Background
On October 14, 2025, the U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC), the Financial Crimes Enforcement Network (FinCEN), and the UK Foreign, Commonwealth & Development Office (FCDO) took the largest coordinated sanctions action in history against cybercrime groups operating in Southeast Asia. This action not only sanctioned 146 individuals and entities linked to the 'Prince Group Transnational Criminal Organization (Prince Group TCO),' but also announced the seizure of 127,271 bitcoins (approximately 1.5 billion USD) associated with the Prince Group. Meanwhile, FinCEN designated the Huione Group, based in Cambodia, as a major money laundering entity, completely isolating it from the U.S. financial system.
Telecom fraud
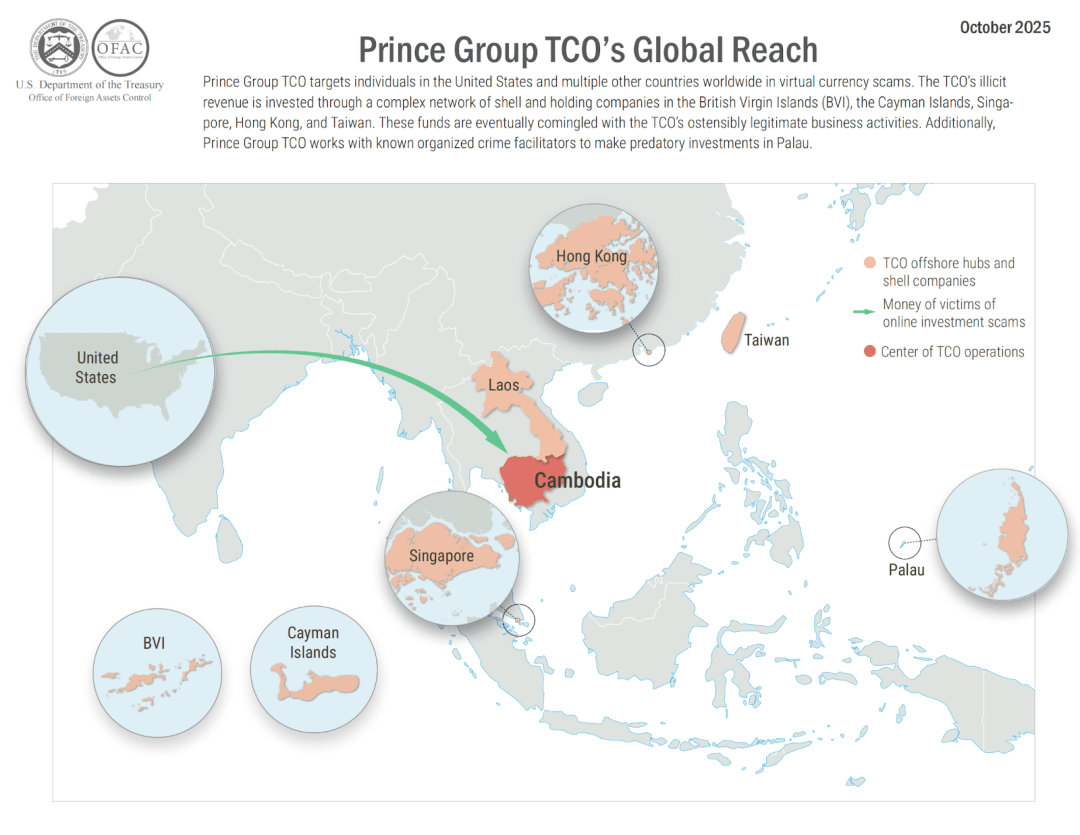
According to the indictment made public by the United States District Court for the Eastern District of New York, since 2015, the Prince Group, under the leadership of its founder and chairman Chen Zhi (also known as "Vincent"), has gradually developed into a vast network spanning more than thirty countries and controlling dozens of commercial entities. On the surface, the Prince Group operates legitimate businesses in real estate, finance, and consumer services, but in reality, its core profits come from transnational telecom scams and investment frauds implemented through forced labor. The group operates scam hubs in locations such as Cambodia, running cryptocurrency investment scams akin to the "pig butchering" model, with victims worldwide. According to estimates by the U.S. government, American citizens will lose at least $10 billion to Southeast Asian scams in 2024. These scams not only involve fraudulent investment websites and social engineering but are also closely linked to human trafficking, illegal detention, and forced labor, forming a systematic and industrialized underground economic chain.
Money laundering conspiracy
According to the indictment and FBI analysis, the Prince Group layered massive profits sourced from scams and illegal gambling through multiple channels, such as cross-border cash conversions, shell companies, fake bank accounts, and disguising as legitimate businesses, to disguise them as legal income.
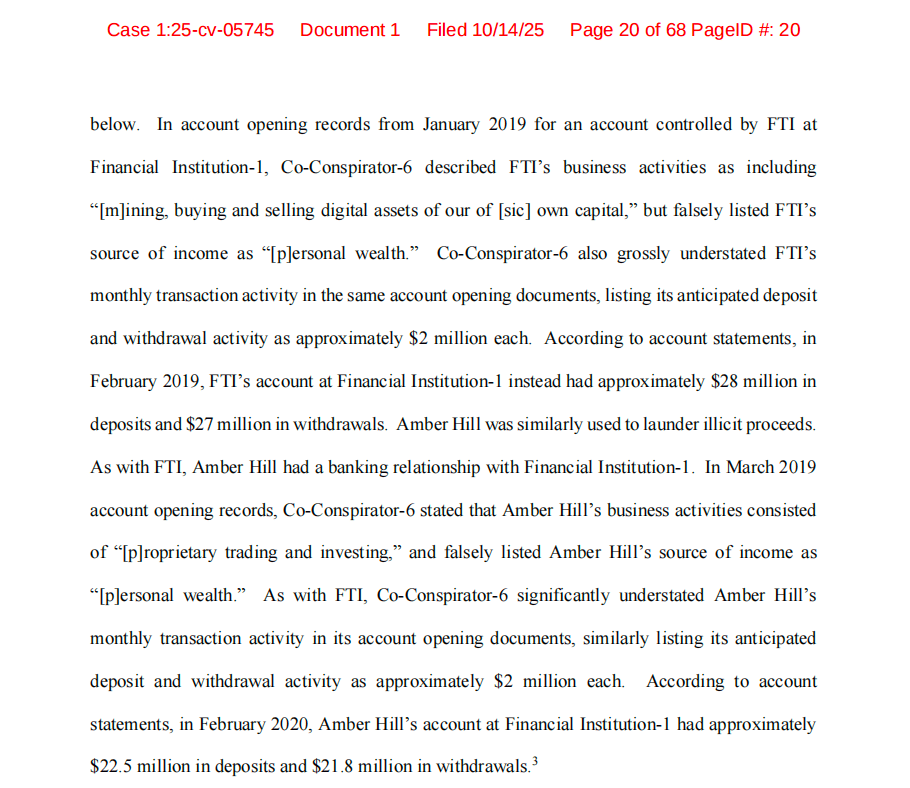
In the initial stages of fund conversion, the Prince Group uses a network of so-called "money laundering houses" or "underground banks"—these institutions receive the assets of scam victims (mostly Bitcoin or stablecoins) under the guise of "money service providers", then exchange them for cash through off-ramping, and subsequently use "clean" fiat currency to purchase new Bitcoin or other cryptocurrencies. For instance, the Brooklyn Network serves as the U.S. operational node for the Prince Group, where account managers provide seemingly legitimate investment portfolios during the scam process, inducing victims to continue investing, while in reality, these accounts are merely funding channels controlled by shell companies. The funds are then funneled back to the core accounts of the Prince Group in the form of cash or cryptocurrency. From approximately May 2021 to August 2022, the Brooklyn Network assisted the Prince Group in transferring and laundering over $18 million from more than 250 victims in the U.S.
To further obscure the trajectory of funds, the Prince Group established numerous shell companies (such as FTI, Amber Hil, and LBG) and funneled illicit funds into its "legitimate" business departments. Although Cambodia has banned online gambling since 2020, the Prince Group continues to operate in multiple countries, and internal ledgers even explicitly remind: "Employee salaries – please use clean money to pay"; another source of funding is cryptocurrency mining, wherein Chen Zhi invested illegal gains into Warp Data and Lubian mining sites. Investigations show that nearly 70% of the funds associated with the Lubian mining addresses did not come from newly mined Bitcoin but were mingled with cryptocurrencies from other sources.
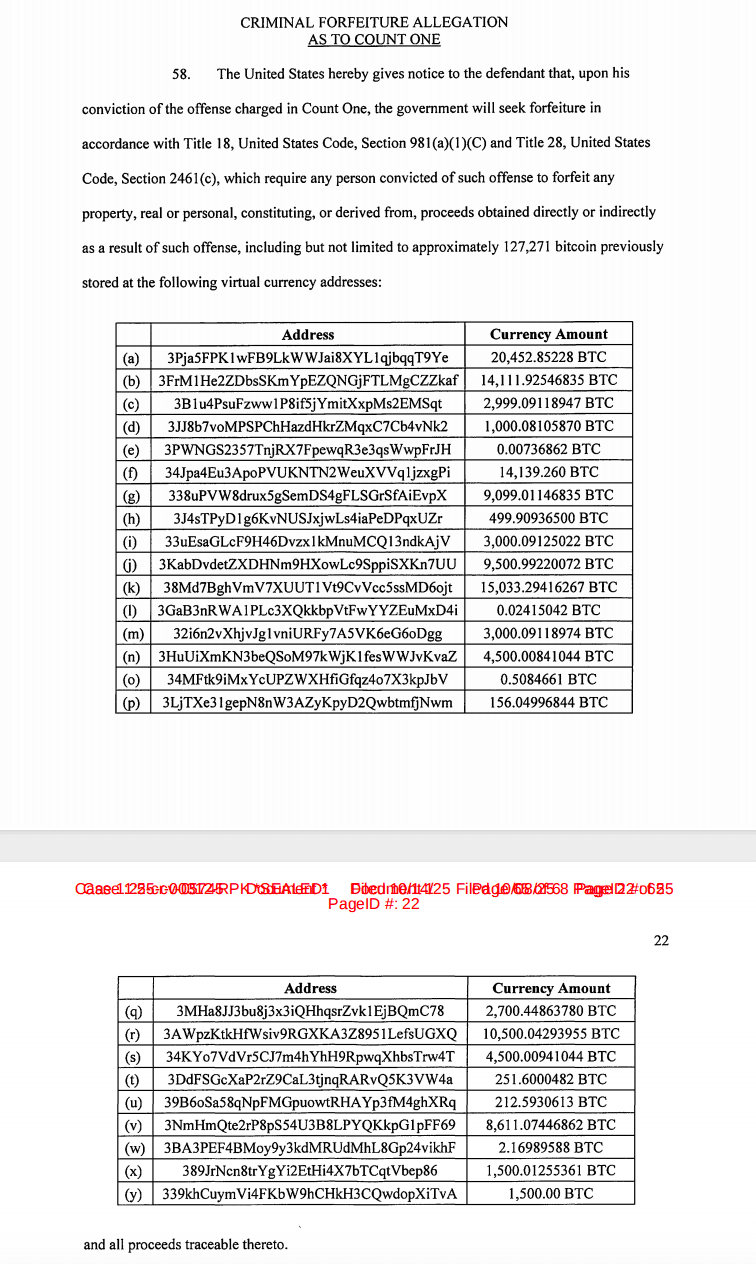
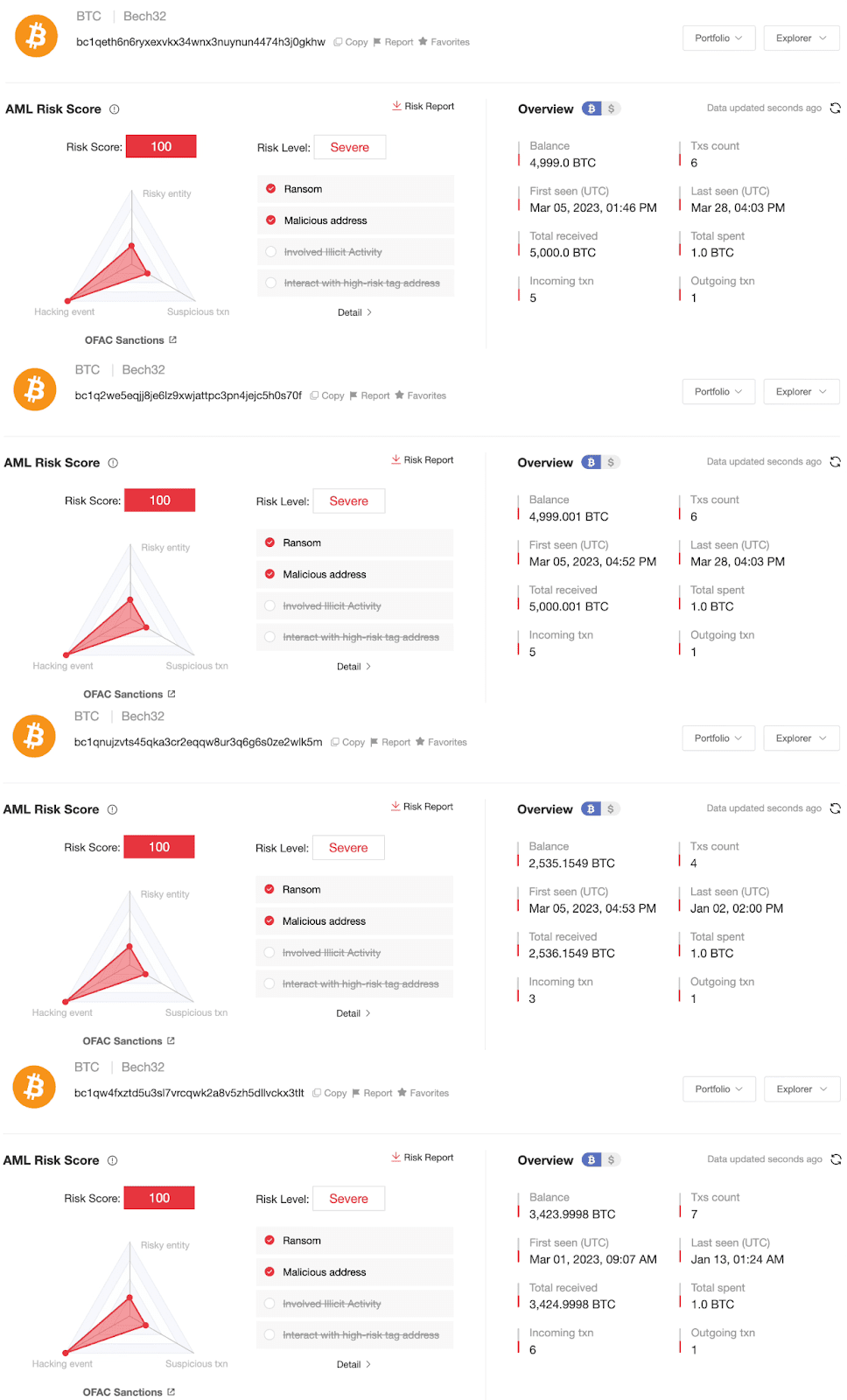
 The Prince Group also employs a range of specialized on-chain money laundering techniques—a "spray-funnel" model: by repeatedly splitting large amounts of cryptocurrency into dozens of wallets and then recombining them, they disrupt the on-chain tracking path. By around 2020, Chen Zhi had accumulated about 127,271 bitcoins in illegal wealth, which are dispersed across 25 non-custodial wallets he controls.
The Prince Group also employs a range of specialized on-chain money laundering techniques—a "spray-funnel" model: by repeatedly splitting large amounts of cryptocurrency into dozens of wallets and then recombining them, they disrupt the on-chain tracking path. By around 2020, Chen Zhi had accumulated about 127,271 bitcoins in illegal wealth, which are dispersed across 25 non-custodial wallets he controls.
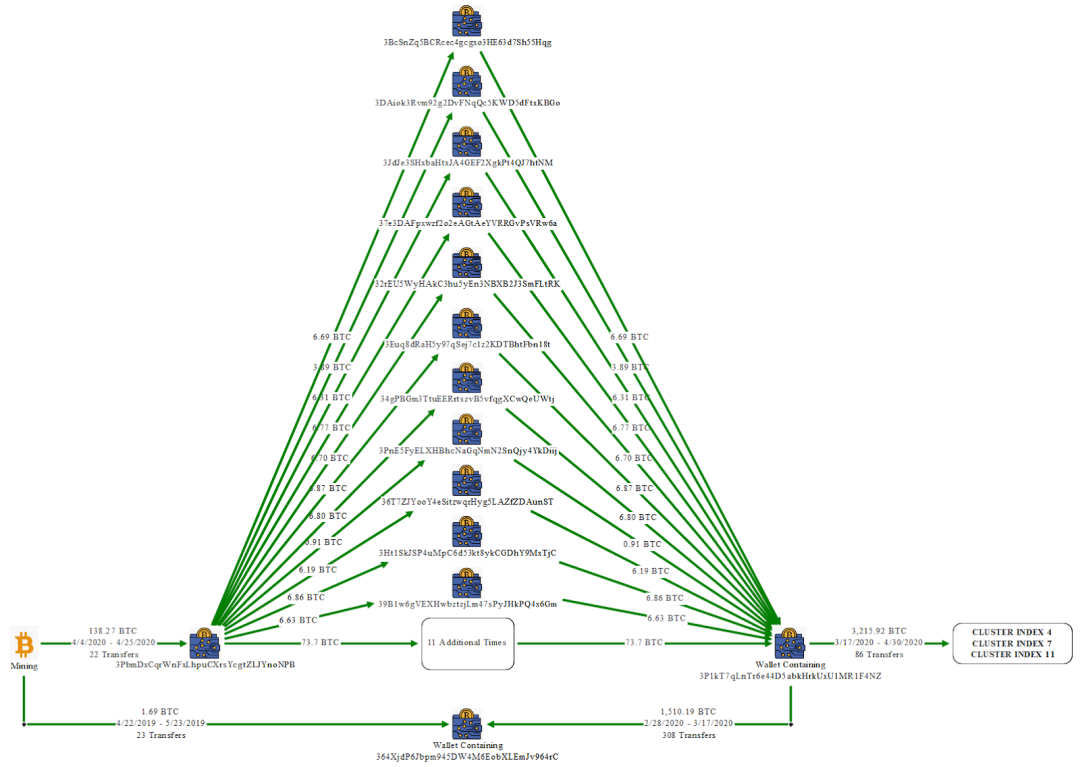
 In the indictment, the FBI classified these addresses into multiple clusters (Cluster Index 1–13), and the addresses within these clusters exhibited highly consistent patterns of fund flows, showing significant characteristics of money laundering behavior.
In the indictment, the FBI classified these addresses into multiple clusters (Cluster Index 1–13), and the addresses within these clusters exhibited highly consistent patterns of fund flows, showing significant characteristics of money laundering behavior.
 In this sanction action, four Bitcoin addresses directly controlled by Chen Zhi were listed by OFAC on the sanctions list:
In this sanction action, four Bitcoin addresses directly controlled by Chen Zhi were listed by OFAC on the sanctions list:
 According to analysis by the on-chain anti-money laundering and tracking tool MistTrack, these four addresses have been active since March 2023 and have received a total of 15,961.15 BTC, with each address only transferring 1 BTC to the next layer address.
According to analysis by the on-chain anti-money laundering and tracking tool MistTrack, these four addresses have been active since March 2023 and have received a total of 15,961.15 BTC, with each address only transferring 1 BTC to the next layer address.
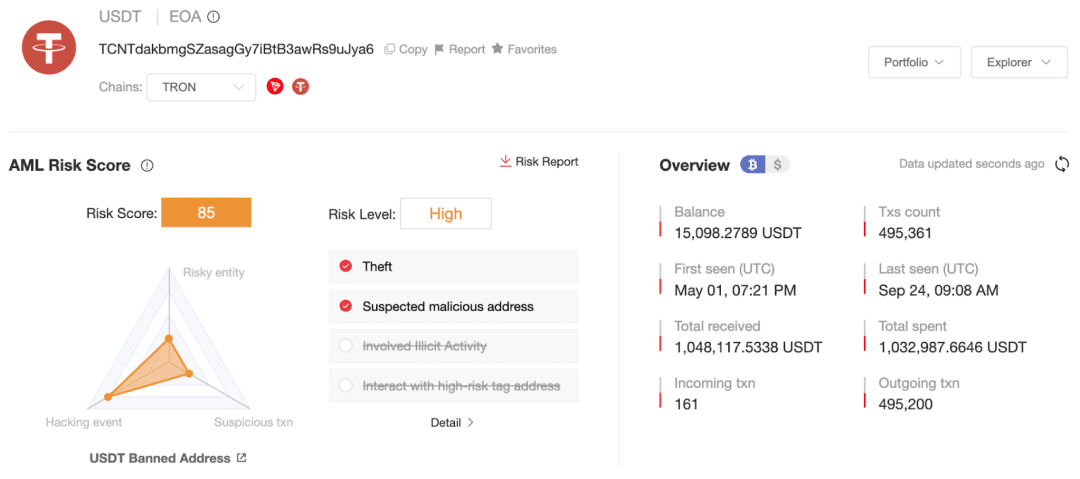
 Also located in Cambodia, Huione Group (汇旺集团) was identified as a major money laundering institution in this action. The U.S. Department of the Treasury's Financial Crimes Enforcement Network (FinCEN) also issued the final rule under Section 311, isolating Huione Group from the U.S. financial system. In addition, the United Nations Office on Drugs and Crime (UNODC) pointed out in a report in May 2025 that Huione Guarantee has become part of Southeast Asia's "industrialized ecosystem of online fraud," with its platform having received over $24 billion in encrypted funds cumulatively. Previous statistics from SlowMist also indicated that from January 1, 2024, to June 23, 2025, the total deposit and withdrawal amount of HuionePay exceeded $50 billion USDT, showing a continuous influx and outflow of large amounts of funds over the past year and a half.
Also located in Cambodia, Huione Group (汇旺集团) was identified as a major money laundering institution in this action. The U.S. Department of the Treasury's Financial Crimes Enforcement Network (FinCEN) also issued the final rule under Section 311, isolating Huione Group from the U.S. financial system. In addition, the United Nations Office on Drugs and Crime (UNODC) pointed out in a report in May 2025 that Huione Guarantee has become part of Southeast Asia's "industrialized ecosystem of online fraud," with its platform having received over $24 billion in encrypted funds cumulatively. Previous statistics from SlowMist also indicated that from January 1, 2024, to June 23, 2025, the total deposit and withdrawal amount of HuionePay exceeded $50 billion USDT, showing a continuous influx and outflow of large amounts of funds over the past year and a half.
FinCEN stated that Huione Group laundered at least $4 billion between August 2021 and January 2025, which includes:
At least $37 million comes from North Korea-related cyber theft;
At least $36 million comes from cryptocurrency investment fraud;
About $300 million comes from other cyber crimes.
According to FinCEN's final rule under Section 311, all U.S. regulated financial institutions are prohibited from opening or maintaining correspondent accounts for Huione Group, nor may they process any cross-border transactions for it, thereby preventing Huione Group from indirectly entering the U.S. financial system.
After the announcement of the sanctions actions, some exchanges, such as OKX, publicly stated that they would implement strict control measures against Huione.
Anti-money laundering recommendations
In the current regulatory ecosystem, on-chain money laundering, online fraud, and high-risk capital flows are no longer just issues for regulators or institutions to focus on; they are directly impacting every practitioner of crypto assets.
For practitioners, even inadvertently coming into contact with sanctioned addresses or funds related to illicit activities may lead to account freezing or asset seizure. Therefore, it is recommended that practitioners use on-chain tracking tools (such as MistTrack) to conduct real-time screening of counterparty addresses before receiving or transferring digital assets, understand their historical transaction behavior and potential risks, and confirm whether the source of funds is clear and reliable, avoiding the acceptance of assets from sanctioned wallets, known high-risk addresses, or suspicious transaction pathways.
For businesses, exchanges, service providers, and other project parties, KYC/KYT is no longer an "optional question". If they inadvertently engage in business with high-risk entities, they may face joint liability risks. They not only need to verify the identity of customers (KYC) but should also track the flow of funds through on-chain transaction monitoring (KYT) to identify potential high-risk addresses, sanctioned entities, and suspicious funds, ensuring that businesses and exchanges do not get involved in illegal transactions.
Based on years of blockchain security research and risk control practices, SlowMist's anti-money laundering tracking analysis system MistTrack has provided stable and reliable on-chain risk control support and robust AML compliance solutions for numerous exchanges and enterprises, as well as accurate data analysis, real-time risk monitoring, and comprehensive compliance support for individual users, corporate teams, and developers. MistTrack can detect the source of funds, screen whether the funds come from sanctioned wallets or high-risk addresses, and avoid receiving tainted funds; it can also provide real-time risk control, conducting address reviews before transactions to avoid dealings with sanctioned addresses or suspicious funds, thus reducing the possibility of freezing. Currently, MistTrack has accumulated over 400 million address tags, over a thousand entities, more than 500,000 threat intelligence data points, and over 90 million risk addresses, providing solid support for digital asset security and combating money laundering crimes. For more information, please visit https://aml.slowmist.com.
Relevant links:
https://home.treasury.gov/news/press-releases/sb0278
https://ofac.treasury.gov/recent-actions/20251014
https://www.justice.gov/usao-edny/media/1416266/dl


