Every fast blockchain faces a dangerous trade-off: the faster you go, the more fragile you become unless you redesign the system entirely.
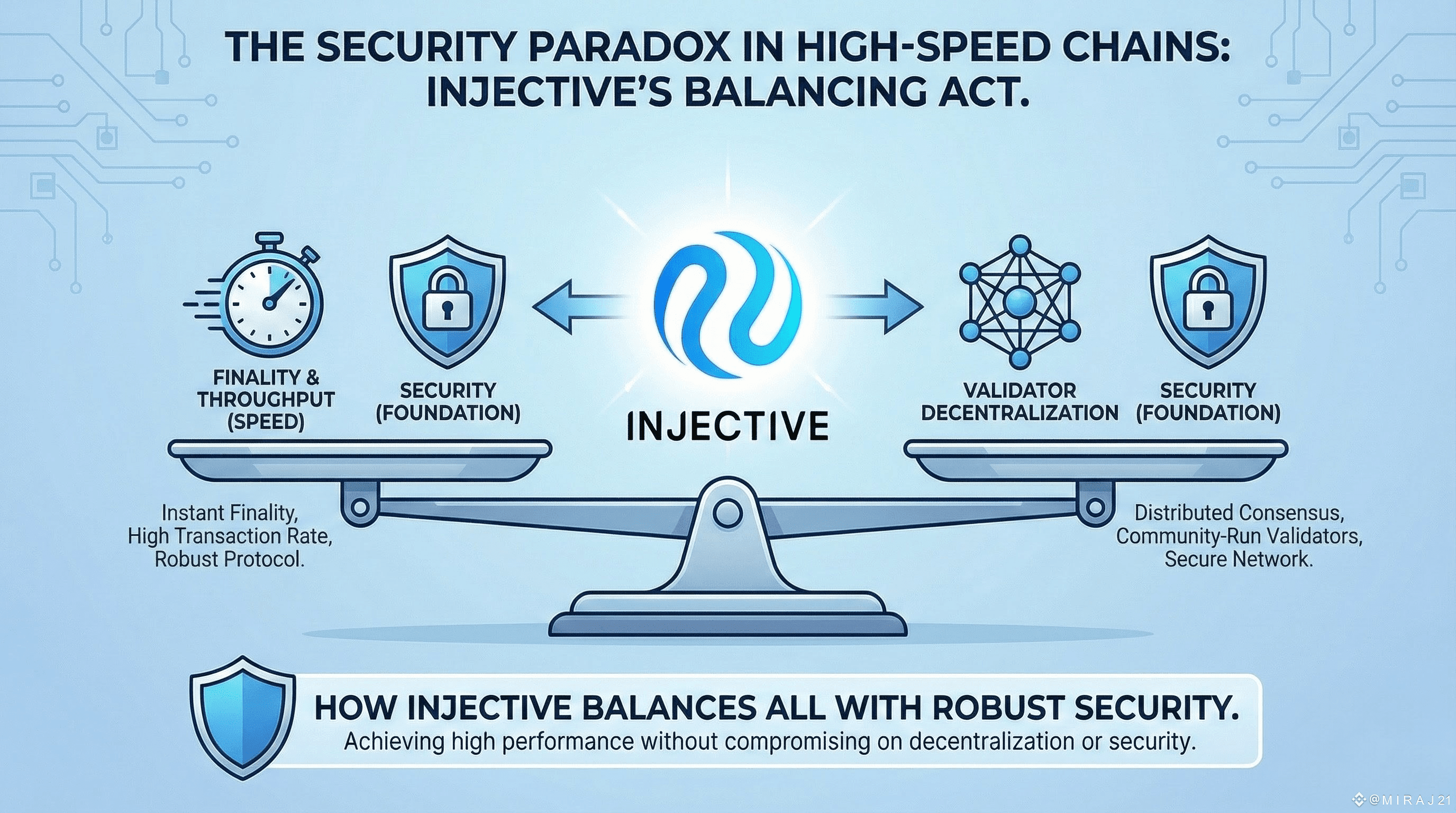 Rapid execution brings along a type of risk. When blockchains strive for finality in under a ultra-high throughput and quick consensus they frequently compromise the decentralization essential, for preserving security. This is the security dilemma: velocity boosts value. Heightens susceptibility, unless the chain manages to balance all three factors.
Rapid execution brings along a type of risk. When blockchains strive for finality in under a ultra-high throughput and quick consensus they frequently compromise the decentralization essential, for preserving security. This is the security dilemma: velocity boosts value. Heightens susceptibility, unless the chain manages to balance all three factors.
Injective stands out as one of the networks that addresses this dilemma via design choices that improve rather than undermine validator security and decentralization while delivering top-tier performance in the industry.
The majority of chains settle for two of the following: speed, security or decentralization. Injective is designed to achieve all three.
Conventional L1s settle for compromises since their consensus mechanisms were not designed for financial tasks. Validators face challenges from throughput. Quicker blocks increase demands, on resources. Decreasing the number of validators boosts speed. Concentrates authority.
Injective deviates from this trend by employing a method that maintains a strong validator group while still achieving fast finality.
Its design adheres to a principle:
Velocity ought to result from effectiveness. Not, from omission.
Finality on Injective is deterministic, not probabilistic a critical distinction for security.
Numerous "fast" chains provide block creation but have delayed or unpredictable finality. Within these networks a block might seem finalized yet remain susceptible, to reorganization, censorship or MEV-driven rearrangements.
The Tendermint-based consensus utilized by guarantees deterministic finality, which implies:
after a transaction is finalized it cannot be undone
validators are unable to split the chain unless they cooperate
settlement assurances remain intact despite traffic
assets, across chains remain protected against reorganization events
Such a degree of dependability is crucial, for derivatives, high-frequency trading and interchain settlement. Situations where finality's a necessity, not merely an option.
Elevated throughput results from optimized architecture not, by excluding validators.
Certain networks increase TPS by reducing the number of validators or mandating specific hardware. Injective sidesteps these centralization methods by enhancing:
block propagation paths
mempool ordering logic
validator signature aggregation
selective gossip reduction
state management and pruning
intelligent batching of financial operations
These enhancements lower the demands, on validators allowing for increased throughput without increasing entry barriers or restricting validator eligibility.
Decentralization is maintained by a validator set rather, than a restricted one.
A widespread misunderstanding is that fast chains need to lower the number of validators to keep block propagation. Injective shows this is unnecessary. Through enhancing consensus processes and message transmission the network:
maintains a broad validator ecosystem
protects against collusion
ensures geographic and jurisdictional diversity
reduces reliance on super-nodes or centralized infrastructure
This upholds the censorship resistance. Fault tolerance anticipated from a contemporary L1.
Block times, under a create fresh attack vectors. Injective manages these through deterministic sequencing and MEV protection.
When blocks confirm quickly harmful agents have reduced opportunity to take advantage of ordering weaknesses. The risks rise sharply if consensus breaks down. Injective safeguards its execution layer by:
eliminating the public mempool
preventing transaction reordering for profit
ensuring validators cannot manipulate inclusion timing
enforcing fairness at the protocol level
This implies that velocity is achieved without sacrificing market integrity. An attribute, for high-frequency financial uses.
Validator decentralization enhances security through the distribution of the verification process.
In chains, with a limited number of validators orchestrating an attack is simpler. Injective’s architecture prevents this risk by:
distributing consensus responsibilities
maintaining governance through a wide validator base
minimizing hardware specialization to keep participation open
using clear slashing rules to discourage malicious behavior
This guarantees that increasing throughput does not centralize power.
The true breakthrough is, in how Injective integrates its three elements: speed, finality and decentralization.
Injective did not develop every component individually.
It constructed them collaboratively so that:
decentralization improves conclusiveness
finality enables transaction completion
high throughput benefits from distributed validation
MEV resistance strengthens confidence, in execution
The chain operates not as a blockchain but as a high-efficiency financial market supported by decentralized consensus.
Cross-chain security enhances the significance of finality.
IBC-linked tokens, derivatives and settlements depend significantly on the finality assurances of the receiving chain. Injective’s deterministic finality guarantees:
no rollback risk for interchain assets
secure cross-chain arbitrage
predictable settlement timelines
safe integration with financial primitives on other chains
A breakdown, in finality would compromise the interchain liquidity framework. Injective’s architecture guarantees that this risk never materializes.
As blockchains advance into financial systems the security dilemma emerges as the key challenge.
The future of Web3 will be dominated not by blockchains that're just fast or just secure or just decentralized. But, by those that harmonize all three aspects. Injective showcases a model:
fast without being fragile
decentralized without being slow
secure without sacrificing innovation
This equilibrium is intentional. It represents the framework, for worldwide financial platforms, rapid trading, derivatives exchanges and decentralized liquidity systems.
Injective demonstrates that velocity and safety are not conflicting. They enhance each other when designed properly.
True performance isn’t measured by speed alone it’s measured by how fast a system can go without breaking its own trust guarantees.


