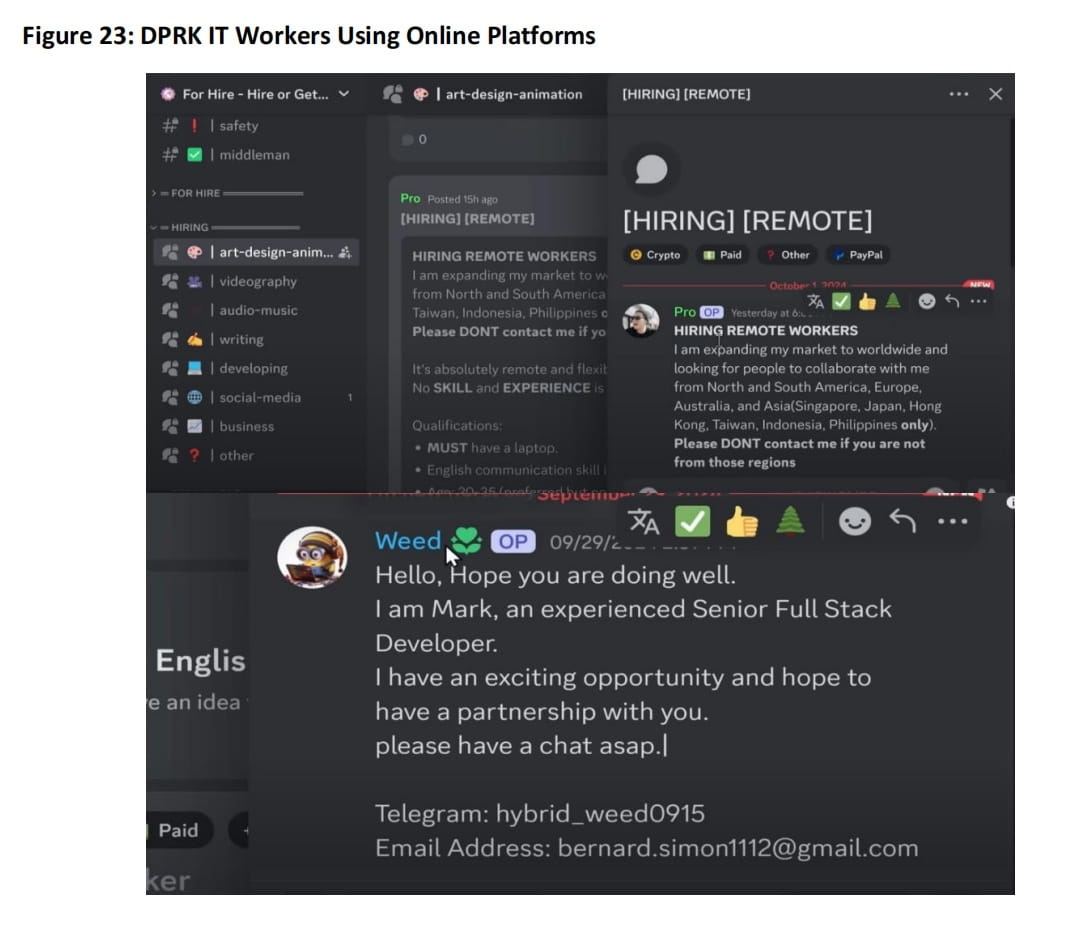
Phase Two: Job Application
Traditional Job Applications: Directly submitting resumes to companies, especially for remote positions.
Online Work Platforms: Building detailed profiles on platforms like Upwork, Freelancer, Fiverr, highlighting popular skills (such as blockchain and artificial intelligence), and trying to move communication to 'external' platforms like Telegram.
Alternative Platforms: Contacting potential clients and recruiters through LinkedIn, Discord, and professional forums to bypass structured vetting processes.
Phase Three: Receiving Funds
Traditional Financial Channels: Using bank accounts and payment platforms (such as PayPal, Payoneer, Wise) to receive payments and quickly transfer to seemingly unrelated third-party jurisdiction accounts.
Cryptocurrency: The preferred payment method, exchanged into fiat currency through mixing services or offshore exchanges to reduce tracking risks.
Additionally, according to information provided by MSMT member states: some DPRK IT workers have adopted different methods to exchange fiat currency for cryptocurrency, such as purchasing PayPal dollars (PYUSD) through third parties and then exchanging them for stablecoins USDC or USDT pegged to the dollar, limiting the transaction amounts to about $5,000 to $6,000 per day; from January to September 2025, DPRK IT personnel began to utilize foreign intermediaries or forged identification documents to obtain bank accounts supporting automated clearing systems (ACH) to facilitate faster deposits into DPRK-controlled Western financial institution accounts; DPRK IT personnel also began to establish shell companies by registering entities in the United States, allowing them to reduce scrutiny during interviews and obtain income from American companies; these strategies carry certain risks, including data breaches, intellectual property infringement, and potential legal liabilities.
V. DPRK Malicious Cyber Activities
Cyber Attacks Targeting South Korea (ROK)
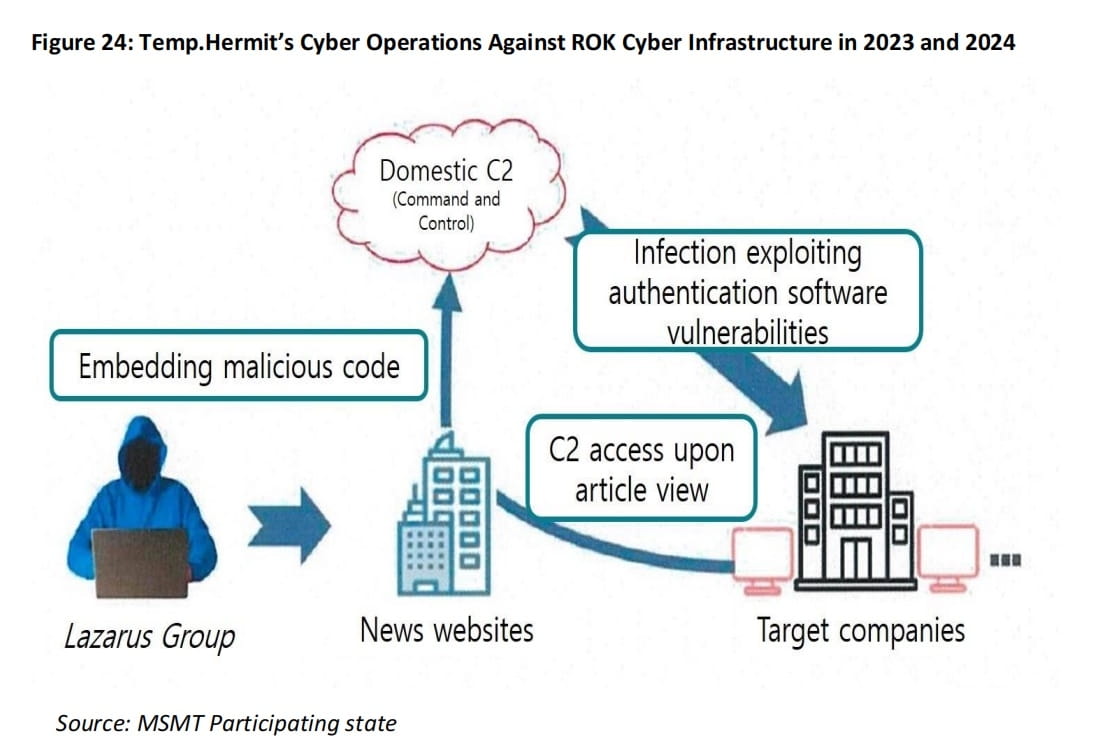
Temp.Hermit’s infiltration operations targeting South Korea's critical network infrastructure.
Between 2023 and 2024, Temp.Hermit disseminated malicious code exploiting vulnerabilities in commonly used identity verification software in South Korea, conducting 'waterhole attacks' on multiple South Korean news websites, implanting malicious code that infected users' computers accessing these sites. This code targeted vulnerabilities in identity verification software installed on infected computers and further spread, creating remotely controllable access points. Temp.Hermit also compromised IT asset management servers of certain South Korean institutions to identify potential weaknesses across the network.
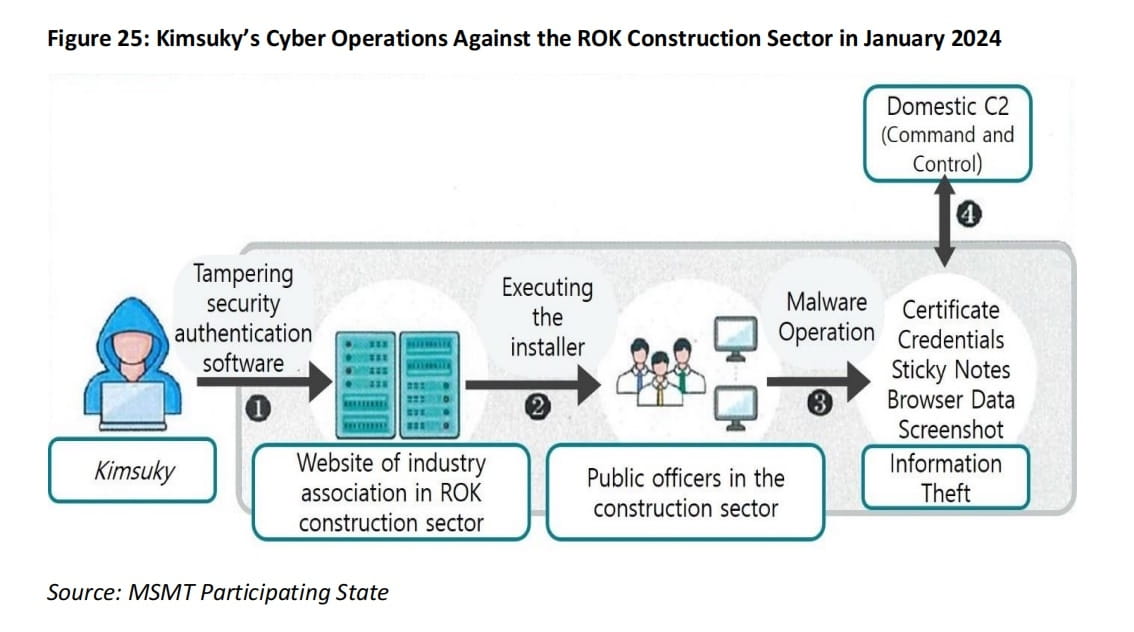
Kimsuky’s information theft campaign targeting the South Korean construction industry.
In January 2024, Kimsuky implanted the 'TrollAgent' malware on the South Korean Construction Industry Association's website, disguising it as a legitimate security certification tool, using stolen digital certificates to bypass detection. Through tampered documents, Kimsuky obtained user system information, browser data, screenshots, and login credentials. This data is believed to be used for further targeted attacks against South Korean public officials and major construction projects.
Defense Industrial Base (DIB) Targets
DPRK has long relied on cyber capabilities to drive the modernization of its weapon systems and acquire related research data. Multiple DPRK APT organizations continuously target aerospace, shipbuilding, satellite manufacturing, and military enterprises, often inducing employees to execute onboarding assessment tests containing malicious code through social engineering to steal sensitive technology material.
In December 2024, TraderTraitor breached the Chinese drone manufacturer DJI, stealing related materials for its drone R&D.
In May 2024, Andariel exploited a supply chain vulnerability in DLP software developed by a security company to launch attacks against multiple South Korean defense technology firms. The attackers controlled its central update server, distributing malware disguised as legitimate modules to downstream customers, and stole a large amount of sensitive data, including weapon design blueprints, from multiple enterprises.
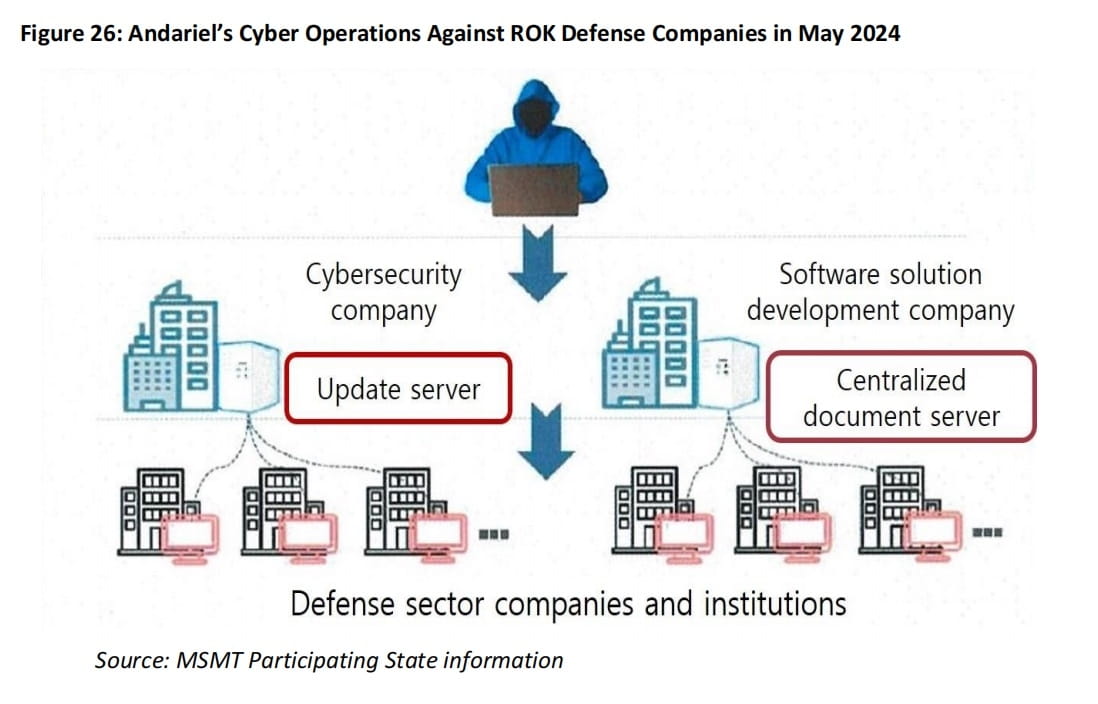
The MSMT report also points out that the boundaries between DPRK IT workers and APT organizations are becoming increasingly blurred. Some IT practitioners have assisted DPRK cyber organizations in identifying vulnerabilities in target industries, managing job databases, and even participating in malware deployment (such as BEAVETAIL and INVISIBLE FERRET). Some IT personnel apply for military or AI-related positions to gain technical experience for subsequent cyber operations, further strengthening the collaboration between the two.
Cyber Attacks Targeting the Public and Government Agencies
In May 2024, APT37 launched a massive attack exploiting vulnerabilities in common identity verification software in South Korea, targeting South Korean national security officials and DPRK-related NGO members. APT37 first compromised the servers providing advertising content, then delivered malicious code to users through zero-day vulnerabilities in the Internet Explorer engine. This operation ultimately installed the 'RokRAT' remote access trojan on infected devices, enabling attackers to conduct long-term surveillance and data theft.
VI. Conclusion
In light of the systemic cyber threats revealed in the MSMT report, the Web3 industry needs to gain an overall awareness of its security situation. DPRK-related attacks are no longer just external hacker intrusions but represent an integrated attack deeply combining IT worker infiltration, supply chain control, on-chain fund theft, and cross-border money laundering networks. For exchanges, wallets, infrastructure, and development teams, risks are no longer limited to technical vulnerabilities but stem from weak links across the entire chain of people, processes, and assets, especially in remote collaboration and outsourced development scenarios, where background checks, identity verification, code source review, and interview process security must become part of the security system.
Meanwhile, crypto assets have become an important channel for DPRK to evade sanctions and settle funds, with money laundering activities exhibiting cross-chain, high-jump, and highly disguised characteristics, meaning that on-chain monitoring and automated risk control have become necessary capabilities: SlowMist and MistTrack have accumulated a large number of malicious address clusters, laundering paths, and related intelligence while long-term tracking the activities of organizations like Lazarus and TraderTraitor, which can assist enterprises in reducing risks.
More importantly, the industry needs to upgrade from 'point defense' to 'systemic joint defense.' High-value targets such as exchanges, cross-chain bridges, custodians, and enterprises involving critical infrastructure should simultaneously strengthen deep defense at the network, supply chain, endpoint, and on-chain levels, introducing mechanisms such as zero-trust architecture, security monitoring, security auditing, and threat intelligence subscription.
In short, the report presents not just isolated attack cases but a comprehensive upgrade against the cryptocurrency financial system. Faced with such a mature and evolving adversary, the entire Web3 ecosystem must respond with stronger collaboration, sharper monitoring, and more complete defense strategies. Only by establishing continuous security capabilities covering personnel, supply chains, assets, and capital flows can the industry maintain security resilience in this long-term game.



