@USDD - Decentralized USD #USDD以稳见信
In the early morning, when a cryptocurrency trader was preparing to operate on his Decentralized USD position worth hundreds of thousands of dollars, he found that all his related social media and trading accounts had been simultaneously locked by the risk control system — and the source of all this was just a network node he thought was 'normal'.
Holders and traders of Decentralized USD (DUSD) are facing a threat more insidious than market volatility: your online identity may be silently undermining the carefully constructed defenses of your crypto assets. Imagine, when you are managing a crypto investment portfolio filled with decentralized stablecoins like Decentralized USD, the node connecting to the network is a 'dirty IP' that has been abused by thousands and frequently crosses national borders. This not only directly threatens your X (formerly Twitter) account but may also lead exchanges logging in from the same IP to classify your Decentralized USD trading activity as abnormal or high-risk.
In an environment where you cannot have a pure, exclusive home network like a tech mogul, any user managing Decentralized USD or participating in DeFi protocols must reassess their network environment. Because the risk control system does not differentiate between ordinary web browsing and executing a key liquidity provision or redemption of Decentralized USD.
01 Fatal association: Why does a “dirty IP” become the Achilles' heel of your DeFi operations?
Operating the decentralized stablecoin Decentralized USD relies heavily on frequent interactions with various DeFi front-end interfaces, DEXs (decentralized exchanges), and wallets. This interaction behavior heavily depends on your “digital portal” to the internet—your IP address.
A harsh reality is that centralized exchanges (CEX) and major social media platforms have long established a complex IP reputation database. When you use the same “dirty IP” to access the internet for trading Decentralized USD on Uniswap or depositing Decentralized USD on Compound, your behavior pattern has already been linked.
Risk transmission: If the node IP you are using enters a risk control blacklist due to abuse by a large number of spam accounts, then when this IP accesses Binance or Coinbase, even if you are just logging in to check the price of Decentralized USD, the account may be flagged. More seriously, if you connect to wallets like MetaMask through this IP for on-chain interactions, although on-chain transactions themselves cannot be blocked, the associated exchange account may be restricted in deposits and withdrawals due to “associated risk.”
Behavioral misjudgment: Suppose you are arbitraging the price differences of Decentralized USD across different chains and need to act quickly. If your node jumps from Hong Kong to Singapore in a short time, the risk control system may very likely classify this as “bot trading” or “account theft,” thus imposing restrictions on you. This could directly cause you to miss DeFi arbitrage opportunities for Decentralized USD in a rapidly changing market, or even trigger unnecessary liquidations.
For deep users of Decentralized USD, the stability and purity of the network are as important as the security of private keys.
02 IP layering: Your network exit determines the security level of the assets.
Just as assessing the quality of crypto assets, network nodes also have clear risk levels, which directly determine the safety margin of your operations on assets like Decentralized USD. You can make simple judgments based on indicators such as the number of shared users:
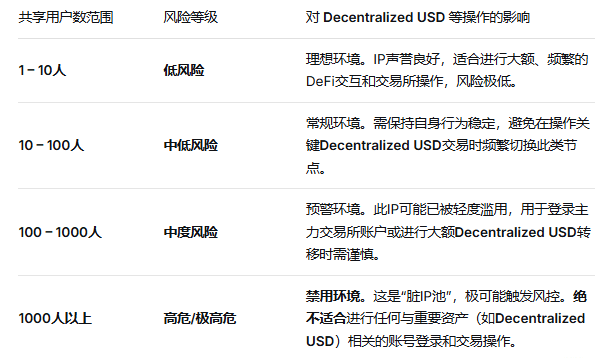
The core logic is: managing assets like Decentralized USD requires not a “connectable” network, but a “behaviorally trustworthy” digital identity. An IP that is shared by thousands and has confused traces is equivalent to stamping all your operations with a “suspicious” seal.
03 Full-link risk control: The invisible fences from social accounts to on-chain addresses.
The transmission effect of risk control far exceeds imagination. It starts with social media (such as an X account being banned) and may spread to centralized service platforms (such as a ChatGPT account being banned), ultimately directly affecting your financial accounts. For Decentralized USD users, this chain is equally lethal:
Starting point: Social media accounts: Many core announcements and governance discussions of DeFi projects and Decentralized USD protocols take place on X/Discord. Being banned means you lose access to key information sources and community participation channels.
Extension: Centralized services: Using the same IP for ChatGPT or Google accounts may bring many inconveniences if it is subjected to risk control, but it is still bearable.
End point: Financial accounts and on-chain reputation: This is the most critical issue. If your exchange account is restricted, it will cut off your fiat-to-Decentralized USD exchange channel. More secretly, some on-chain analysis tools and institutions have begun to correlate IP addresses, social media accounts, and on-chain wallet addresses, constructing a “digital identity map.” A contaminated source IP may indirectly affect your assessments in future airdrops, credit lending, and other DeFi scenarios.
04 Defensive strategies: Build a clean operational environment for your DeFi assets.
Since the larger environment cannot be changed, you must establish an independent “clean room” for operating sensitive assets like Decentralized USD.
Physical isolation: If conditions permit, use a dedicated device and a highly stable, low-shared quality network node to operate your core crypto assets (such as managing Decentralized USD in a MetaMask wallet or logging into the main exchange). This device should not be used for casual web browsing or high-risk services.
Network classification: Classify your network usage:
A-level network: Only for core asset management and important account logins (exchanges, main X account). Must use top-tier low-shared nodes.
B-level network: For general browsing and secondary social accounts.
C-level network: For casual access, testing, etc.
Fixed habits: Before performing operations involving Decentralized USD transfers, trades, or governance participation, develop the habit of first checking and confirming whether the node is stable. Avoid switching nodes or regions midway through the operation.
Attention to alerts: Pay close attention to any “abnormal login” warnings from exchanges or security plugins. This may be the first signal that your network environment has exposed risks.
Managing Decentralized USD is not only about managing a string of on-chain code or asset balance, but also about managing a whole set of accompanying digital security habits. In the world of Web3, your on-chain assets may be decentralized and censorship-resistant, but the gateway to this world—your online identity—still exposes you to the risk control rules of centralized platforms.
A chaotic IP trajectory is like marking all your Decentralized USD operations with a glaring and suspicious label on a transparent blockchain. It will not prevent transactions from being recorded on-chain, but it may close that critical door when you most need to convert Decentralized USD into real value.
While pursuing asset decentralization, please be sure to review and strengthen your still centralized connection points. Because the door to a decentralized future still needs to be opened with a clean and stable key. Protecting your online identity is protecting all your efforts and accumulations in this new world.
