The article analyzes the development trends of the wallet sector in 2025, pointing out that although the market seems solidified, existing players have undergone significant changes in ecological positioning and underlying technology. Wallets are transitioning from a single-chain era to multi-chain compatibility and gradually shifting towards business competition, such as aggregated DEXs and cross-chain bridges. At the same time, upgrades in custody technology, such as the application of TEE technology, have enhanced security and user experience. The article also looks forward to the potential of wallets in AI trading and Cedefi products in the future.
1. Introduction
In the blink of an eye, the author has been cultivating in the wallet sector for 4 years.
Many people feel that the wallet sector in 2025 has already solidified, but the reality is not so — it is surging beneath the surface; in this year:
Coinbase has just released the CDP wallet, built on TEE technology.
Binance's MPC wallet introduces key sharding custody into the TEE environment.
Bitget just launched the social login feature last week, hosted by TEE.
OKX Wallet launched a TEE-based smart account feature.
MetaMask and Phantom have introduced social login, which is essentially key sharding encrypted storage.
Although there haven't been any standout new players this year, the existing players have undergone tremendous changes in ecological positioning and underlying technical architecture.
This transformation stems from the drastic changes in the upstream ecosystem.
As BTC and the inscription ecosystem fully recede, many wallets begin to adopt a new positioning as "gateways" to accommodate emerging tracks such as Perps (perpetual contracts), RWA (stock-related), and CeDeFi (combination of centralized and decentralized finance).
This transformation has actually been brewing for years.
Following this article, let us delve into understanding those flowers blooming in the dark and their impact on future users.
2. Review the development stages of the wallet track
Wallets are rare products with essential demand in the blockchain industry and are also the entry-level applications that have broken through ten million users, apart from public chains.
2.1 First Stage: Single-Chain Era (2009-2022)
In the early industry (2009-2017), wallets were extremely difficult to use and even required local node operation. We will skip this stage.
At the usable stage, self-hosting becomes the first choice — after all, in a decentralized world, "default distrust" is the foundation of survival. Well-known products like MetaMask, Phantom, Trust Wallet, OKX Wallet, etc. are the leaders of this period.
From 2017 to 2022, the market experienced an explosion of public chains/L2. Although most chains still use Ethereum's EVM architecture, creating a compatible good tool is sufficient to meet demand.
During this period, the core positioning of wallets is "good tools." Although there are visible commercial prospects for traffic entrances and DEX entrances, safety, usability, and stability are the primary requirements.
However, from 2023 to 2025, the situation has changed.
Heterogeneous public chains like Solana, Aptos, and BTC (during the inscription period) have completely captured the user market. Although Sui itself is developing well, after the hacker incident, large funds have hesitated due to the drawbacks of excessive centralization.
Driven by the financing era of "fat protocols, thin applications", although VCs have little return, the market landscape is indeed changing.
2.2 Second Stage: Multi-Chain Era (2022-2024)
Faced with the multi-chain landscape, even strong players like MetaMask have had to transform, starting to support Solana, BTC, and more natively. Leading players like OKX Wallet and Phantom have also implemented multi-chain compatible architectures early on.
The core sign of whether multi-chain compatibility exists is how many chains are supported and where the transactions originate — this represents a large amount of work for the backend, while the client only needs to sign. From the user's perspective, it is whether they need to find RPC nodes themselves to use the wallet.
Today, multi-chain compatibility has almost become standard. Long-term adherence to single chains is likely to become unsustainable as the hot spots of chains continue to change.
A typical example is the Keplr wallet, which focuses on the Cosmos ecosystem, but this track has never taken off. Many application chains quickly built on Cosmos gradually fell silent after launch. As the threshold for building EVM L2 becomes lower, the situation for single-chain wallets may ease, but the ceiling is also there.
Once the basic tools are good enough to use, users begin to awaken their commercial needs in wallets!
True asset owners not only need to custody their assets but also actively drive them — seeking the best yield locations and choosing interaction partners. However, users are also tortured by the complexity of interactions with various DApps and must constantly guard against phishing sites.
Since this is the case, why not directly utilize the built-in functions of the wallet?
2.3 Business competition branching period
The competition focus among various wallets has shifted to the business layer, typically aggregating DEX and cross-chain bridges. Although Coinbase has explored integrating social features, this demand has been too superficial and has remained lukewarm.
Returning to the essential needs, users require the ability to complete multi-chain asset transfers at a single wallet entry point. At this time, coverage, speed, and slippage become core competitive points.
The DEX field can further extend to derivative trading: RWA (such as tokenized stocks), Perps (perpetual contracts), prediction markets (which will be hot in the second half of 2025, especially since the World Cup will be held in 2026).
Alongside DEX, there is also the demand for DeFi yields.
After all, on-chain APY will be higher than traditional finance:
Coin-based strategy: ETH staking yields about 4% APY, Solana staking + MEV yields about 8% APY (details can be found in the extensive report: The evolution and pros and cons of MEV on Solana), and more aggressive participants can engage in liquidity pools (LP) and cross-chain bridge LPs.
Stablecoin strategy: Although yields are relatively low, combining cyclical leverage operations can enhance APY.
So by this year (2025), at the peak of business competition, wallet infrastructure will once again undergo upgrades.
The reason is that the above transactions are too complex — not only due to the complexity of transaction structures but also the complexity of transaction lifecycles.
To achieve truly high yields, it is necessary to incorporate automated trading: dynamic portfolio adjustments, timed limit orders (not just supporting market orders), dollar-cost averaging, stop-loss, and other advanced functions.
However, these features were impossible to achieve in the pure self-hosting era.
So, should it be completely "security first" or "profit first"? It’s not a difficult question because the market has different demands.
Just like during the era of Telegram Bots, many players handed over their private keys in exchange for automatic trading opportunities — a high-risk model of "if you're afraid, don't play; if you play, don't be afraid." In contrast, large service providers must consider brand and reputation when providing wallets.
Is there a solution that can securely host private keys while also relatively ensuring that the service provider does not go bankrupt?
Of course there is! This has ushered in this year's upgrade of underlying custody technology.
3. Underlying technology custody upgrade period
Returning to the underlying technology upgrade mentioned at the beginning of the industry, let us analyze them one by one.
3.1 Farewell to the era of complete self-hosting
Firstly, actions taken by pure wallet vendors like Metamask and Phantom are relatively lightweight. They are more experience-driven, as social logins are only addressing user needs for cross-device access and recovery, not fully entering specific application layer tracks.
However, their transformation is, to some extent, a farewell to the era of complete self-hosting.
Self-hosting has degrees of distinction, but no one can truly define what is complete and what is incomplete.
Firstly, self-hosting itself means that the user's private key can only be stored on the user's device. However, this has already posed many problems in the past.
Locally encrypted storage of private keys could be at risk of brute force if the device is compromised, and its strength relies on the user's password.
When synchronizing across devices and backing up, copies must be made, which makes the operating system's clipboard permissions a matter of life and death.
What is memorable is that a certain wallet vendor's page for copying private keys only defaults to pasting the first part, requiring users to manually type the remaining digits. This directly led to a more than 90% drop in reported private key theft cases during that time. Later, hackers adapted and also brute-forced the remaining digits, entering a counter-offensive period.
After the Ethereum Prague upgrade, due to the high permissions of 7702, signatures have become very obscure, even leading to special cases with a full-chain impact, which has further stimulated the high phishing risk associated with permit 2.
Therefore, the essence of self-hosting is that users cannot easily adapt to completely controlling their assets due to the industry background.
After all, if the private key is with the user, there is naturally no problem. However, if an encrypted copy of the private key is kept on the server to prevent the user’s local device from being lost, then the assets could be completely lost. Can this still be considered self-hosting?
The answer provided by Metamask and Phantom is also yes. However, at the same time, it is necessary to prevent the service provider from acting maliciously.
3.2 First, let's talk about Metamask
His approach is simple: users need to log in with an email and set a password. The two combine to form something called TOPRF (Threshold Oblivious Pseudorandom Function), which encrypts the user's private key. The encrypted private key can naturally be backed up.
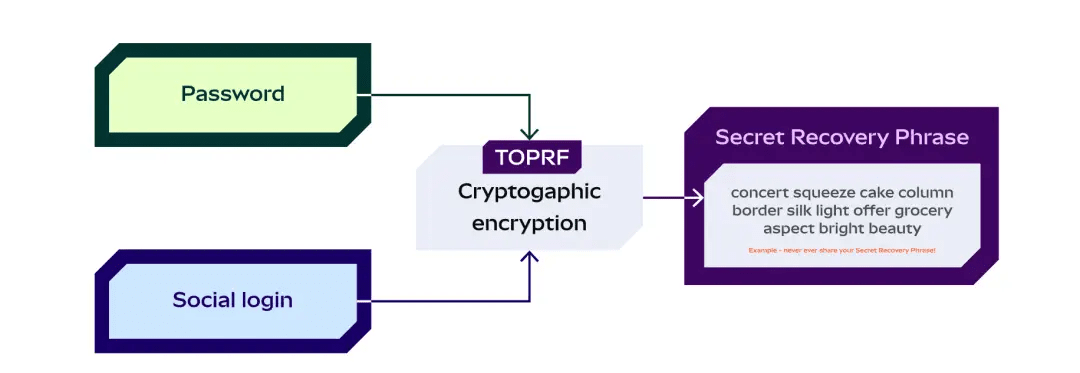
Then this TOPRF is distributed through a typical SSS (Shamir Secret Sharing) method. The social login service providers will obtain encrypted data through social verification and must combine it with the user's password to fully decrypt.
Thus, security risks are not completely absent; after all, weak passwords and email theft also pose risks. Moreover, if users forget their passwords, recovery becomes impossible. However, the benefit is that it is more convenient, and the experience is fundamentally consistent with Web 2.0.
3.3 Looking at Phantom
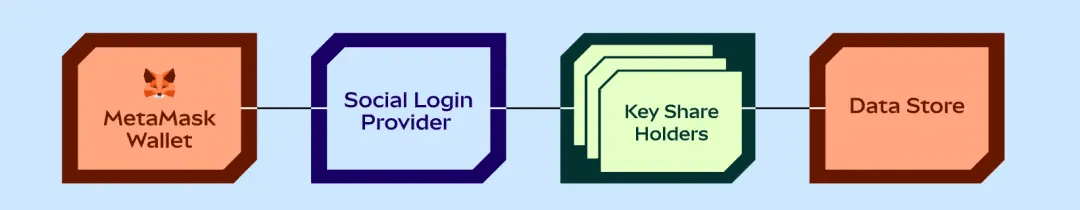
Looking at the chart, the overall architecture is somewhat complex, but the essence is still back-end encrypted storage of private keys, using sharding management for encryption and decryption keys.
In contrast to the small fox, the key used for encryption is divided into two parts. It introduces another service provider called JuiceBox to store one part, requiring social login + PIN (4 digits) to use its shard.
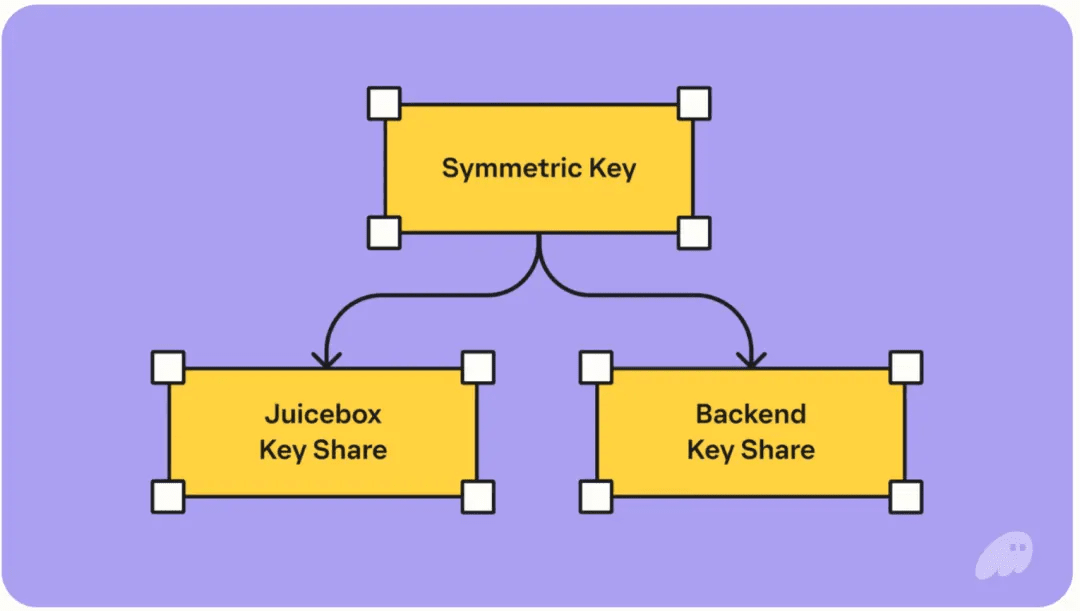
Overall, users only need their email not to be stolen and to remember their PIN, then they can recover anytime.
Of course, in extreme cases, if JuiceBox colluded with Phantom, it could also decrypt assets, but at least the cost of attacks on hackers would shift from a single point to multiple parties. Moreover, since JuiceBox is a network, its security design would also share the burden among multiple validators.
It can be said that, in terms of social recovery, these two are making certain compromises while adhering to bottom lines, but it is at the expense of user experience for the sake of low-probability events.
The author believes it is a good change; after all, what the blockchain industry needs most is to embrace ordinary users, rather than forcing ordinary users to become industry experts.
4. Adopt a self-hosted trusted technology environment Tee
The previous social login can only solve the recovery problem, but cannot solve the problem of automated trading.
Each company has slightly different approaches for this.
First, let’s popularize the background: Tee stands for Trusted Execution Environments. It is essentially a type of server, but this server can ensure that its memory environment and execution process cannot be read or interfered with, even by AWS service providers or the owner of the server.
Additionally, once he starts running the program, he will publicize a document called Attestation, which the party interacting with Tee can verify whether this document is consistent with what he has publicly disclosed.
Only when the program he runs conforms to the specified version of open source will the two correspond, thereby proving trustworthiness. This point has been widely applied in the industry:
For example, the official cross-chain bridge of Avalanche uses SGX (a certain type of Tee) for the notary validator.
For example, the Ethereum mainnet already has 40% of the blockchain transactions being completed through the underlying buildr net, which is also TEE.
Not to mention various financial banks, which strictly control to prevent insider risks, have also basically introduced Tee. Leading exchanges have also introduced Tee at high prices for hot and cold wallet signature custody under the compliance framework of 2025.
Although there are indeed many difficulties in using Tee, such as low machine performance (which can be compensated with money) and the risk of downtime (loss of memory information), as well as complex upgrades.
The remaining question is how various exchanges provide Tee services in wallets?
4.1 Coinbase and Bitget's solutions
Initially, it is hard to imagine that exchanges like Coinbase, which are compliant and publicly traded in the US, are actually the most centralized versions.
And Bitget's logical architecture is almost consistent.
In essence, he is only using Tee to generate private keys and drive signatures, but how does Tee verify whether this service truly reflects the user's intention?
Coinbase is entirely based on user login, forwarding instructions to Tee after backend authentication and then completing transactions.
Bitget is also the same; although there is little information, it currently appears that there is no signature page process during the endpoint, and it directly sets the new address to the eip-7702 address, thus achieving gas payment.
The advantages of this system can be said to ensure that at least the user's asset private keys are indeed in Tee, but whether the backend will insert other strange instructions into it cannot be verified or falsified.
But fortunately, there is evidence on the chain.
Therefore, I believe that Coinbase and others essentially add the credibility of exchanges. After all, whether the private key is exported is certainly recorded, which can eliminate the risk of users committing fraud. The only risk is that the exchange itself acts maliciously, which is actually consistent with the underlying model of user trust in CEX.
4.2 Bn and Okx
Comparing the MPC and SA from these two companies, the logical essence is also the same. In driving transactions, okx will pop up a set of intention authorization signature pages. This, combined with the logic of verifying intentions within Tee, allows for a higher degree of user authorization, but also increases the overall understanding cost for users.
Binance's MPC is actually more of a factor of the existing technical system (in fact, MPC has significant limitations in multi-chain expansion). With the introduction of Tee, users need to encrypt and transmit a shard from their local device to Tee. As for OKX, it is the user's own local mnemonic phrase that is encrypted and transmitted to Tee.
As a user, there is no need to worry too much about the security risks here. Currently, the reliable communication between Tee and the client is very mature, theoretically completely eliminating man-in-the-middle attacks. After all, as long as the public key made public by Tee is used for asymmetric encryption, only the private key can decrypt it.
There are also some differences in detailed experiences, such as how long the MPC and private keys are valid in Tee, how to renew them, etc. These are engineering issues, so I won't elaborate on them.
Analyzing its design motivation, the main benefit of such a design is still migration costs, avoiding the cold start problem of users needing to migrate assets to experience new advanced features.
For example, cb's set is focused on the payment track, allowing traditional e-commerce service providers without local private key management experience to complete on-chain operations through APIs.
Moreover, Binance's system combines to operate in the Cedefi track, allowing users who typically look at K-lines to more easily navigate similar pages to directly purchase on-chain assets, while ignoring gas, slippage, multi-chain, and other issues.
5. Summary
How to evaluate the year 2025, and how to view the future?
I believe this year is a year of silence for wallets, as well as a year of transformation. It hasn't made much noise, but it has been quietly doing significant things.
In today's multi-chain environment, simply creating a user-friendly tool is no longer sufficient to sustain a large-scale wallet team (along with the necessary foundational setup). It definitely needs various value-added services to provide support, and this year just happens to be an explosive year for applications, with the perps track emerging and thriving, RWA (stock direction), prediction markets, and payments all showing improvements.
The market is gradually shifting from heavy memes to diversified DEX demands.
Moreover, memes are only perceived as fast transactions with high turnover amounts, giving the impression of a large market. In reality, the same group of people has always been playing, and the hot spots are changing, but user growth is not significant.
When combined with various Tee enhancements, each exchange's reputation has led to their respective new custody systems.
Moreover, on a larger trend, AI will become increasingly powerful, and AI trading will also grow, while previous wallets were only prepared for human use, not for AI.
Therefore, what I see is that next year, applications will experience even richer explosions, as the underlying technology has matured. There will definitely be a gap period in between because this Tee setup is still a play for large exchanges. They are unlikely to easily open up external access like Coinbase.
Additionally, users' funds playing Dex is just one part of the user demand; there is a much larger number of users who simply want to earn some stable income. Combined with the various subsidies and various airdrops during the promotion period, along with an APY, they will be very satisfied.
And the CeDeFi products that can benefit from on-chain returns will be the first landing place for many Cex users (to clarify, what is mainly mentioned here is CeDeFi with independent addresses, such as Bitget; shared addresses cannot benefit).
Finally, this year has seen significant advancements in cryptographic technology, and while this article does not cover it, increasingly more public chains like Ethereum and Solana have gradually integrated the R1 curve (which is the default support for device passkeys) through pre-compiled contracts. Thus, wallets incorporating passkeys are also a foreshadowing (although their recovery and cross-device synchronization are difficult to manage), which is why there are not many good applications yet.
After all, any product that can simplify high-frequency needs will eventually have a place.



