A cryptocurrency trader has just suffered a loss of nearly 50 million USD after falling victim to an address poisoning attack - a seemingly simple scam that continues to ensnare even the most experienced users. The incident quickly attracted the attention of the community when the victim publicly offered a reward of 1 million USD for anyone who assists in recovering a large portion of the stolen funds.
A 26-minute mistake and a price tag of tens of millions of dollars.
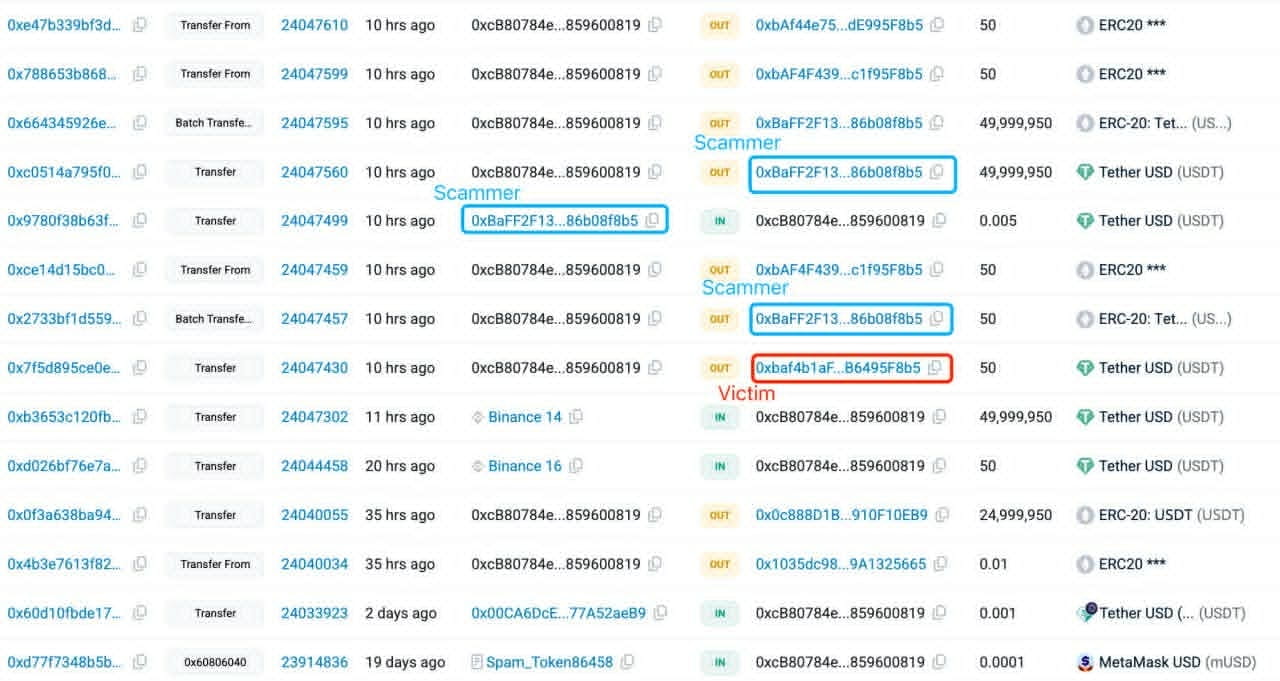
A trader has just suffered a loss of nearly $50M after becoming a victim of an address poisoning attack. Source: Lookonchain.
According to the on-chain analytics platform Lookonchain, the incident occurred on December 20 when the victim transferred 49,999,950 USDT to an address controlled by the scammer. Previously, this trader had withdrawn funds from Binance and intended to transfer assets back to a personal wallet.
As many cautious crypto users still do, the victim made a test transaction of 50 USDT to verify the receiving address. However, this seemingly safe step opened up an opportunity for the attacker.
How does the address poisoning mechanism work?
According to blockchain security companies, the attacker used an automated script to create a fake wallet address that closely resembled the victim's real address. Specifically, the malicious address had the first 5 characters and the last 4 characters identical to the legitimate address, differing only in the middle characters.
Due to many crypto wallets shortening addresses with '...' for easier viewing, this difference is very hard to detect with the naked eye. After creating the fake address, the attacker sent small transactions from that address to the victim's wallet to 'poison' the transaction history.
When the victim returned to copy the address from the transaction history to execute a transfer of nearly 50 million USDT, they inadvertently selected the wrong fake address.
Data from Etherscan shows that the test transaction took place at 3:06 UTC, while the transaction that mistakenly transferred the entire amount occurred just 26 minutes later, at 3:32 UTC.
Rapid money laundering through DAI, ETH, and Tornado Cash.
Immediately after receiving the USDT, the attacker acted extremely quickly. According to the security company SlowMist, within just 30 minutes, the entire amount of USDT was swapped for DAI through MetaMask Swap.
This move is considered calculated, as USDT can be frozen by Tether if flagged, while DAI is a decentralized stablecoin, lacking similar centralized control mechanisms.
Subsequently, the DAI was converted into approximately 16,690 ETH, of which 16,680 ETH was sent to Tornado Cash - a mixing tool that was previously sanctioned by the US to obscure transaction traces and complicate tracking processes.
Offering a reward of $1 million, turning to law enforcement.
In an effort to recover assets, the victim sent a direct on-chain message to the attacker, offering a whitehat bounty of $1 million in exchange for the return of 98% of the stolen funds.
The message also stated that the victim has officially filed a criminal lawsuit while coordinating with law enforcement, cybersecurity companies, and various blockchain protocols to gather information about the attacker.
However, the possibility of asset recovery remains a big question, especially as most of the money has been funneled into Tornado Cash.
Address poisoning is no longer an isolated phenomenon.
This incident recalls a similar incident in May 2024, when an Ethereum user lost $71 million in wrapped bitcoin due to address poisoning. In that case, most of the assets were recovered after on-chain negotiations with the assistance of blockchain security companies.
However, not every case has a positive outcome, especially when the attacker acts quickly and uses powerful anonymity tools.
In 2025: Crypto continues to be a 'juicy target' for hackers.
According to warnings from Jameson Lopp, co-founder of Casa, address poisoning attacks are increasing across multiple blockchains. Specifically for Bitcoin, approximately 48,000 suspicious incidents have been recorded since 2023.
Meanwhile, Chainalysis reported that the total losses from hacks and crypto fraud in 2025 exceeded $3.4 billion, an increase from 2024. Notably, the hack of the Bybit exchange in February, with $1.4 billion stolen - believed to be carried out by North Korean hackers - accounted for nearly 44% of the total annual losses, and was described by Elliptic as 'the largest crypto theft in history.'



